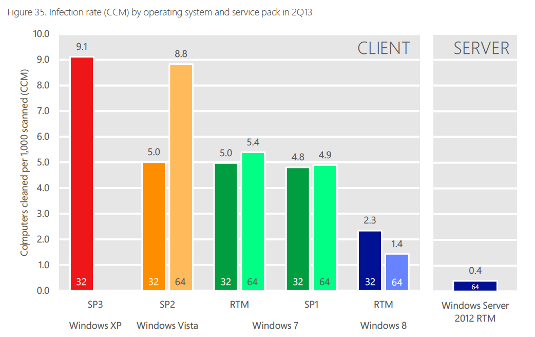
Lavabit and Silent Circle form "Dark Mail Alliance" to thwart email surveillance
 Two encrypted-email companies that shut down while struggling to keep metadata out of the US government’s hands have announced that they’re teaming up to create a new, open-source email protocol based on security and privacy and that they plan to help the world to hopefully ditch the old one: Simple Mail Transfer Protocol (SMTP).
Two encrypted-email companies that shut down while struggling to keep metadata out of the US government’s hands have announced that they’re teaming up to create a new, open-source email protocol based on security and privacy and that they plan to help the world to hopefully ditch the old one: Simple Mail Transfer Protocol (SMTP).
The collaboration, dubbed the Dark Mail Alliance, between founding companies Lavabit and Silent Circle, will be focused on maintaining and organizing the open-source code for the new email protocol.
The companies announced the alliance at Wednesday’s Inbox Love conference, held at Microsoft’s Silicon Valley campus, saying that they hope to “change the world of email completely by putting privacy and security at its core.”
The two founding companies also plan to bring other members into the alliance and to assist future recruits to implement the new protocol.
Specifically, Lavabit and Silent Circle will work jointly to help email software developers and service providers proliferate what they’re calling Email 3.0, a “private, next-generation, end-to-end encrypted alternative.”
As it is, email is now “fundamentally broken from a privacy perspective”, Lavabit said in its press release:
What we call ‘Email 3.0.’ is an urgent replacement for today’s decades old email protocols (‘1.0’) and mail that is encrypted but still relies on vulnerable protocols leaking metadata (‘2.0’).
Our goal is to open source the protocol and architecture and help others implement this new technology to address the privacy concerns over surveillance and back door threats of any kind.
Ars Technica’s Cyrus Farivar reports that the new protocol is set for a mid-2014 release.
Silent Circle CTO Jon Callas told Ars that it’s high time to boot the antiquated SMTP out the door:
This is just another transport – what we’re getting rid of is SMTP. We like to laugh at it, but there are reasons why it was a good system. We’re replacing the transport with a new transport. E-mail was designed 40 years ago when everybody on the Internet knew each other and were friends.
The new protocol will be based on Extensible Messaging and Presence Protocol (XMPP), a set of open Extensible Markup Language (XML) technologies for real-time online communication, including instant messaging, presence, multiparty chat, voice and video calls, online collaboration, gaming, file transfer, Internet of Things applications including the smart grid, and social networking services.
As Cisco describes it, the core technology behind XMPP was refined in the Jabber open-source community in 2000 and formalized by the Internet Engineering Task Force (IETF) in 2002 and 2003.
Silent Circle’s Callas told the conference that the company’s existing Silent Circle Instant Messaging Protocol (PDF) was a rough “alpha” of the new Dark Mail protocol.
Dark Mail will be available as an add-on or an option to existing email providers, which means that companies such as Google could opt to use it with Gmail, for example.
That’s not an entirely unimaginable outcome, I would say, given how furious Google reportedly is over new documents from NSA whistleblower Edward Snowden that point to the US’s National Security Agency (NSA) having infiltrated links to Yahoo and Google data centers worldwide.
Lavabit founder Ladar Levison told Ars that he will soon launch – possibly as soon as Tuesday – a Kickstarter campaign to fundraise for the Dark Mail Alliance to open-source Lavabit’s code “with support for Dark Mail built-in.”
Farivar reports that the first 32 companies to donate $10,000 will get a pre-release 60 days before the public gets it and thus will be able to be the first companies to integrate it into their systems.
Lavabit, Snowden’s former email provider, shuttered its service in August following court orders demanding metadata about an unnamed user who many assume was Snowden.
Levison did, actually, end up giving the government Lavabit’s crytopgraphic key in digital form, after having first printed out and handed over a copy of the key in 4-point type that didn’t quite fly with the government’s judge.
Shuttering Lavabit’s service meant that even though the government had the key, they didn’t have anything to open with it.
Silent Circle, for its part, in short order followed Lavabit’s example, pre-emptively shutting down its Silent Mail service in anticipation of the government getting its hands on the metadata that is, for now, inevitably associated with email.
The goal of ditching SMTP is ambitious: it’s now used for almost all email that travels on the Internet.
But as Ars reader Major General Thanatos commented, the NSA’s vigorous surveillance propensities well might have provided the world with a good reason to put its shoulder to the task and make the switch.
Would switching to XMPP stop spying once and for all? If so, how painful would such a switch be? Can you imagine the world actually doing it?
Let us know your thoughts in the comments section below.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/vEFFtSzgqLE/
 Facebook is testing data mining methods that would silently follow users’ mouse movements to see not only where we click but even where we pause, where we hover and for how long.
Facebook is testing data mining methods that would silently follow users’ mouse movements to see not only where we click but even where we pause, where we hover and for how long. A number of readers have asked us, “What do you guys have to say about the BadBIOS story that’s unfolding at the moment?”
A number of readers have asked us, “What do you guys have to say about the BadBIOS story that’s unfolding at the moment?” In fact, if you’re a certain age, you may well be waiting for Jeff Goldblum to
In fact, if you’re a certain age, you may well be waiting for Jeff Goldblum to 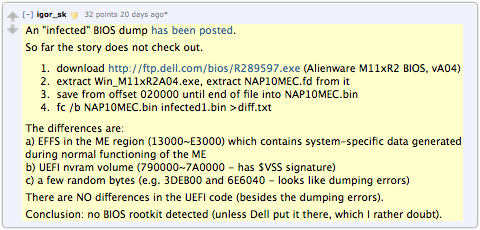
 But with 68% of the respondents saying that their security function only partially meets the needs of the business, security professionals would seem to have much work to do in order to justify any increases in funding that they hope to acquire.
But with 68% of the respondents saying that their security function only partially meets the needs of the business, security professionals would seem to have much work to do in order to justify any increases in funding that they hope to acquire.