Parents slam “weirdo” fraudsters for using child’s Facebook pic for cash
Did you see that viral post showing an adorably glowering kid posing for his school portrait last week? He’s got his hands in the pockets of his pink pants in one photo, he’s sitting in front of a container full of fake grass in another, and he’s just staring balefully straight at the camera in a third.
So what’s with the sour face? Does he hate pink? Did he get teased?
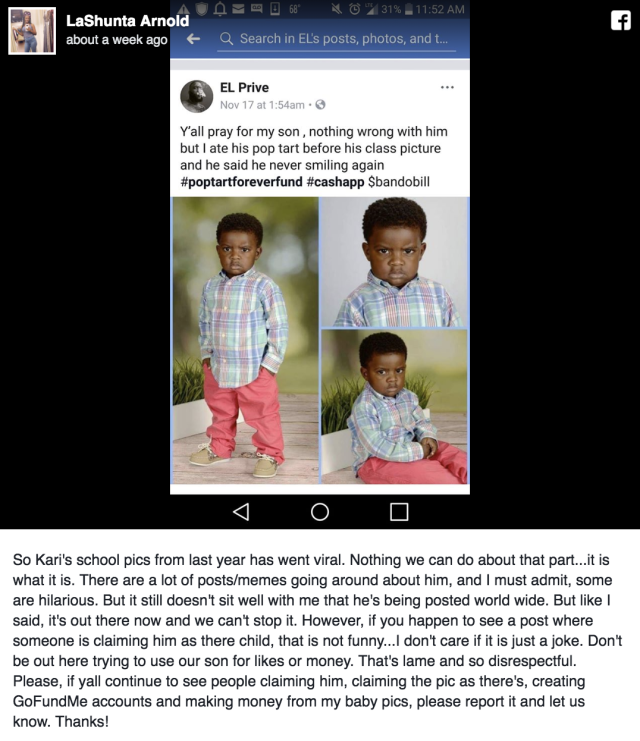
No, said “El Prive,” there’s nothing wrong with his “son.” It’s just that he ate the last Pop-Tart, and the boy said he’d never smile again. And, of course, #poptartforeverfund #cashapp $bandobill.
#SimplyAdorbs! Within two days, the post was reportedly shared more than 156K times and had garnered well over 40K comments.
…And then the boy’s real parents weighed in. Last Monday, the lad’s mom put up a post saying – Hey, #ThatIsn’tYourSon and #Don’tUseOurSonForLikesOrMoney.
And thus was set off Pop-Tart-gate.
A woman named Tantarnea Arnold who goes by the name of LaShunta on Facebook posted about El Prive – who the Daily Mail identified as Bill Muhammad and whose Facebook page identifies as Bandobill™:
So Kari’s school pics from last year has went viral. Nothing we can do about that part…it is what it is. There are a lot of posts/memes going around about him, and I must admit, some are hilarious. But it still doesn’t sit well with me that he’s being posted world wide. But like I said, it’s out there now and we can’t stop it. However, if you happen to see a post where someone is claiming him asthere child, that is not funny…I don’t care if it is just a joke. Don’t be out here trying to use our son for likes or money. That’s lame and so disrespectful. Please, if yall continue to see people claiming him, claiming the pic as there’s, creating GoFundMe accounts and making money from my baby pics, please report it and let us know. Thanks!
At this point, given that we shouldn’t blindly trust anything we read on the internet, we should be questioning whether Ms. Arnold is, in fact, the true mother of the furrowed-brow tot, and for that matter, whether the kid in the photo is really somebody named Makari Arnold. But given that her Facebook profile and photos are publicly accessible, and that multiple photos on her page depict a (smiling!) child who looks like the child in the viral post, we can grant her the benefit of the doubt and assume that she’s on the up and up.
The boy’s father, Michael Arnold, also posted about the pictures, asking:
What type of weirdo claims somebody else son?
If yall see any go fund me accounts @ me or report.
