ControlScan And Merchant Warehouse Report New Findings On SMB Merchants’ Payment Security Awareness
ATLANTA, Nov. 12, 2013 – ControlScan and Merchant Warehouse have jointly released the results of their fifth annual survey of Level 4 merchants’ awareness, sentiment and progress toward securing cardholder data in compliance with payment card industry (PCI) standards.
The Level 4 merchant group represents 98% of all U.S. retailers, is primarily comprised of small to mid-sized businesses (SMBs), and numbers in the millions. The newly-released research report “Payment Security and the SMB: The Fifth Annual Survey of Level 4 Merchant PCI Compliance Trends” reveals that as a group these merchants are making progress, yet key concerns remain.
“Nearly three-quarters of survey respondents believe complying with PCI standards improves the security of their business, and that’s encouraging,” said Joan Herbig, CEO of ControlScan. “As a whole, though, these merchants are showing a lack of corresponding activity for prevention and detection. In addition, they are not prepared should a data breach occur.”
A total of 615 Level 4 merchants responded to the 2013 survey, providing many critical insights for independent sales organizations (ISOs), acquirers and other merchant service providers (MSPs), including:
43% are personally responsible for information security in their organization, while 35% say no one is assigned the responsibility;
51% do not require their third-party service providers to achieve and maintain PCI compliance; and
Only 36% have developed an incident response plan (IRP) for their business.
“SMB merchants have a distinct need when it comes to payment security and compliance,” said Henry Helgeson, CEO, Merchant Warehouse. “Very few have the time or resources to think through what it takes to better their security posture, and most don’t even realize the significant risk their business faces. It’s up to us as their MSP to give them a cost-effective, simplified way to succeed in this regard.”
To access a copy of the survey research report, which includes an in-depth discussion of the implications Level 4 merchants’ responses have for their own breach risk as well as the risk the MSPs serving them face, please click on the following link:https://www.controlscan.com/whitepapers/merchant-study-2013.php.
In addition, ControlScan and Merchant Warehouse are hosting a joint webinar on November 20, 2013to present the study’s findings. Click here for more information and to register:https://www2.gotomeeting.com/register/397376026.
About ControlScan
Headquartered in Atlanta, Georgia, ControlScan delivers payment security and compliance solutions to a global network of merchant service providers and the small businesses they serve. The company’s innovative approach to secure hosted payment and PCI compliance solutions leverages technology, education and services to provide flexible options for its customers. Known for its thought leadership, ControlScan gives its customers a clear view of marketplace issues and trends so they can remain competitive. For more information, please visit www.controlscan.com or call 1-800-825-3301.
About Merchant Warehouse
Merchant Warehouse is a leading provider of payment technologies and merchant services. The company’s solutions enable merchants to more effectively connect and engage with their customers regardless of how, where or when they choose to shop. Merchant Warehouse’s flagship technology solution, the Geniustrade Customer Engagement Platformtrade, supports both traditional and new payment types, including mobile commerce, from a single countertop acceptance device. For more information about Merchant Warehouse, please visit merchantwarehouse.com or follow the company on Twitter at@MWarehouse
Article source: http://www.darkreading.com/privacy/controlscan-and-merchant-warehouse-repor/240163841
 November’s Patch Tuesday is coming up this week, and Microsoft’s usual “announcement that
November’s Patch Tuesday is coming up this week, and Microsoft’s usual “announcement that  A New York City police detective from the NYPD pleaded guilty on Friday to paying $4,000 for email hacking services that got him into at least one colleague’s email account and one mobile phone.
A New York City police detective from the NYPD pleaded guilty on Friday to paying $4,000 for email hacking services that got him into at least one colleague’s email account and one mobile phone. South East Asia has had its fair share of Anonymous excitement lately.
South East Asia has had its fair share of Anonymous excitement lately.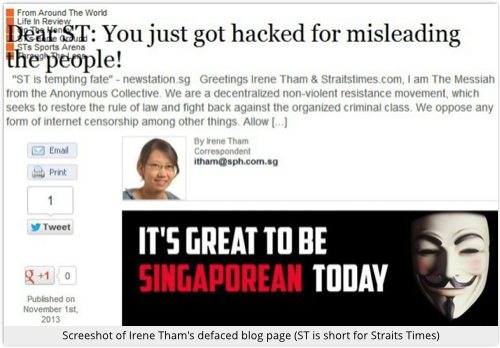
 Worse luck for Raj is that he is currently in custody in the city state
Worse luck for Raj is that he is currently in custody in the city state  Most
Most