Chrome 71 stomps on abusive advertising
Google shipped version 71 of its Chrome browser earlier this week, alongside fixes for 43 security issues. The latest Chrome version also introduces several new security measures.
Perhaps the biggest new security feature in Chrome is its anti-abuse technology, which focuses on ads that deliberately mislead users. These sites use a range of techniques such as presenting buttons that purport to do one thing like playing video or closing a window, but which actually do another like opening advertising windows.
Such sites are also known to use fake chat messages, transparent areas that are clickable without the user’s knowledge, auto-redirects without user interaction, and ads that use fake moving mouse cursors to try and make users click on a certain area. Scammers and phishers sometimes use these techniques to steal personal information, the company said.
Google is stepping up the anti-abuse measures that it launched last year by identifying sites that persist in using these abusive techniques to serve ads, and blocking advertising from them altogether. Site owners will get a 30-day warning.
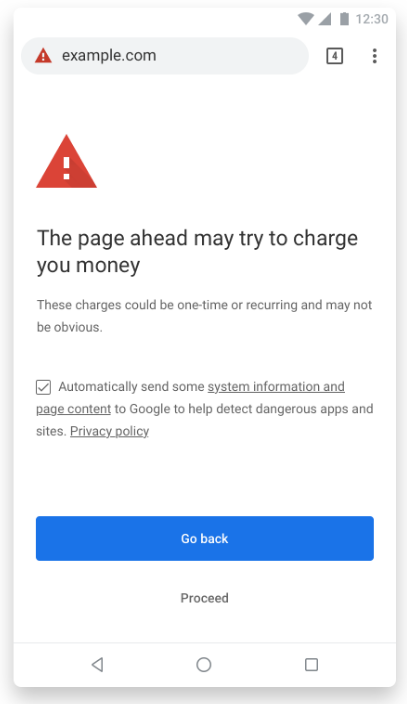
Another anti-abuse measure focuses on mobile subscription sites. These are websites that invite users to enter their phone number in return for some service. The fee then shows up as a subscription on their mobile phone bill. In many cases, these payment forms represent a legitimate way to pay. Some sites abuse the feature, though, by misleading users about how much they can expect to pay, or whether they will be charged at all.
Chrome 71 identifies these sites and then warns users before they visit them:
Generally, sites can avoid getting this warning by following Google’s best practices for mobile billing. If their sites get hit with a warning screen, Google will do its best to let them know about it, using its Search Console service if the site is registered there. The owner can then make the necessary changes and appeal to have the warning removed.
Chrome 71 will also no longer allow websites to speak to users unless the user interacts with the loaded site first. This will stop sites abusing the speech API by trying to persuade unwitting users to do things. Google had already implemented restrictions on autoplaying for all its other Chrome APIs, but the capability remained as a bug, first reported in February. Chrome 71 will follow similar rules as part of its autoplay policy for web audio, mirroring those already introduced for other content in Chrome 66.
With version 71, Google is also removing the inline installation feature which allowed users to install browser extensions on sites other than the official Chrome web store. This makes it more difficult for bad actors to cajole users into installing malicious extensions.
Google had already begun restricting inline installation in Chrome, making it unavailable for all newly-published extensions from June onward and disabling it for existing extensions in September. This latest release strips out the code within Chrome that allowed inline installations altogether.
These security improvements are the latest of many introduced by Google this year which has also seen the company roll out new rules for extension developers and a native password generator.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/CTVnwwU2MyQ/