Akamai To Acquire Prolexic
CAMBRIDGE, MA and HOLLYWOOD, FL – December 2, 2013 – Akamai Technologies, Inc. (NASDAQ: AKAM) and Prolexic Technologies, Inc. announced today that the two companies have signed a definitive agreement for Akamai to acquire Prolexic, a provider of cloud-based security solutions for protecting data centers and enterprise IP applications from distributed denial of service (DDoS) attacks.
Faced with an ever-changing threat landscape, organizations require comprehensive security solutions that address many different protection scenarios. These include securing mission‑critical Web properties and applications from attack, as well as protecting the full suite of enterprise IP applications – including email, file transfers, and VPN – across a data center.
Akamai provides leading solutions for defending Web sites and Web applications by leveraging the scale and intelligence of its global platform to protect against even the largest and most sophisticated DDoS and application-layer attacks. Prolexic combines DDoS mitigation solutions with security operations expertise for protecting data centers and enterprise IP applications.
By acquiring Prolexic, Akamai intends to provide customers with a comprehensive portfolio of security solutions designed to defend an enterprise’s Web and IP infrastructure against application-layer, network-layer and data center attacks delivered via the Internet.
“Any company doing business on the Internet faces an evolving threat landscape of attacks aimed at disrupting operations, defacing the brand, or attempting to steal sensitive data and information,” said Tom Leighton, CEO of Akamai. “By joining forces with Prolexic, we intend to combine Akamai’s leading security and performance platform with Prolexic’s highly-regarded DDoS mitigation solutions for data center and enterprise applications protection. We believe that Prolexic’s solutions and team will help us achieve our goal of making the Internet fast, reliable, and secure.”
“Today, business is defined by the availability, security and latency of Internet-facing applications, data and infrastructure,” said Scott Hammack, CEO at Prolexic. “Being able to rely on one provider for Internet performance and security greatly simplifies resolution of network availability issues and offers clients clear lines of accountability. We believe that, together, we will be able to deliver an unprecedented level of network visibility and protection.”
Under terms of the agreement, Akamai will acquire all of the outstanding equity of Prolexic in exchange for a net cash payment of approximately $370 million, after expected purchase price adjustments, plus the assumption of outstanding unvested options to purchase Prolexic stock. The closing of the transaction, which is subject to customary closing conditions, including regulatory approvals, is expected to occur in the first half of 2014. Therefore, Akamai’s Q4 2013 existing guidance remains unchanged. The Prolexic acquisition is expected to be slightly dilutive to Akamai’s Non-GAAP net income per share in the first full year post closure in the range of $0.06 to $0.08. Once the acquisition closes, the Company will include Prolexic in its guidance going forward.
Conference call scheduled today, Monday, December 2 at 8:45 a.m. ET
Akamai will host a conference call to discuss the acquisition of Prolexic today, December 2, 2013, at 8:45 a.m. Eastern time. The call may include forward-looking financial guidance from management. The call can be accessed through 1-800-706-7749 (or 1-617-614-3474 for international calls) using conference ID No. 19279933. A live Webcast of the call may be accessed at www.akamai.com in the Investor section. In addition, a replay of the call will be available for two weeks following the conference through the Akamai Website or by calling 1-888-286-8010 (or 1-617-801-6888 for international calls) and using conference ID No. 55460617.
Use of Non-GAAP Financial Measures
In addition to providing financial measurements based on generally accepted accounting principles in the United States of America (GAAP), Akamai provides additional financial metrics that are not prepared in accordance with GAAP (non-GAAP). Management uses non-GAAP financial measures, in addition to GAAP financial measures, to understand and compare operating results across accounting periods, for financial and operational decision making, for planning and forecasting purposes and to evaluate Akamai’s financial performance. The non-GAAP financial measures included in this press release are Adjusted EBITDA margin and non-GAAP net income per share.
Management believes that the use of non-GAAP financial measures allows for meaningful comparisons and analysis of trends in the business, as they exclude expenses and gains that may be infrequent, unusual in nature and not reflective of Akamai’s ongoing operating results. Management also believes that non-GAAP financial measures provide useful information to investors in understanding and evaluating Akamai’s operating results and future prospects in the same manner as used by management and in comparing financial results across accounting periods and to those of peer companies.
The non-GAAP financial measures do not replace the presentation of Akamai’s GAAP financial results and should only be used as a supplement to, not as a substitute for, Akamai’s financial results presented in accordance with GAAP. Akamai has not provided a reconciliation of each non-GAAP financial measure used in this press release to the most directly comparable GAAP financial measure because it is not practicable to do so at this time.
Akamai’s definitions of the non-GAAP financial measures used in this press release are outlined below:
• Non-GAAP net income – GAAP net income adjusted for the following tax-effected items: amortization of acquired intangible assets; stock-based compensation; amortization of capitalized stock-based compensation; restructuring charges; acquisition related costs; certain gains and losses on investments; gains and other activity related to divestiture of a business; loss on early extinguishment of debt; gains and losses on legal settlements and other non-recurring or unusual items that may arise from time to time.
• Non-GAAP net income per share – Non-GAAP net income divided by the basic weighted average or diluted common shares outstanding used in GAAP net income per share calculations.
