 A number of readers have asked us, “What do you guys have to say about the BadBIOS story that’s unfolding at the moment?”
A number of readers have asked us, “What do you guys have to say about the BadBIOS story that’s unfolding at the moment?”
In a nutshell, it’s a story about a virus that is claimed to have some remarkable characteristics.
Sufficiently remarkable, in fact, to inspire Ars Technica’s Dan Goodin to describe it as not just “mysterious” but “omnipotent.”
What it does
Here are some of the claims that have been made about the BadBIOS virus:
- It is said to infect the low-level system firmware of your computer, so it can’t be removed or disabled simply by rebooting.
- It is said to include components that work at the operating system level, so it affects the high-level operation of your computer, too.
- It is said to be multi-platform, affecting at least Windows, OS X, and OpenBSD systems.
- It is said to prevent infected systems being booted from CD drives.
- It is said to spread itself to new victim computers using Software Defined Radio (SDR) program code, even with all wireless hardware removed.
- It is said to spread itself to new victim computers using the speakers on an infected device to talk to the microphone on an uninfected one.
- It is said to infect simply by plugging in a USB key, with no other action required.
- It is said to infect the firmware on USB sticks.
- It is said to render USB sticks unusable if they aren’t ejected cleanly; these sticks work properly again if inserted into an infected computer.
- It is said to use TTF (font) files, apparently in large numbers, as a vector when spreading.
- It is said to block access to Russian websites that deal with reflashing software.
- It is said to render any hardware used in researching the threat useless for further testing.
- It is said to have first been seen more than three years ago on a Macbook.
By now, you may be thinking that this sounds more like a science fiction movie than real life.
 In fact, if you’re a certain age, you may well be waiting for Jeff Goldblum to burst forth with a Mac, some mysterious and onmipotent file transfer software, and a countervirus that will save the planet.
In fact, if you’re a certain age, you may well be waiting for Jeff Goldblum to burst forth with a Mac, some mysterious and onmipotent file transfer software, and a countervirus that will save the planet.
You’re probably also thinking that with as many symptoms, twists, turns and apparent tell-tales as are listed above, we ought to know a lot about it after three years.
The thing is, all the facts above come from one observer on Twitter, @dragosr, the guy who runs the CanSecWest, Eusec and PacSec security conferences.
The abovementioned details have only come out in the past short while, so we can collectively be excused for not knowing an awful lot just yet.
What we know
One BIOS sample file has been made available; SophosLabs took a brief look and largely concurred with an already-public analysis published on Reddit. (For the record, our analysts didn’t see the Reddit story until after they’d looked at the file.)
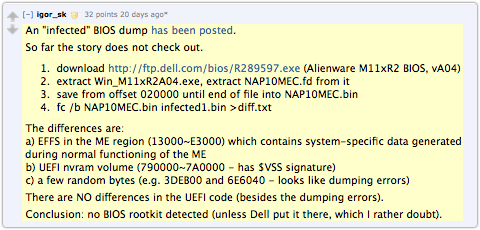
The BIOS we saw seems all but identical to an official Dell Alienware BIOS, so it would be no use on a Mac, for example.
And even if a byte-by-byte analysis of the whole BIOS were to reveal a pre-planted backdoor, that would nevertheless only be one small part of the whole story.
Furthermore, the software defined radio and speaker-to-microphone infection vectors mentioned above, as a vehicle for jumping airgaps, sound highly speculative.
Not impossible, of course – never say impossible where malware is concerned, not least since Stuxnet appeared – but certainly very unlikely.
Spreading via USB sticks, like Stuxnet did, would surely be a satisfactory explanation on its own (though the part assuming automatic code execution via USB on multiple operating systems sounds highly speculative, too).
Imagine that you could reliably get an infected system to beam out radio waves in the absence of any radio hardware, for example by relying on some serendipitously-located internal circuit parts to serve as your transmitter and antenna.
Imagine that you could somehow turn on the speaker and produce reliably-decodable but inaudible sounds.
How would you persuade the uninfected computer to receive them at all, let alone to treat them as shellcode that would ultimately let you reflash the BIOS?