Two days after Ms. Arnold aired her indignation, Bandobill™ claimed that he’d lost his job over the incident.
LOST my job over misunderstanding and numerous calls to my corporate office for accusations of fraud… and being on news…. mission accomplished people
Y’all so tight
It’s just a JOKE, people, he said, no harm intended, and many commenters agreed with him. Others said this was no “misunderstanding”… not given that he includes a Cash App request.
What’s the misunderstanding? You don’t post someone else’s kid without their permission. You def don’t put your cash app on that pic like you need money for the kid. That looks like fraud.
Cash App is a mobile payment app that lets users transfer money to each other using a mobile phone. Muhammad claimed that only $23.52 was raised and will go to a Kentucky homeless shelter, on top of another $200 from his own pocket.
Why were his photos publicly posted to begin with?
On Monday, Tantarnea Arnold said that the photos were taken last year at her son’s daycare center. She said that a cousin had posted the photos and that they subsequently went viral.
People like to share photos of their kids online. Even if they don’t, their friends and family are happy to step in and do it in their stead. Back in 2013, we asked readers whether they thought that posting photos of your kids online makes you a bad parent.
Nearly 72% said “No, but I am careful about what information I post about my children.”
That caution is encouraging, but we have to put it into perspective: people who read blogs about information security such as Naked Security would of course tend to be more informed than the general population about the potential harm of sharing photos.
What potential harm? Well, as the Arnolds can certainly attest, it doesn’t feel good to have your child’s photo used in somebody else’s joke, be it a non-malicious one or one that’s designed to rip people off. Also in the “that’s creepy” realm, we’ve seen online role players photo-nap kids and list them for “adoption.” Pedophiles, of course, photo-nap kids for their own use. And misery can also come from being teased by cyberbullies or being tormented over the images by schoolmates.
In spite of such potential dangers, we’re still sharing photos of children (and of others who are powerless to protest, such as the elderly or the unconscious, intubated or sedated) at a furious clip.
Experts say that on average, by the age of 13, parents have posted 1,300 photos and videos of their child to social media. According to a report published earlier this month by the UK’s Children’s Commissioner that looked into the collection and sharing of children’s data, the photo dump explodes when children themselves start posting online: on average, children post to social media 26 times per day for a total of nearly 70,000 posts by the time they reach the age of 18.
While we’re aware of the short-term dangers that can come from children’s photos falling into the wrong hands, it’s still too early to discern the dangers that can arise long-term, after a lifetime of children’s images and personal data being amassed from social media, smart toys and other connected devices, the Children’s Commissioner said:
This is not just about parents and children sharing information on social media, even though that is part of the issue. It is also increasingly about smart toys, speakers and other connected devices which are being brought into more and more homes. It is about the proliferation of monitoring equipment that parents can buy, from pedometers to location tracking watches. And it is about information that is given away when children use essential public services such as schools and GPs – something which they might have very little control over. Children are being “datafied” – not just via social media, but in many aspects of their lives.
Beyond stranger danger, will this lead to Big Data applications in the future? Will information about your 4-year-old somehow influence their future college application? Will their personal health data affect their ability to take out insurance in the future?
Time will tell.
In the meantime, Makari’s photos have had more than a year to spread far and wide, and there’s no way the Arnolds can ever get them back. What they can do: try to limit the audience for their photos and, thereby, (hopefully) stop other photos of their two children from being used in similarly offensive ways. Here’s how:
How to limit the audience of past Facebook posts
- Click the down arrow at the top right of any Facebook page and choose Settings
- Select Privacy from the menu on the left-hand side
- Under Your activity, click Limit the audience for posts you’ve shared with friends of friends or Public?
- Click Limit Past Posts
How to lock down the privacy of your future Facebook posts
- Click the down arrow at the top right of any Facebook page and choose Settings
- Select Privacy from the menu on the left-hand side
- Under Your activity, click Who can see your future posts?
- Here you can choose to limit the posts to Friends only, or a custom list of people you choose.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/7eFuqf1JNFA/