On Tuesday, Nicola Brookes told Naked Security, she received a Christmas card in the post, sent to her home address.
On Tuesday, Nicola Brookes told Naked Security, she received a Christmas card in the post, sent to her home address.
On the front of the card was a picture of a dog. The message wished Happy Christmas To A Dog.
Inside the card, she found a large photo of herself, in the hospital, eyes closed, with tubes taped to her throat, nose and temple. The picture had been scraped from her daughter’s Facebook posts regarding Ms. Brooke’s emergency surgery for Crohn’s disease.
The image of a “Get Well Soon” balloon was pasted over the photo.
That might not seem like a terribly vicious troll attack. After all, the image included a “get well” message.
But besides the obvious pejorative of calling its recipient a dog, the card did a number of things.
First, it presented further evidence of known facts: namely, that a troll or trolls had published Ms. Brookes’s home address online, that they had scraped personal photos to use in attacking her, and that they’d been following people close to her.
The card also must be placed in the context of preceding troll-crafted images to appreciate its malevolence.
One such: Ms. Brookes’s face is pasted over the image of a woman, on the floor, hogtied, with her hands tied behind her back, her feet tied together, one end of the rope tied around her neck in such a way that she would, eventually, tire of keeping her legs elevated, relax, and thereby strangle herself to death.
The woman in the photo is surrounded by troll dolls. The caption: “TROLL RAPE: You never even saw it coming”.
She claims to have received much worse images than that. Naked Security have been shown the images. They are even more abhorrent than the troll rape one, so we’ll refrain from describing them.
Not that any of this is new, mind you. It’s been going on for over two years.
During that time, since posting a message of support for another troll victim, Ms. Brookes has been the subject of many headlines for stories about internet trolls.
Many of these headlines had a feel-good tone: they often trumpeted a “victory over cyber bullies“, given a landmark case in which Ms. Brookes forced Facebook to reveal her trolls’ names, email addresses and IP addresses.
It has turned out to be anything but a victory. Her torment has continued unabated.
An active UK policeman, Lee Rimell, was arrested in connection with the abuse, which included website hate pages: one about Brookes’s Crohn’s disease, and another falsely labeling her a paedophile and a drug dealer.
One Facebook clone account sent suggestive messages to young girls in her name.
The charges resulted in an investigation by the Crown Prosecution Service (CPS), who subsequently decided that PC Rimell shouldn’t face criminal charges.
In fact, the CPS apparently figured that Ms. Brookes was at least partially to blame, given that she had the audacity to talk back to the trolls.
A quote from CPS, courtesy of the BBC’s coverage:
“You engaged with the ‘trolls’ contrary to the specific advice given to you by Sussex Police on at least three occasions.”
For what it’s worth, Ms. Brookes denies that Sussex Police ever gave her that advice at all, let alone told her three times.
But little does it matter, given that police figured they didn’t have much to go on.
That was largely because, Brookes told us, according to investigators, Rimell had his PC “reconditioned” in July of 2012, just a few weeks before his arrest.
This “reconditioning”, the investigators told Brookes, destroyed the hard drive history and all digital, forensic evidence off his PC. Therefore, Brookes said, when investigators seized and examined Rimell’s PC, they couldn’t find evidence of abuse with which the CPS could charge him.
Police wouldn’t confirm or deny that an investigation summary letter detailing the “reconditioned” PC originated from CPS, but here’s an excerpt from the letter that Brookes claims they sent her in October:
Lee Rimmell [sic misspelled surname in all instances] was arrested and interviewed in respect of the allegation that your Hotmail account was hacked into. The computer which was seized and examined by the Police was shown to be reconditioned in July 2012. This post-dates the offence. Lee Rimmell denied the offence and stated that his account was hacked into. He further intimated that it was possible that this person also hacked into your account from his account. The Police inform me that they contacted an expert who confirmed that it is possible for another individual to access and use Lee Rimmell’s IP address to hack into your account. We are at a disadvantage as Lee Rimmell’s computer for the relevant period is no longer available and cannot be examined. There is therefore insufficient evidence on the material provided to us to prove that Lee Rimmell was responsible for hacking into your computer.
All of this is just part and parcel of a dragged-out ordeal, which has included Ms. Brookes dismissing her pro bono legal counsel, alleging malpractice; and the police’s claims, according to Brookes, that she didn’t file a complaint months ago, which has sent her back to square one.
So no, PC Rimell won’t be facing criminal charges, and a civil suit may be unlikely, given the enormous amounts of money involved to file and to conduct computer forensics—money Ms. Brookes doesn’t have.
Instead, Rimell on Tuesday attended what’s called a “Misconduct Meeting” in regards to alleged breaches of the police’s Standards of Professional Behaviour.
At that meeting, evidence to support the misconduct allegation was to be presented from Sussex Police, including Rimell’s admission that he sent such messages, albeit “claiming he didn’t intend such consequences,” according to an email that Naked Security has seen that was sent by Adrian Taylor, Detective Inspector for the West Midlands Police Professional Standards Department.
At the end of the meeting, Rimell was given the harshest possible penalty for a Misconduct Meeting. Namely, he was given a warning.