Update. As several readers pointed out, @dragosr has tweeted, “To be explicit, no audio infection, just cc, only 2 unusual infection vectors IDed, USB and one other, waiting on patches before discussion.” CC means Command and Control, the name given to the data transfer mechanism by which a botnet is operated. [2013-11-01T20:00Z]
What we can predict
So the short answer to the question of what we have to say about BadBIOS is, “We can’t yet say.”
Based on @dragosr’s tweets, it looks as though additional information, including access to affected USB sticks, will become available at the PacSec conference in Tokyo in just under two weeks’ time; until then, says Dragos, he’s got to knuckle down to prepare for the event.
And, talking of the event, there are various papers about firmware and BIOS level attacks at PacSec 2013, so let’s hope that one or more of them will shed some light on what’s true and false about BadBIOS.
Until then, it’s a bit like the dilemma we faced nearly five years ago when the Conficker virus came out and stood poised to do something new on 01 April 2009.
Everyone wanted to know what it would do, but all anyone could say with honesty was, “We shan’t know until 01 April.”
What to do about BadBIOS
I don’t think there is any need for alarm over the BadBIOS story.
There isn’t an obvious threat to everyone (like there was with Stuxnet, even before we knew its inner purpose); it doesn’t seem to be spreading in the wild (like Stuxnet was, despite having a specific target); and there are plenty of clear and present threats we can usefully concern ourselves with in the interim.
So that’s about that for now, I’m afraid – it’s a question of watching and waiting.
NB. It’s possible, of course, that this is an elaborate hoax, intended as a combined publicity exercise and social engineering experiment that will be wrapped up at PacSec. If so, expect it to be aimed at outing anyone who jumped to detailed conclusions without having the details to go on!
Image of funky looking chip courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/5tjRu89lYgU/
 Anonymous uses an image of Guy Fawkes on its mask logo. Fawkes was caught underneath the parliament buildings in England, along with a huge stash of gunpowder with which he and his co-conspirators apparently planned to blow the government to smithereens, back on 05 November 1605.
Anonymous uses an image of Guy Fawkes on its mask logo. Fawkes was caught underneath the parliament buildings in England, along with a huge stash of gunpowder with which he and his co-conspirators apparently planned to blow the government to smithereens, back on 05 November 1605.
 Your mission, should you choose to accept it, is to intercept contactless payment data at distances of up to 90cm using a backpack, shopping trolley, and a small antenna.
Your mission, should you choose to accept it, is to intercept contactless payment data at distances of up to 90cm using a backpack, shopping trolley, and a small antenna. Two encrypted-email companies that shut down while struggling to keep metadata out of the US government’s hands have
Two encrypted-email companies that shut down while struggling to keep metadata out of the US government’s hands have  Facebook is testing data mining methods that would silently follow users’ mouse movements to see not only where we click but even where we pause, where we hover and for how long.
Facebook is testing data mining methods that would silently follow users’ mouse movements to see not only where we click but even where we pause, where we hover and for how long. A number of readers have asked us, “What do you guys have to say about the BadBIOS story that’s unfolding at the moment?”
A number of readers have asked us, “What do you guys have to say about the BadBIOS story that’s unfolding at the moment?” In fact, if you’re a certain age, you may well be waiting for Jeff Goldblum to
In fact, if you’re a certain age, you may well be waiting for Jeff Goldblum to 

 A woman from South Milwaukee, Wisconsin, faces stalking and identity theft charges after she allegedly hacked into her ex-boyfriend’s email and stole information not only on him, but also on his other love interests.
A woman from South Milwaukee, Wisconsin, faces stalking and identity theft charges after she allegedly hacked into her ex-boyfriend’s email and stole information not only on him, but also on his other love interests. Leaving aside the issue of personal pics, most people probably feel OK about letting their boyfriends know all manner of things about them that they wouldn’t want all and sundry to hear about, but it’s worth remembering just how useful our personal info can be to bad actors.
Leaving aside the issue of personal pics, most people probably feel OK about letting their boyfriends know all manner of things about them that they wouldn’t want all and sundry to hear about, but it’s worth remembering just how useful our personal info can be to bad actors.