• Adjusted EBITDA – GAAP net income excluding the following items: interest; income taxes; depreciation and amortization of tangible and intangible assets; stock-based compensation; amortization of capitalized stock-based compensation; restructuring charges; acquisition related costs; certain gains and losses on investments; gains, losses and other activity related to divestiture of a business; foreign exchange gains and losses; loss on early extinguishment of debt; gains and losses on legal settlements and other non-recurring or unusual items that may arise from time to time.
• Adjusted EBITDA margin – Adjusted EBITDA stated as a percentage of revenue.
The non-GAAP adjustments, and Akamai’s basis for excluding them from non-GAAP financial measures, are outlined below:
• Amortization of acquired intangible assets – Akamai has incurred amortization of intangible assets, included in its GAAP financial statements, related to various acquisitions the Company has made. The amount of an acquisition’s purchase price allocated to intangible assets and term of its related amortization can vary significantly and are unique to each acquisition. Therefore, Akamai excludes amortization of acquired intangible assets to provide investors with a consistent basis for comparing pre- and post-acquisition operating results.
• Stock-based compensation and amortization of capitalized stock-based compensation – Although stock-based compensation is an important aspect of the compensation to Akamai’s employees and executives, the expense varies with changes in the stock price and market conditions at the time of grant, varying valuation methodologies, subjective assumptions and the variety of award types. This makes the comparison of Akamai’s current financial results to previous and future periods difficult to interpret. Therefore, Akamai believes it is useful to exclude stock-based compensation and amortization of capitalized stock-based compensation in order to better understand the performance of Akamai’s core business performance and to be consistent with the way the investors evaluate its performance and comparison of its operating results to peer companies.
• Restructuring charges – Akamai has incurred restructuring charges, included in its GAAP financial statements, primarily due to workforce reductions and estimated costs of exiting facility lease commitments. Akamai excludes these items when evaluating its continuing business performance as such items are not consistently recurring, do not reflect expected future operating expense, nor provide meaningful insight into the current and past operations of its business.
• Acquisition related costs – Acquisition related costs include transaction fees, due diligence costs and other one-time direct costs associated with strategic activities. In addition, subsequent adjustments to the Company’s initial estimated amount of contingent consideration associated with specific acquisitions are included within acquisition related costs. These amounts are impacted by the timing and size of the acquisitions. Akamai excludes acquisition related costs and benefits to provide a useful comparison of the Company’s operating results to prior periods and to its peer companies because such amounts vary significantly based on magnitude of its acquisition transactions.
• Gain and other activity related to divestiture of a business – Akamai recognized a gain and other activity associated with the divestiture of its Advertising Decision Solutions business. Akamai excludes gains and other activity related to divestiture of a business because sales of this nature occur infrequently and are not considered part of the Company’s core business operations.
• Income tax-effect of non-GAAP adjustments – The non-GAAP adjustments described above are reported on a pre-tax basis. The income tax effect of non-GAAP adjustments is the difference between GAAP and non-GAAP income tax expense. Non-GAAP income tax expense is computed on non-GAAP pre-tax income (GAAP pre-tax income adjusted for non-GAAP adjustments) and excludes certain discrete tax items (such as recording or release of valuation allowances), if any. Akamai believes that applying the non-GAAP adjustments and their related income tax effect allows the Company to more properly reflect the income attributable to its core operations.
About Prolexic
Prolexic is one of the largest, most trusted Distributed Denial of Service (DDoS) mitigation providers in the world. Designed to absorb large and complex attacks, Prolexic aims to restore mission-critical Internet-facing infrastructures for global enterprises and government agencies within minutes. Some of the world’s largest banks and the leading companies in e-Commerce, SaaS, payment processing, travel/hospitality, gaming, energy and other at-risk industries rely on Prolexic to protect their businesses. Founded in 2003 as a leading cloud DDoS mitigation platform, Prolexic is headquartered in Hollywood, Florida, and has scrubbing centers located in the Americas, Europe and Asia. To learn more about Prolexic, please visit www.prolexic.com and @Prolexic on Twitter.
About Akamai
Akamai is the leading provider of cloud services for delivering, optimizing and securing online content and business applications. At the core of the Company’s solutions is the Akamai Intelligent Platformtrade providing extensive reach, coupled with unmatched reliability, security, visibility and expertise. Akamai removes the complexities of connecting the increasingly mobile world, supporting 24/7 consumer demand, and enabling enterprises to securely leverage the cloud. To learn more about how Akamai is accelerating the pace of innovation in a hyperconnected world, please visit www.akamai.com or blogs.akamai.com, and follow @Akamai on Twitter.
Article source: http://www.darkreading.com/management/akamai-to-acquire-prolexic/240164358
 The Debian Linux security team recently pushed out an
The Debian Linux security team recently pushed out an 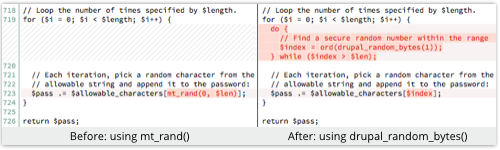

 The Debian Linux security team recently pushed out an
The Debian Linux security team recently pushed out an