Proposed Canadian cyber law – anti-bullying or pro-snooping?
 The Canadian government recently put forward a new set of cyber laws designed to prevent online bullying.
The Canadian government recently put forward a new set of cyber laws designed to prevent online bullying.
The proposed legislation immediately drew howls of outrage from all corners, accusing the government of simply reviving its previous failed attempt at introducing draconian state snooping in a new disguise.
So, what’s really going on with Bill C-13?
The bill was announced by Canada’s Justice Minister Peter MacKay on November 20th, nicely coinciding with Anti-Bullying Week in the UK.
Referred to as the “Protecting Canadians from Online Crime Act”, the legislation is seen as a direct response to the deaths of Canadian cyberbullying victims Rehtaeh Parsons and Amanda Todd, both of whom committed suicide following online harassment, as have tragically many others.
The opening section of the bill seems to address this issue fairly directly, making it a criminal offence to publish or otherwise distribute “intimate images” without consent, with a potential punishment of up to five years imprisonment.
Even this part is not without controversy however, with some commentators suggesting that it would cover far more than the malicious online bullying, harassment and defamation it is aimed at, citing public interest publication and also frivolous and unintentional posting of pictures which could be seen as intimate.
Others have suggested it fails to properly understand and address the issues faced by young internet users, calling for more proactive rather than purely punitive intervention, while still others contend that the “consent” requirement may not cover the likes of “revenge porn” where images may have been taken with consent but later distributed.
Revenge porn is an area specifically targeted by new and planned laws in other jurisdictions, including California.
It is the rest of Bill C-13 that most commentators have taken issue with though.
In the summary of the bill, only the first of six key points refers directly to its ostensible main subject of cyber-bullying, while the rest detail additional powers to be granted to investigators, to access, monitor and record information on suspected digital criminals.
Much of this content seems to be recycled from the Canadian government’s previous attempt at getting this legislation, 2012’s Bill C-30, known as the “Protecting Children from Internet Predators Act” and introduced as an attempt to battle online paedophilia.
This seems to reveal a pattern of hiding these provisions under the cover of a clearly worthwhile effort to protect young people, although Bill C-30 was originally (and rather more honestly) entitled the “Lawful Access Act”, in reference to the added access rights it would have granted to police.
One Canadian minister went as far as claiming that those who opposed the bill stood on the side of child pornographers. Bill C-30 was killed after public outcry at the snooping powers it would have granted.
This was back in 2012, before the whole Snowden/NSA debacle heightened public awareness of just how much governments may be intruding into their privacy online.
Canadian legal experts point out that the new bill retreads much the same ground, although some of the most widely-criticised components have been removed, including granting full and unimpeded access to subscriber info from phone and internet provider firms, with no need for warrants, and requiring ISPs to build in interception methods into their systems.
 The new powers that remain in Bill C-13 include granting immunity to anyone who hands over personal info to the police as long as there is no explicit ban on passing on such info – so, police can call on anyone they think may have data they might be interested in and ask for a look at it, with no requirement that they have any reason to want to see that data.
The new powers that remain in Bill C-13 include granting immunity to anyone who hands over personal info to the police as long as there is no explicit ban on passing on such info – so, police can call on anyone they think may have data they might be interested in and ask for a look at it, with no requirement that they have any reason to want to see that data.
The data holders will not be obliged to comply without a warrant, but they will not be penalised if they do hand over information.
Where warrants are required, they seem to mostly only require the police have “reasonable grounds to suspect” some sort of wrongdoing, rather than the more usual and considerably stricter “grounds to believe”.
New warrants proposed include ones allowing access to metadata and location information from suspects’ devices and service providers, and letting the police avoid telling people that they have been subject to such intrusions.
There are also tweaks to sections of law covering what could be loosely called “hacking”, including accessing systems or intercepting data or passwords without authorisation, as well as making or owning hardware or software designed to access for-fee services without paying (previously only hardware was covered), and creating tools which might facilitate hacking.
All in all there seems to be quite a lot here worth worrying about. There is doubtless some worthwhile content in the bill, but the way it has been put together looks at best misguided, at worst duplicitous.
Not only are there many points which remain little changed from the previous highly controversial outing, they have once again been buried inside a bill which, for all its worthiness, now looks like little more than a cloak under which to hide the nastier content.
The bill has been up for debate in the Canadian parliament over the last week. It has already drawn comment from the Canadian Privacy Commissioner, and a campaign to fight the provisions has been launched.
Given the reaction the last time these powers were proposed, and the increased profile of privacy issues in the last six months or so, it seems likely that the Canadian government will face another barrage of indignation at their latest attempt to sneak in-depth snooping powers into law.
Follow @VirusBtn
Follow @NakedSecurity
Image of Canada eye and Big Brother courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/cU5YUsgEOIw/
 The popularity of online shopping continues to grow every year as cash-strapped consumers discover the savings that can be made in comparison to traditional brick and mortar retailers.
The popularity of online shopping continues to grow every year as cash-strapped consumers discover the savings that can be made in comparison to traditional brick and mortar retailers.  If you follow technology gossip, you probably saw the fuss kicked up last week by a Seattle resident called Nick Starr, who went into a local 24-hour diner wearing
If you follow technology gossip, you probably saw the fuss kicked up last week by a Seattle resident called Nick Starr, who went into a local 24-hour diner wearing 
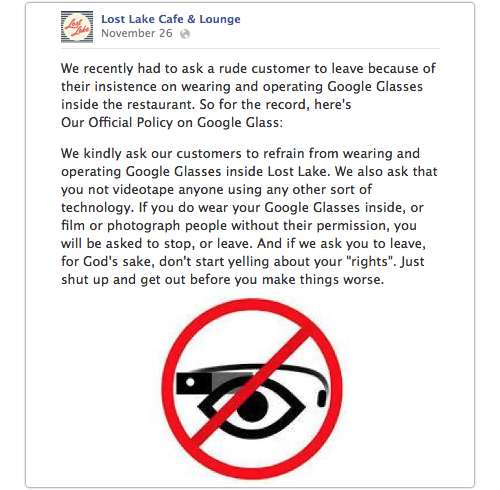
 And if you don’t like it (the ban on Google Glasses, not the Blackened Northwest Salmon), then, in the words of Lost Lake Cafe and Lounge, Open 24 Hours, Capitol Hill, 1505 Tenth Avenue, Seattle WA, “
And if you don’t like it (the ban on Google Glasses, not the Blackened Northwest Salmon), then, in the words of Lost Lake Cafe and Lounge, Open 24 Hours, Capitol Hill, 1505 Tenth Avenue, Seattle WA, “