Million-dollar fine for sneaky Bitcoin botnet builders
Back in May of this year we wrote about a New Jersey company’s interesting interpretation of the concept of “anti-cheating” software.
 Online gaming portal ESEA, short for E-Sports Entertainment, positions itself as a level playing field for serious online gamers.
Online gaming portal ESEA, short for E-Sports Entertainment, positions itself as a level playing field for serious online gamers.
By downloading and using ESEA’s proprietary anti-cheating client software, you effectively join a walled garden, or “fairness bubble,” from which dodgy players are meant to be excluded.
That means you can get down to genuine mano-a-mano contests (or perhaps, in multiplayer games, I mean mano-a-mano-a-mano-a-mano), without the disappointment of finding you are up against some sort of inhuman programmatic shooter-bot.
Of course, that makes the anti-cheat client itself a sort of bot.
It monitors the interaction between the player and the game, looking for evidence of cheating, for example by precisely timing events such as keypresses, or by grabbing screenshots.
The client can then call home with its data, await analysis from head office, receive instructions on what to do with suspected cheaters, and grab configuration tweaks and updates as new cheating techniques are discovered and mitigated.
In other words, you really have to trust the anti-cheating client not to be a cheat itself.
ESEA violated that trust.
An employee, who seems to have operated on the principle of hoping for forgiveness rather than permission (though he ultimately received neither), snuck in an code update that turned the anti-cheating client into a Bitcoin miner.
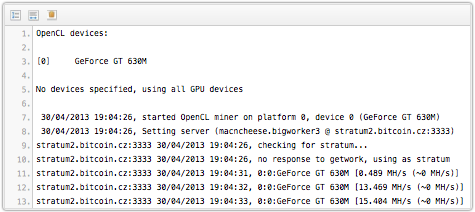
At the time, a disgruntled user, alterted to the Bitcoin mining by some give-away entries in the ESEA client log file, managed to talk to an ESEA syadmin on the phone, and received a curious admission:
It shouldn’t be any surprise, but the [anti-cheat] client is capable of doing a lot of things that people don’t know about. […] They think the client does screenshots and that’s about it. Truth be told…it probably does more than about 50 different things, because there are more than 50 ways to cheat.
[…] Funnily enough, there was a debate, a conversation, regarding the subject of using the client to mine Bitcoins. That was a joke, but at the same time it was half serious.
Actually, it turned out to have been fully serious to the very employee whom the intrepid caller had reached.
Whether the guilty party thought that he ought to get in his excuse early, now that the secret was out, or whether he just couldn’t resist taking credit for a cool hack, he felt the need to blurt out:
It turned out I actually did write code to do it, but it wasn’t supposed to be code that was everywhere. […] I restarted the server and the [configuration] setting got reset and [the mining code] actually got turned on, which was only, like, it wasn’t for very long.
We calculated how much we would actually make, if we really wanted to do it. We would make hundreds of thousands of dollars if we actually did it with everybody. But that would be pretty intense.
[Voice of caller] Not to mention kind of illegal.
At the time, ESEA netted just under $4000, a sum the company donated to charity, chipping in the same amount again from its own pocket as a sort of mean culpa.
Back in May, we asked, “Peace with honour?“
Would ESEA’s admission of guilt, we wondered, and its gesture of donating to charity, be enough to settle the matter?
We now have the answer, which is, “No!”
The New Jersey Consumer Affairs watchdog has reached an settlement with ESEA that will see the company pay a penalty of $325,000.
Actually, the penalty is a cool $1,000,000, but ESEA will be let off just over two-thirds of it ($675,000) if it behaves itself for the next ten years.
In the words of the New Jersey Attorney General’s office:
Consumers who subscribed to E-Sports’ video game anti-cheat services paid for protection from cheaters – not to be cheated by the very services they’d purchased. Companies that collect consumer information and access users’ computers have a duty to ensure that protocols and procedures are in place to protect the information they collect. Moreover, no company should obtain more access or information than is necessary to engage in the legitimate operation of its business.
ESEA, for its part, hasn’t reacted graciously at all this time, blurting out officially and in bold face that:
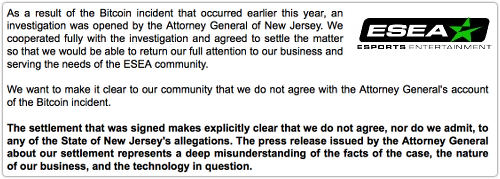
The settlement that was signed makes explicitly clear that we do not agree, nor do we admit, to any of the State of New Jersey’s allegations. The press release issued by the Attorney General about our settlement represents a deep misunderstanding of the facts of the case, the nature of our business, and the technology in question.
It seems that ESEA now thinks that mining Bitcoins was part of the legitimate operation of its business – something that may come as a surprise to its community.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/RuBkJ2Q3dQc/
 Technological defences can help a lot in protecting you from phishing and fraud.
Technological defences can help a lot in protecting you from phishing and fraud.