 Microsoft just published its January-to-June 2013 Security Intelligence Report (SIR).
Microsoft just published its January-to-June 2013 Security Intelligence Report (SIR).
(Yes, I was surprised at the timing, too, since we’re already two thirds of the way through the next reporting period. But there you are, and here it is [PDF].)
I will dutifully declare that I have still to finish reading the report in full.
At 160 pages, even if some of them are blank, or contain corporate boilerplate, I just haven’t got through it yet.
But I have read one of Microsoft’s recent blog postings about the report, highlighting the part in which rates of malware infection and encounter are compared across the four flavours of client-side Windows: XP, Vista, 7 and 8.
The results seem to tell a pretty clear visual story about why you should get rid of Windows XP as soon as you can:
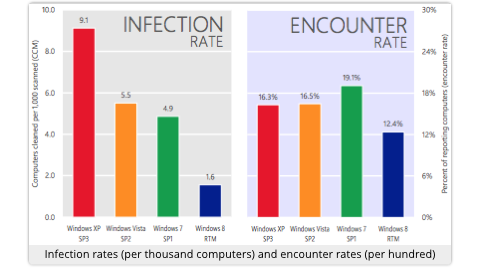
→ The numbers on the left and right sides can’t directly be compared because they’ve been scaled differently for readability. The infection rate shows computers cleaned up out of every thousand on which Microsoft’s Malicious Software Removal Tool (MSRT) was used. The encounter rate shows computers on which malware was detected – and almost certainly prevented from infecting – out of every hundred protected by a Microsoft virus blocker.
The obvious conclusion from the above is that your chance of being exposed to malware, and thus potentially infected if you were unprotected, is similar on all versions of Windows.
Windows 8 users, at first glance, appear to enjoy a slight advantage in exposure rate, with 12/100 computers measured to be actively under attack, against 16/100 or more for the other flavours of Windows.
The SIR doesn’t offer an explanation, but we can always speculate:
- Perhaps more recent versions of Internet Explorer are more likely to prevent you browsing to potentially infectious websites in the first place, thus reducing exposure?
- Perhaps Windows 8 has stronger internal safeguards against exploits, thus stopping some attacks before they get as far as provoking an anti-virus warning?
- Perhaps some Windows 8 users made the switch for security reasons, and are therefore less likely to put themselves in harm’s way?
Likewise, Windows 7 seems to be at a very slight disadvantage, with 19% of computers visibly attacked, against 16% with XP and Vista.
That might not be a statistically significant difference (nor might the apparent advantage of Windows 8, of course), or it might be a simple side-effect of that fact that Windows 7 is the most prevalent version of Windows.
The most common platform, you can argue, is more likely to be singled out by malware writers who don’t want to go to the trouble of building a multi-version exploit.
But the statistical significance of the left-hand numbers seems, at least on the surface, to be undeniable.
When users went to the trouble of looking for malware, presumably because they thought they had slipped up and got infected, they were 5.7 times more likely to find some on XP than on Windows 8.
In short, the apparent conclusion is that XP is more than five times as permeable to malware than Windows 8.
Therefore, you can argue, XP’s imminent – and, after 12 years, not exactly unexpected or untimely – Goodbye, Farewell and Amen moment should be applauded, and moving on to a more recent operating system will bring clear and immediate security benefits.
On the other hand, you can keep putting these numbers through the wringer and argue that they don’t prove much of anything at all.
For example, the MSRT only deals with a small subset of malware out there – it’s always been something of a stopgap measure for the most commonly-known malware families.
In other words, you might choose to explain the lower apparent infection rates on Windows 8 merely as a sign that the MSRT tends to miss more malware on Windows 8, being biased as a side-effect of history to detecting malware that only works on XP.
You can argue that, because the MSRT quite explicitly isn’t a broad-spectrum anti-virus, the figures on the left don’t denote infection rates at all, but are nothing more than a measure of the effectiveness of MSRT by Windows version.
The truth, I guess, is somewhere between the two.
While XP may not be an ecosytem that is 5.7 times more dangerous than Windows 8, I think it is reasonable to accept that Microsoft’s data supports the claim that you are at much greater risk if you keep on using it.
 If you need any more evidence, I suggest you take a look at our recent article series Anatomy of an exploit – inside the CVE-2013-3893 Internet Explorer zero-day.
If you need any more evidence, I suggest you take a look at our recent article series Anatomy of an exploit – inside the CVE-2013-3893 Internet Explorer zero-day.
There, we show the sort of tricks needed to pull off a drive-by exploit against Internet Explorer 9 on Windows 7, which involves working around not only Data Execution Prevention (DEP), but also Address Space Layout Randomisation (ASLR).
Without ASLR, DEP offers only a very mild extra resistance to attack – and XP doesn’t have ASLR.
That alone is probably reason enough to move before next April’s end-of-updates deadline.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/IppOnh3qVnU/
 Anonymous uses an image of Guy Fawkes on its mask logo. Fawkes was caught underneath the parliament buildings in England, along with a huge stash of gunpowder with which he and his co-conspirators apparently planned to blow the government to smithereens, back on 05 November 1605.
Anonymous uses an image of Guy Fawkes on its mask logo. Fawkes was caught underneath the parliament buildings in England, along with a huge stash of gunpowder with which he and his co-conspirators apparently planned to blow the government to smithereens, back on 05 November 1605.
 Your mission, should you choose to accept it, is to intercept contactless payment data at distances of up to 90cm using a backpack, shopping trolley, and a small antenna.
Your mission, should you choose to accept it, is to intercept contactless payment data at distances of up to 90cm using a backpack, shopping trolley, and a small antenna.

