REDMOND, Wash., Dec. 5, 2013 /PRNewswire/ — The Microsoft Digital Crimes Unit today announced it has successfully disrupted a rampant botnet in collaboration with Europol’s European Cybercrime Centre (EC3), the Federal Bureau of Investigation (FBI) and leaders in the technology industry, including A10 Networks Inc. The Sirefef botnet, also known as ZeroAccess, is responsible for infecting more than 2 million computers, specifically targeting search results on Google, Bing and Yahoo search engines, and is estimated to cost online advertisers $2.7 million each month. Today’s action is expected to significantly disrupt the botnet’s operation, increasing the cost and risk for cybercriminals to continue doing business and preventing victims’ computers from committing fraudulent schemes.
(Logo: http://photos.prnewswire.com/prnh/20000822/MSFTLOGO)
This is Microsoft’s first botnet action since the Nov. 14 unveiling of its new Cybercrime Center — a center of excellence for advancing the global fight against cybercrime — and marks the company’s eighth botnet operation in the past three years. Similar to Microsoft’s Citadel botnet case, the ZeroAccess case is part of an extensive cooperative effort with international law enforcement and industry partners to dismantle cybercriminal networks and ensure that people worldwide can use their computing devices and services with confidence.
“This operation marks an important step in coordinated actions that are initiated by private companies and, at the same time, enable law enforcement agencies around Europe to identify and investigate the criminal organizations and networks behind these dangerous botnets that use malicious software to gain illicit profits,” said Troels Oerting, head of the EC3. “EC3 added its expertise, information communications technology infrastructure and analytic capability, as well as provided the platform for high-level cooperation between cybercrime units in five European countries and Microsoft.”
Due to its botnet architecture, ZeroAccess is one of the most robust and durable botnets in operation today and was built to be resilient to disruption efforts, relying on a peer-to-peer infrastructure that allows cybercriminals to remotely control the botnet from tens of thousands of different computers. ZeroAccess is used to commit a slew of crimes, including search hijacking, which “hijacks”
people’s search results and redirects people to sites they had not intended or requested to go to in order to steal the money generated by their ad clicks.
ZeroAccess also commits click fraud, which occurs when advertisers pay for clicks that are not the result of legitimate, interested human users’ clicks, but are the result of automated Web traffic and other criminal activity.
Research by the University of California, San Diego shows that as of October 2013, 1.9 million computers were infected with ZeroAccess, and Microsoft determined there were more than 800,000 ZeroAccess-infected computers active on the Internet on any given day.
“The coordinated action taken by our partners was instrumental in the disruption of ZeroAccess; these efforts will stop victims’ computers from being used for fraud and help us identify the computers that need to be cleaned of the infection,” said David Finn, executive director and associate general counsel of the Microsoft Digital Crimes Unit. “Microsoft is committed to working collaboratively — with our customers, partners, academic experts and law enforcement — to combat cybercrime. And we’ll do everything we can to protect computer users from the sinister activities and criminal networks that victimize innocent people and businesses around the world.”
Last week, Microsoft filed a civil suit against the cybercriminals operating the ZeroAccess botnet and received authorization from the U.S. District Court for the Western District of Texas to simultaneously block incoming and outgoing communications between computers located in the U.S. and the 18 identified Internet Protocol (IP) addresses being used to commit the fraudulent schemes. In addition, Microsoft took over control of 49 domains associated with the ZeroAccess botnet. A10 Networks provided Microsoft with advanced technology to support the disruptive action.
As Microsoft executed the order filed in its civil case, Europol coordinated a multijurisdictional criminal action targeting the 18 IP addresses located in Europe. Specifically, Europol worked with Latvia, Luxembourg, Switzerland, the Netherlands and Germany to execute search warrants and seizures on computer servers associated with the fraudulent IP addresses located in Europe.
This is the second time in six months that Microsoft and law enforcement have worked together to successfully disrupt a prevalent botnet. It demonstrates the value coordinated operations have against cybercriminal enterprises.
“If the hacker community has not yet taken notice, today’s disruption of the ZeroAccess botnet is another example of the power of public-private partnerships,” FBI Executive Assistant Director Richard McFeely said. “It demonstrates our commitment to expand coordination with companies like Microsoft and our foreign law enforcement partners — in this case, Europol — to shut down malicious cyberattacks and hold cybercriminals accountable for exploiting our citizens’ and businesses’ computers.”
