What You Need To Know About CryptoLocker
During the past couple months, ransomware known as CryptoLocker has made its presence known in homes and businesses around the world. While ransomware is not a new concept, the pervasiveness of CryptoLocker, combined with its strong encryption, make it a particularly nefarious ongoing threat.
CryptoLocker is Windows-based ransomware that encrypts files on local drives and network shares, and then demands payment to unlock them. Funds are requested via untraceable payment methods like Bitcoin and MoneyPak. CryptoLocker uses asymmetric encryption, with the private key held by the author or distributor of the malware. Unfortunately, it uses a strong algorithm that makes it practically impossible to decrypt the data without knowing the key. Here’s a video showing CryptoLocker in action.
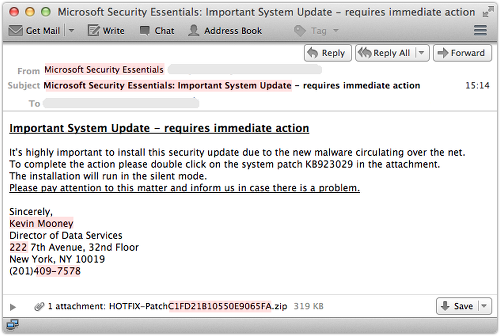
CryptoLocker has, to date, been spread predominantly through email attachments and through other malware that has already infected PCs via other means. It has also been seen as a payload in drive-by downloads.
While CryptoLocker itself can be removed, the strong encryption prevents data encrypted by the malware from being unlocked. Thus, the best remedy for an infection is often to wipe the PC, reinstall Windows, and restore data from a backup that was made preinfection.
Fortunately, CryptoLocker is generally preventable. The best endpoint security products not only detect and block known versions of the malware, but also have techniques for identifying new variants and for blocking exploits and known malicious URLs. Perimeter and anti-spam protection can also be employed to reduce the risk of infection.
The irreversible damage to data reminds us of the importance of having an ironclad backup strategy for users’ data. This has to extend beyond simple syncing of local files to a network drive or cloud storage; it must include the ability to recover older versions of files from tape, snapshots, etc. If you haven’t recently assessed what information your users are storing locally and how much it would cost in time and lost productivity if that information became inaccessible, then it may be time to revisit your backup strategy.
CryptoLocker represents an evolutionary step in ransomware: the first really widespread attack that uses strong, irreversible encryption. You can expect that additional evolution will occur. Perhaps the next iteration of CryptoLocker will self-replicate or lock users out of their online accounts, for example. The best security against any future iteration is a layered approach that patches vulnerabilities, detects and blocks exploits, risky URLs, and malicious code throughout your environment, and ensures you can recover systems and data in the event that an attack succeeds. And, of course, a bit of user education always helps, too.
Thanks to Paul Ducklin and my colleagues in SophosLabs, whose research I drew on heavily for this column.
Article source: http://www.darkreading.com/sophoslabs-insights/what-you-need-to-know-about-cryptolocker/240164183