Win XP box? You’re 6 TIMES as likely as Win 8 bods to get the pox
Supercharge your infrastructure
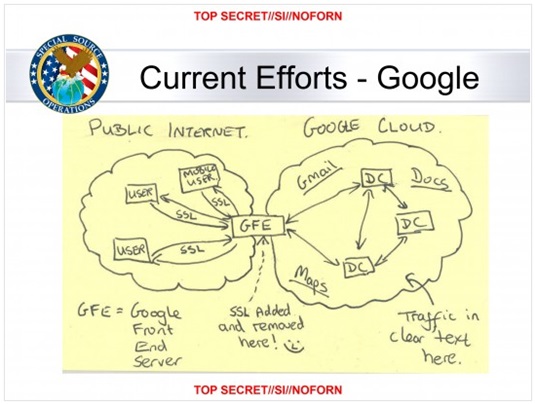
UK-based Windows XP users were six more likely to actually be infected than their counterparts who use more recent versions of Windows, according to figures from Microsoft.
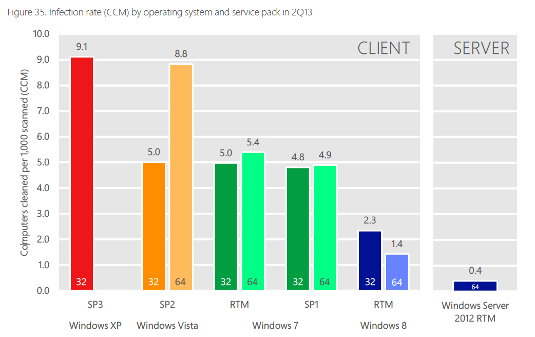
The company is likely trying to highlight the infection rates of the 12-year-old OS as a way to get customers to upgrade. It says that 9.1 of 1,000 XP (SP3) boxes scanned – which is just under one per cent – had been found to be infected.
The software giant’s latest annual “Security Intelligence Report” reports that, on average, 17 per cent of computers worldwide encountered malware during the first half of 2013.
Top threats facing the UK include HTML/IframeRef: – “specially formed” iFrame tags that point to remote websites containing malicious code; Sirefef: – a rogue security software family called Antivirus 2010 among other names; and BlacoleRef: – malicious JavaScript inserted into compromised websites that redirects browsers to the infamous Blackhole Exploit Kit.
From Microsoft’s report
The Microsoft Security Intelligence Report takes data from over one billion sources across the Windows landscape – data was drawn from Redmond real estate such as its Malicious Software Removal Tool, Exchange Online, Windows Defender and more (see page 134) – providing an overview into the threat landscape across Windows boxes around the world. The information was collected during the first six months of 2013.
The research also looks at software vulnerabilities, software vulnerability exploits, malicious and potentially unwanted software and security vulnerabilities in both Microsoft and third-party software.
“Vulnerability disclosures across the industry decreased 1.3 per cent from 2H 2012, and 10.1 percent from 1H 2012. An increase in operating system vulnerability disclosures in 1H 2013 largely offset a corresponding decrease in application vulnerability disclosures during the same period, resulting in little overall change,” according to Microsoft.
“Overall, however, vulnerability disclosures remain significantly lower than they were prior to 2009, when totals of 3,500 disclosures or more per half-year period were not uncommon.”
Microsoft doesn’t provide a reason but El Reg‘s security desk suspects that some combination of improved security practices among vendors and the growth in the exploit marketplaces (which naturally result in lower vulnerability disclosures) is behind the change.
Application vulnerability disclosures accounted for 63.5 per cent of total disclosures for the first half of 2013. Operating system vulnerabilities accounted for 22.2 per cent of total disclosures, while browser bug reports made up the remaining 14.3 per cent.
Redmond is urging laggard Win XP users to upgrade their machines before security updates for the OS end on 8 April 2014. ®
Free Regcast : Microsoft Cloud OS
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/10/31/security_intelligence_report_microsoft/