Microsoft and its partners do not expect to fully eliminate the ZeroAccess botnet due to the complexity of the threat. However, Microsoft expects that this action will significantly disrupt the botnet’s operation. Microsoft is working with ecosystem partners around the world to notify people if their computers are infected and will make this information available through its Cyber Threat Intelligence Program (C-TIP). ZeroAccess is very sophisticated malware, blocking attempts to remove it, and Microsoft therefore recommends that people visit http://support.microsoft.com/botnets for detailed instructions on how to remove this threat. Because Microsoft found that the ZeroAccess malware disables security features on infected computers, leaving the computer susceptible to secondary infections, it is critical that victims rid their computers of ZeroAccess by using malware removal or antivirus software as quickly as possible. Europol is also providing information on its website about botnets to educate the public on how to protect themselves.
More information about today’s news and the coordinated action against ZeroAccess is available at http://www.microsoft.com/en-us/news/presskits/dcu.
Legal documentation in the case can be found at http://www.botnetlegalnotice.com/ZeroAccess.
About Europol
EC3 is the focal point in the EU’s fight against cybercrime, contributing to faster reactions in the event of online crimes. It will support Member States and the European Union’s institutions in building operational and analytical capacity for investigations and cooperation with international partners. EC3 officially commenced its activities on 1 January 2013, and it aims to become the focal point in the EU’s fight against cybercrime, through building operational and analytical capacity for investigations and cooperation with international partners in the pursuit of an EU free from cybercrime. The European Cybercrime Centre is hosted by Europol; the European law enforcement agency in The Hague, The Netherlands, and thus EC3 can draw on Europol’s existing infrastructure and law enforcement network.
About FBI
As an intelligence-driven and a threat-focused national security organization with both intelligence and law enforcement responsibilities, the mission of the FBI is to protect and defend the United States against terrorist and foreign intelligence threats, including cyber-based attacks and high-technology crimes; to uphold and enforce the criminal laws of the United States; and to provide leadership and criminal justice services to federal, state, municipal, and international agencies and partners.
About A10 Networks
A10 Networks was founded in Q4 2004 with a mission to provide innovative networking and security solutions. A10 Networks makes high-performance products that help organizations accelerate, optimize and secure their applications. A10 Networks is headquartered in Silicon Valley with offices in the United States, United Kingdom, France, The Netherlands, Germany, Spain, Brazil, Japan, China, Korea, Taiwan, Hong Kong, Singapore and Malaysia. For more information, visit:
http://www.a10networks.com.
About Microsoft
Founded in 1975, Microsoft (Nasdaq “MSFT”) is the worldwide leader in software, services and solutions that help people and businesses realize their full potential.
Article source: http://www.darkreading.com/end-user/microsoft-the-fbi-europol-and-industry-p/240164485
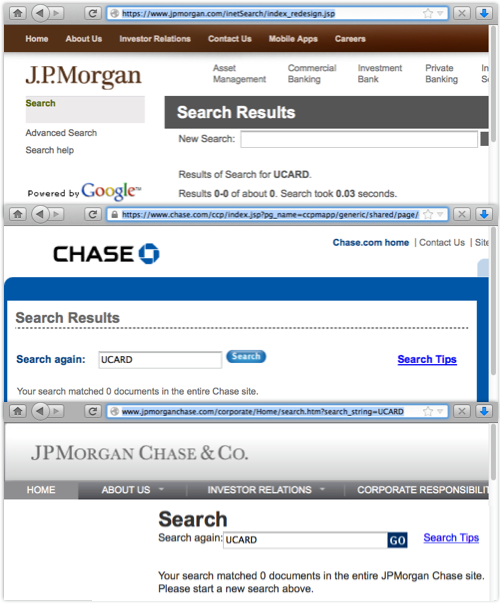
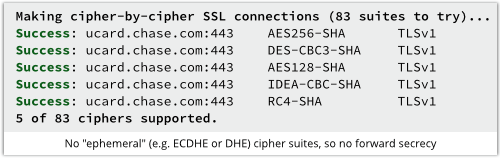
 JP Morgan Chase is the latest financial institution to own up to a data breach.
JP Morgan Chase is the latest financial institution to own up to a data breach.