A “Final Written Warning,” that is.
This will be placed on PC Rimell’s personal file and will remain live for eighteen months from Thursday, 5 December. Further misconduct (that justifies more than management advice) will result in dismissal in all but unspecified “exceptional circumstances,” at which point the slap on the wrist “final” warning may extend to yet another 18 months, but “on one occasion only”.
To sum it all up: A UK police officer was arrested. He admitted to abusive content. He got off with a warning. Whilst this was going on troll abuse of the victim skyrocketed.
Ms. Brookes does not believe that receiving a troll’s Christmas card two days before PC Rimell’s hearing amounts to merely a coincidence, but who can prove otherwise, given how proxies cover proxies that shield proxies behind which hide cowardly people, and given how expensive court filings and digital forensics are, and given how little training police receive in investigating these matters?
As The Independent reported in late November, the national stalking advocacy service Paladin reports that less than a third of UK police officers have received training on a new stalking law, despite its implementation a year ago.
Out of 320 people arrested in the first six months under the new law in England and Wales, only 189 have been charged, while 27 received a conviction and only six served jail time, The Independent reports.
The UK police have refrained from giving details about just what it is that Rimell did to earn this “Final Written Warning.” All we can say for sure is that he carried out online activities which merited the most severe of four outcomes of a misconduct hearing.
That alone, however, might be construed as being enough to question whether he is in the correct line of work, given that the taxpayers of the UK are keeping him on the payroll as a public protector whose sole and express role is to help prevent abuse.
Brookes is one example of law enforcement’s failure to proactively, swiftly shut down and investigate online abuse, as she told me:
It took six months before police would open a case. My solicitors for months wrote letters, since 2011, trying to force police to investigate what’s happening. They just wouldn’t.
Meanwhile, Ms. Brookes believes that the advice being handed out to victims – “don’t engage cyber bullies,” for example – is a joke:
In the beginning, I answered them back. I felt I had every right to defend myself at the time.
She also relates to cyber-bullying victims who take their own lives, she said:
I can completely understand [teen suicides]. I had very, very low days. Very low.
The advice going on, [victims find ourselves] just screaming and shouting at the TV and our monitors, saying ‘We do all that anyway.’ They still get to us. The police are completely uneducated. They don’t have the training or resources to tackle this problem. They don’t have a bl**** clue what they’re doing.
We like to end our reports with useful advice for our readers but that is a difficult thing to do when Nicola Brookes’s story has shown the stark limitations of “don’t engage”.
It’s not that easy. Clearly it’s not that easy but until we find a better solution it remains the best advice even though following it is, as Ms Brookes has discovered, very far from a guarantee of success.
Equally we encourage victims not to be put off from reporting the abuse they suffer at the hands of trolls to the appropriate law enforcement agency. If you want to know how then read our guide on how to report a computer crime: Trolling.
Nicola Brookes is disappointed, angry and still being abused, and today she reported the sinister Christmas card to the Sussex police. She told us the police are dealing with it as a new offence that is unconnected with the previous 2 years of abuse and that because they don’t anticipate getting any useful forensic evidence from the envelope it is doubtful that the matter will be taken any further.
Image of tablet courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/txl-NdcORRY/
 It’s Patch Tuesday this week – the last one, indeed, for 2013, the year in which we celebrated the tenth anniversary of Microsoft’s formularised process for security updates.
It’s Patch Tuesday this week – the last one, indeed, for 2013, the year in which we celebrated the tenth anniversary of Microsoft’s formularised process for security updates. On Tuesday, Nicola Brookes told me, she received a Christmas card in the post, sent to her home address.
On Tuesday, Nicola Brookes told me, she received a Christmas card in the post, sent to her home address. The powers that be won’t let US President Barack Obama use an iPhone because of security reasons, he told a group of young people while pitching his signature healthcare law at the White House.
The powers that be won’t let US President Barack Obama use an iPhone because of security reasons, he told a group of young people while pitching his signature healthcare law at the White House. We’ve written several times recently about the problems we face – whether as consumers, programmers, vendors or users – from
We’ve written several times recently about the problems we face – whether as consumers, programmers, vendors or users – from 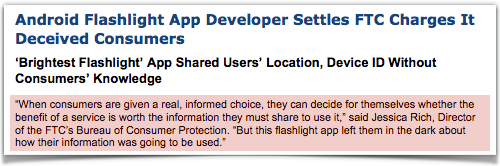
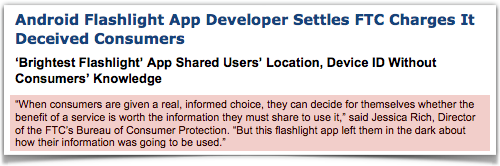
 On Tuesday, Nicola Brookes told Naked Security, she received a Christmas card in the post, sent to her home address.
On Tuesday, Nicola Brookes told Naked Security, she received a Christmas card in the post, sent to her home address. We’ve written several times recently about the problems we face – whether as consumers, programmers, vendors or users – from
We’ve written several times recently about the problems we face – whether as consumers, programmers, vendors or users – from