NEW YORK, Nov. 15, 2013 /PRNewswire/ — Mobile transactions — running the gamut of everything from having your payment card swiped through a smartphone attachment to using mobile apps to redeem offers to tapping your smartphone to a special in-store device to pay for an item — are showing growth in the percentage of Americans who have experienced them firsthand. However, the segment — particularly in its tap-to-pay application — is still struggling to earn consumer interest.
(Logo: http://photos.prnewswire.com/prnh/20100517/NY06256LOGO)
These are some of the results of The Harris Poll of 2,577 adults surveyed online between September 18 and 24, 2013 by Harris Interactive. (Full results, including data tables, available here)
‘Tap-to-Pay’ expectations mixed
Consistent with a 2012 Harris Poll, majorities of Americans appear to be anticipating tap-to-pay smartphone payments eventually replacing payment card
(64%) and cash (59%) transactions (72% and 66%, respectively, among smartphone
users) in the future – but not in the near future. Three in ten Americans (29%; 33% among smartphone users – down slightly from 32% and 38%, respectively, in
2012) believe such transactions will replace payment card transactions in less than five years, and one-fourth (26%; 29% among smartphone users – comparable to 26% and 31%, respectively, in 2012) believe it will replace cash transactions within that timeframe.
However, more smartphone users than in 2012 indicate that tap-to-pay transactions will never replace payment card (24% 2012, 28% 2013) or cash (30% 2012, 34% 2013) transactions.
Firsthand experiences on the rise…
Taking a step back, it’s been an eventful year for exposure to the smartphone payment realm. Americans – smartphone users in particular – are more likely than in 2012 to have either personally completed or witnessed firsthand each of a series of mobile transaction types, including (but not limited to):
— Paying for a product or service with a credit card and having your card
swiped through an attachment on the seller’s smartphone, sometimes
referred to as “Mobile vendor” type transactions (Americans: 25% 2012,
32% 2013 / Smartphone users: 35% 2012, 43% 2013).
— Processing a payment by tapping your smartphone against a special
receiver at a store or other merchant, instead of using cash or a
payment card (Americans: 13% 2012, 17% 2013 / Smartphone users: 18%
2012, 23% 2013).
..but interest declining for tap-to-pay
Looking at the consumer side of the equation, while tap-to-pay experiences may be on the rise, interest in using a smartphone to process in-person payments instead of cash or cards has dropped slightly since last year among Americans as a whole (27% 2012, 24% 2013) and more notably among smartphone users (44% 2012, 37% 2013).
— Echo Boomers (35%) and Gen Xers (30%) display stronger interest in doing
so than Baby Boomers (16%) or Matures (12%).
Among those not interested in using a smartphone to process payments, a simple lack of compelling motivation remains one of the top factors impeding interest, with 53% saying they don’t see any reason to switch from cash or payment cards.
This also holds true for smartphone users where a majority (58%) don’t see any reason to switch from cash or payment cards either, although this perspective did decline a bit from 2012 (62%).
Security concerns are the other top impediment; 53% of those uninterested in using a smartphone to process in-person transactions also say they don’t want to store sensitive information on their phone, while nearly half (47%, up from 40% in 2012) don’t want to transmit sensitive information to the merchant’s device.
Security concerns are also a worry among smartphone users, albeit with some changes since 2012:
— Though over six in ten (62%) listed the fact that they don’t want to
store sensitive information on their phone as a reason for lack of
interest, it’s worth noting that this position softened from 68% in
2012.
— On the other hand, the 55% indicating that they don’t want to transmit
sensitive information to the merchant’s device represents a modest
increase for this concern since 2012 (51%).
Consumers still waiting for Mobile Payment Motivations Initiatives to ease the transition over to mobile payments, while moderately impactful on attitudes in 2012, also seem to be losing their footing. Just under one-fourth of Americans (24%) and roughly one-third of smartphone users (34%) indicate that being able to make mobile payments while still taking advantage of their existing credit card reward programs would make them more interested in doing so, representing drops of four and six percentage points, respectively from 2012 (when 28% of Americans and 40% of smartphone users said it would make them more interested).
The ability to use a smartphone as a “digital wallet” with electronic versions of all the identifications, loyalty program cards and other documentation normally carried in a wallet (thus freeing consumers to leave their wallets at
home) experienced similar drops, with 26% of Americans and 36% of smartphone users (down from 30% and 43%, respectively, in 2012) saying this would make them more interested in doing so using a smartphone to make in-person payments.
“Dwindling interest since last year may be an indication that the initial interest has fallen short with practical use, and has not yet been followed up by a constructive call to action by manufacturers and retailers,” explains Aaron Kane, senior research director at Harris Interactive and a key consultant on Harris Poll TECHpulse, a new research product designed to track consumer awareness of and attitudes toward emerging technologies, such as mobile payments. “Right now, the bottom line is that consumers don’t yet feel as if they’re being presented with a compelling enough reason to switch their payment habits, nor are they confident that these new methods are secure. This knowledge ‘gap’ represents an opportunity for companies to change the conversation by addressing these issues head-on.”
