 US financial companies are the best protected against the risk of cyberattack, with the energy and retail sectors not too far behind. In contrast, technology businesses consistently rate far lower, according to a study by risk analysis firm BitSight.
US financial companies are the best protected against the risk of cyberattack, with the energy and retail sectors not too far behind. In contrast, technology businesses consistently rate far lower, according to a study by risk analysis firm BitSight.
The study is based on the firm’s security risk rating system, measured by analysing factors like data breaches, but also including levels of spam and botnet traffic observed coming from within a company’s IP space and how long it takes to mop up breaches and infections.
It looked at 70 Fortune 200 companies, over the 12 months leading up to September 2013. The results show a noticeable dip around April this year, apparently coinciding with a general uptick in the threat level at around that time.
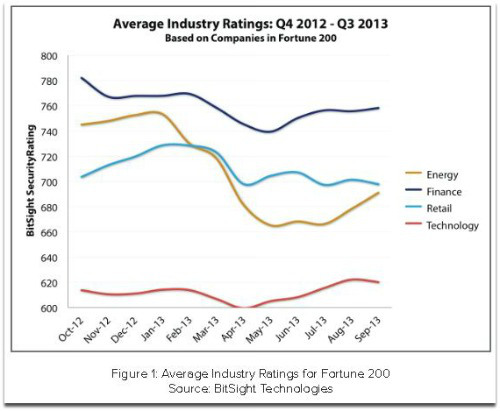
This wave hit the energy sector hardest, dropping its rating to below that of retail where it stayed for the rest of the year, but finance maintained a clear lead throughout, and technology lagged well behind for the entire period.
Financial institutions are clearly the choicest of targets for cybercrooks, combining the potential for huge one-off digital heists with access to customer data which can be leveraged into similarly huge sums through multiple smaller frauds.
Banks have also been subject to numerous hacktivist attacks in recent years, although perhaps not so much in the last year.
It seems they are doing a reasonable job of maintaining their security borders, mainly thanks to taking such things more seriously, it is suggested.
The BitSight report cites a survey, conducted in 2012 by Carnegie Mellon University’s CyLab, which found that financial firms are far more likely to employ high-level executives with explicit responsibility for security and risk (CSOs, CISOs, and Chief Risk Officers).
Simply employing people to fill these roles isn’t enough, of course; they have to be properly skilled and informed as well as empowered and incentivized to maintain the best possible security levels. But even just by having the role, companies can send a clear message that they are giving the proper weight to security and privacy issues.
Other sectors are also serious targets for cyberattack too, with retail, like finance, a big draw for cybercriminals looking to get access to precious card numbers.
Retail has of course been hit by both large- and small-scale data breaches in the last year.
Meanwhile the energy sector is more likely to be threatened by the potential for terror and extortion attacks, and while security in this sector should be bolstered by government spending, it has still seen its share of breaches and compromises.
The tech sector is something of an outlier in many ways, being largely outside direct government control and not subject to many of the data-handling requirements that banks and retailers have to meet. It is worrying though that security in this sector is so lax, given the combined dangers of industrial espionage and leakage of client information.
This sort of leakage seems to have contributed heavily to the sector’s poor ratings, with massive breaches like the Adobe leak of tens of millions of user login details, made worse by sloppy cryptography, cited as a major factor.
But it’s not just data leakage. It seems that tech firms are also slowest to deal with malware infections, something of a surprise given that there should be more skilled technical people on hand to help clean things up.
By this metric the difference is less pronounced, with energy and retail not far ahead of tech in terms of velocity in dealing with botnet infestations, but finance again does well. In terms of spam seen emerging from company networks, retail just scrapes ahead of finance, with tech and energy on level pegging not too far behind.
For the most part, the duration of a breach is of minor importance; if hackers can get hold of your entire customer database the moment they get in, they won’t gain much by waiting around for a few days to add any new names to their lists.
Still, knowing how long it takes to spot and clear up an infection gives a good indicator of how strong a firm’s security is in general.
In the end it’s all about attitude. At a corporate level we’re just not giving security the importance it merits, unless forced to do so by strict regulation.
Until all companies, whatever sector they are in, realise that the data they hold is a potential target and that they must take proper measures to ensure it is kept safe, we’ll keep on seeing our info regularly being scooped up by the bad guys.
Perhaps the banks are working harder because our info can be converted so directly into their money. Other businesses need to learn that nowadays all information is valuable, and should be treated as such.
Image of lock on digital screen courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/0c9soKFsrYw/

 Last week, we wrote about how a UK blogger named DoctorBeet
Last week, we wrote about how a UK blogger named DoctorBeet 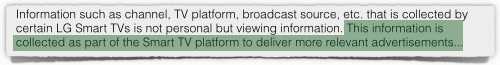

 China’s infamous Great Firewall, the massive surveillance and censorship system sitting between China’s internet and the rest of the world, has been circumvented and bypassed by numerous techniques over the years with varying degrees of success and longevity.
China’s infamous Great Firewall, the massive surveillance and censorship system sitting between China’s internet and the rest of the world, has been circumvented and bypassed by numerous techniques over the years with varying degrees of success and longevity. US financial companies are the best protected against the risk of cyberattack, with the energy and retail sectors not too far behind. In contrast, technology businesses consistently rate far lower, according to a
US financial companies are the best protected against the risk of cyberattack, with the energy and retail sectors not too far behind. In contrast, technology businesses consistently rate far lower, according to a 