Apple’s gov transparency report jabs thumb in eyes of Google, Facebook
5 ways to prepare your advertising infrastructure for disaster
Apple has joined Facebook, Google, Microsoft, Twitter, and Yahoo!’s transparency club, releasing a detailed report on the numbers and types of requests for personal records it has received from law enforcement and government agencies around the world.
“We have reported all the information we are legally allowed to share,” the report, issued Tuesday, states, “and Apple will continue to advocate for greater transparency about the requests we receive.”
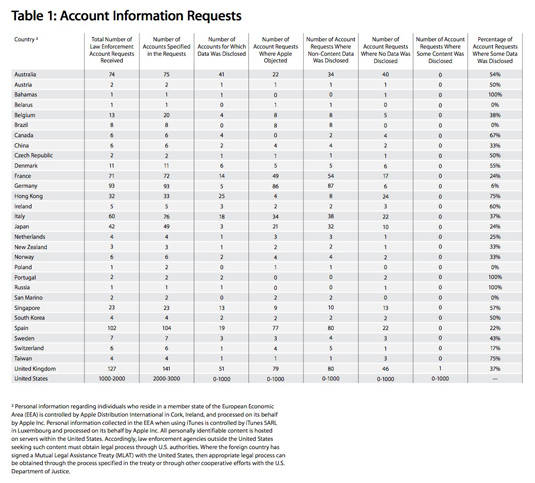
The report’s Account Information Requests table, below (click to make readable), lists the exact number of requests received, acted upon, and other details from the 31 countries from which Apple received such requests. “Some countries are not listed in this report,” a note reads, “because Apple has not received any information requests from the government there.”
Among the 31, only one country disallows companies from revealing the exact number of requests. Yes, you guessed right: the good ol’ U.S. of A.
“At the time of this report,” Apple notes, “the U.S. government does not allow Apple to disclose, except in broad ranges, the number of national security orders, the number of accounts affected by the orders, or whether content, such as emails, was disclosed. We strongly oppose this gag order, and Apple has made the case for relief from these restrictions in meetings and discussions with the White House, the U.S. Attorney General, congressional leaders, and the courts.”
Account requests, Apple says, commonly involve law enforcement asking for information regarding robberies or other crimes, as well as searches for missing persons or kidnapping victims.
“In very rare cases,” the report says about account requests, “we are asked to provide stored photos or email. We consider these requests very carefully and only provide account content in extremely limited circumstances.”
In the report, Apple manages the somewhat contortionistic feat of simultaneously patting itself on the back while sticking its thumbs in the eyes of such companies as Google, Facebook, Twitter, and the like. After saying that the privacy of their customers is “a consideration from the earliest stages of design for all our products and services” and that they “work hard to deliver the most secure hardware and software in the world,” the thumbs comes out:
Perhaps most important, our business does not depend on collecting personal data. We have no interest in amassing personal information about our customers. We protect personal conversations by providing end-to-end encryption over iMessage and FaceTime. We do not store location data, Maps searches, or Siri requests in any identifiable form. … Unlike many other companies dealing with requests for customer data from government agencies, Apple’s main business is not about collecting information.
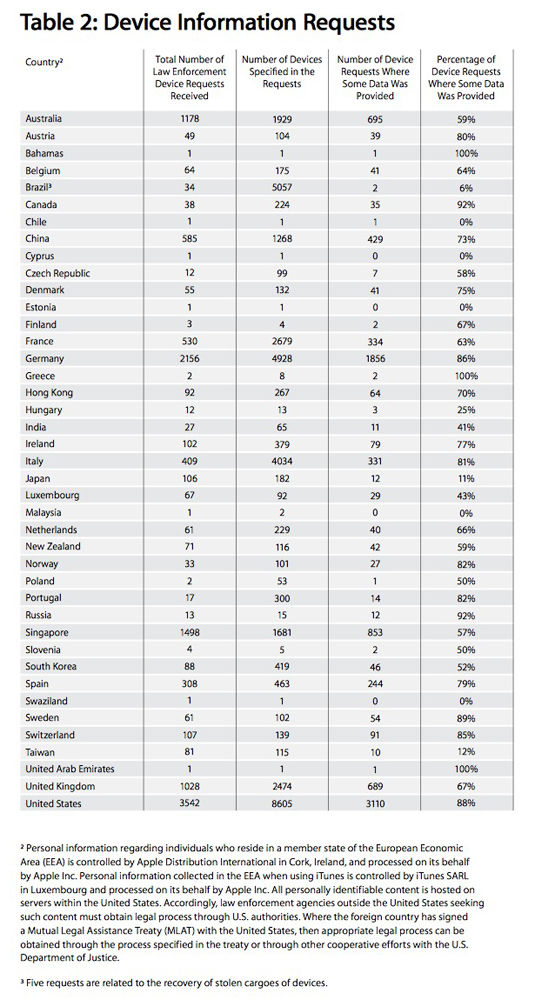
In addition to the information on requests for account information, Apple also provides details on device requests, of which they say “the vast majority” relate to lost or stolen devices. “These types of requests frequently arise when our customers ask the police to assist them with a lost or stolen iPhone, or when law enforcement has recovered a shipment of stolen devices.”
Apple also notes that it has never received an order to release information under Section 215 of the USA PATRIOT* Act.
That section, under challenge by such civil liberties organizations as the EFF and the ACLU, allows the FBI – and who knows what other federal authorities – to obtain secret clearance from the FISA court to obtain information from a company about you and your activities, ostensibly to “to protect against international terrorism or clandestine intelligence activities.” The company must hand over that info to the investigators under a gag order that prevents them from ever informing you+world+dog that they even received the order.
“We would expect to challenge such an order if served on us,” Apple says. However, we may never know whether or not they were so served, or if they challenged such an order. Section 215 remains the law of the the land here in the good ol’ U.S. of A. ®
Bootnote
* Do know that the USA PATRIOT Act is so capitalized because its common name is an acronym for its full name: the Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism Act of 2001.
Free Regcast : Managing Multi-Vendor Devices with System Centre 2012
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/11/05/apple_transparency_report_sticks_thumb_in_eyes_of_google_facebook/