For information regarding Harris Interactive’s TECHpulse research tool [email protected].
To see other recent Harris Polls, please visit the Harris Poll News Room.
Want Harris Polls delivered direct to your inbox? Click here!
Methodology
This Harris Poll was conducted online within the United States between September
18 and 24, 2013 among 2,577 adults (aged 18 and over). Figures for age, sex, race/ethnicity, education, region and household income were weighted where necessary to bring them into line with their actual proportions in the population. Propensity score weighting was also used to adjust for respondents’
propensity to be online.
All sample surveys and polls, whether or not they use probability sampling, are subject to multiple sources of error which are most often not possible to quantify or estimate, including sampling error, coverage error, error associated with nonresponse, error associated with question wording and response options, and post-survey weighting and adjustments. Therefore, Harris Interactive avoids the words “margin of error” as they are misleading. All that can be calculated are different possible sampling errors with different probabilities for pure, unweighted, random samples with 100% response rates. These are only theoretical because no published polls come close to this ideal.
Respondents for this survey were selected from among those who have agreed to participate in Harris Interactive surveys. The data have been weighted to reflect the composition of the adult population. Because the sample is based on those who agreed to participate in the Harris Interactive panel, no estimates of theoretical sampling error can be calculated.
These statements conform to the principles of disclosure of the National Council on Public Polls.
The results of this Harris Poll may not be used in advertising, marketing or promotion without the prior written permission of Harris Interactive.
The Harris Poll(r) #84, November 15, 2013
By: Larry Shannon-Missal, Harris Poll Research Manager
About Harris Interactive’s TECHpulse Research Tool TECHpulse is a multi-client product development and marketing research-based tool that provides trendable business information on consumer consumption and attitudes towards a variety of technology categories (i.e., Wearable Technologies, Mobile Payments and more). It also delivers strategic consumer insight into new and emerging technologies to support business decision-making.
Companies can use TECHpulse research to…
— Fine-tune existing product lines
— Develop new product lines
— Help prioritize feature development
— Help with feature packaging and pricing
— Guide the direction of technology strategy About Harris Interactive Harris Interactive is one of the world’s leading market research firms, leveraging research, technology, and business acumen to transform relevant insight into actionable foresight. Known widely for The Harris Poll(r), Harris offers proprietary solutions in the areas of market and customer insight, corporate brand and reputation strategy, and marketing, advertising, public relations and communications research across a wide range of industries.
Additionally, Harris has a portfolio of multi-client offerings that complement our custom solutions while maximizing a client’s research investment. Serving clients worldwide through our North American and European offices, Harris specializes in delivering research solutions that help our clients stay ahead of what’s next. For more information, please visit www.harrisinteractive.com.
Article source: http://www.darkreading.com/mobile/exposure-to-mobile-payment-grows-but-con/240163983
 Snapchat has thumbed its nose at Facebook’s $3 billion, all-cash offer, the Wall Street Journal
Snapchat has thumbed its nose at Facebook’s $3 billion, all-cash offer, the Wall Street Journal  Snapchat was designed to allow senders to control how long a message or picture could be seen.
Snapchat was designed to allow senders to control how long a message or picture could be seen. Mavis Batey MBE, codebreaker extraordinaire at Bletchley Park during World War II, died this week at the age of 92.
Mavis Batey MBE, codebreaker extraordinaire at Bletchley Park during World War II, died this week at the age of 92. The Enigma was an electromechanical encryption device, patented by a German engineer in 1918.
The Enigma was an electromechanical encryption device, patented by a German engineer in 1918.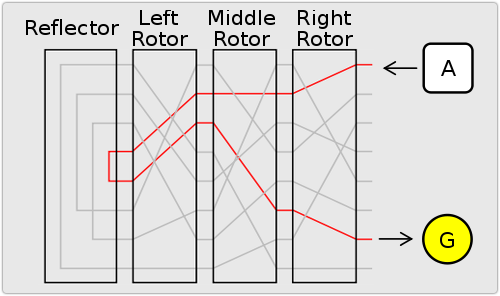
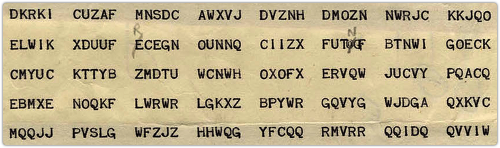
 European travellers will soon be able to use their personal electronic devices (PEDs) for the entire duration of their flights following a new ruling from Europe’s air safety agency.
European travellers will soon be able to use their personal electronic devices (PEDs) for the entire duration of their flights following a new ruling from Europe’s air safety agency.