 Vice.com’s Martin Robbins summed it up well: Wikipedia, he said, is “the world’s go-to resource for information on everything from the Boer War to fifth-season episodes of Buffy.”
Vice.com’s Martin Robbins summed it up well: Wikipedia, he said, is “the world’s go-to resource for information on everything from the Boer War to fifth-season episodes of Buffy.”
Although some internet cognoscenti cast a skeptical eye at Wikipedia, the service still garners a vast amount of trust.
That trust is based on an assumption that, ideally, Wikipedia’s content is edited, vetted, and can be reasonably relied on to be more than a collection of marketing puff pieces.
PR firms willing to make a buck out of paying clients by gaming Wikipedia’s editing processes are now threatening that trust, to the extent that alarmed watchers are predicting that, in a few years, a significant portion of the service’s content could well be spam.
Earlier in October, the Daily Dot detailed one of the most extensive sockpuppet investigations ever to be undertaken at Wikipedia, if not the largest ever.
As Wikipedia itself defines it, a sockpuppet is a false online identity assumed by a member of an internet community in order to praise, defend or support a person or organization, or to circumvent a suspension or ban from a website.
As the Daily Dot reported, nearly all of the hundreds of sock accounts uncovered by Wikipedia’s investigation shared a few traits:
Most of the pages created were about companies and living persons; the pages were generally positive and promotional in nature; they often cited articles that were written on websites that anybody could contribute to.
One of the accounts associated with what turned out to be a vast sockpuppet network was called Morning277 and had been active since November 2008.
Morning277 proved to be one busy Wikipedia beaver, logging more than 6,000 edits by the time it was investigated.
On a talk page detailing the long-term history of Morning277’s abuse of the service, Wikipedia editors say that Morning277 is associated with a group of hired writers who collaborate without ever using the talk pages to communicate with each other – a red flag for sockpuppetry.
As of September, Wikipedia had confirmed 323 sockpuppet accounts identified by the investigation, which dates to 2008, with another 84 suspected.
Wikipedia’s editors have tracked most of the entries to a US company called Wiki-PR, a firm that specializes in editing Wikipedia on behalf of paying clients.
The firm offers “Wikipedia Writers For Hire” and claims to “build, manage, and translate Wikipedia pages for over 12,000 people and companies.”
Robbins, reporting last week, noted that Wiki-PR’s promise on its Twitter profile at the time baldly stated the matter:
“We write it. We manage it. You never worry about Wikipedia again.“
Wiki-PR is unapologetic about its business model of charging for Wikipedia editing.
CEO and co-founder Jordan French said in an emailed statement that Wikipedia most certainly does allow paid editing, pointing to a policy proposal to limit paid editing on Wikipedia that had, in fact, failed to pass, given that consensus wasn’t reached in a reasonable amount of time.
In a Wikipedia entry on Wiki-PR’s editing of its pages, Wikipedia editors say that the practices of the public relations firm have contradicted the encyclopedia’s practices, including those of conflict-of-interest editing.
 The firm claims to have administrator access that enables it to manage its clients’ Wikipedia presence.
The firm claims to have administrator access that enables it to manage its clients’ Wikipedia presence.
Part of the duties of Wikipedia administrators are, of course, sockpuppet investigations.
In fact, as the Daily Dot described, the Wikimedia Foundation, a nonprofit that oversees Wikipedia and its sister sites, entrusts only a small team of vetted admins with the responsibility.
If Wiki-PR’s claims to have administrator access are true, the Daily Dot suggested, it would mean that the firm has planted “sleeper agents” among Wikipedia’s most powerful users – “a revelation that would likely send chills down the spine of any devoted Wikipedian.”
The investigation concluded that Morning277 wasn’t behind a sockpuppet network, per se.
Rather, it was “primarily a case of meatpuppetry” – i.e., when individuals promote their causes by bringing like-minded editors into a dispute.
As far as whether Morning277 is connected to Wiki-PR, French said he couldn’t really comment, given that it’s “unclear whether there is private litigation (or forthcoming private litigation) between the admin who blocked Wikipedia user Morning277 and the actual person” behind the Morning277 account.
Are you confused yet? I’m confused. Wikipedia has madly intricate editing and investigative processes, along with nomenclature to match.
Is Morning277 a sockpuppet? A meatpuppet?
The difference, to my outsider’s perspective, doesn’t amount to much. Either term refers to those with an agenda to push in the pages of Wikipedia, and that seems to be an inarguably anti-Wikipedian situation.
And again, from this outsider’s perspective, it does strike me that Wikipedia’s “bright lines” with regard to paid editing are too fuzzy and permeable for the long-term good of the service.
What do you think? Are businesses justified in hiring firms like Wiki-PR to massage their message? Or should Wikipedia firm up its bright line to resolutely disallow paid editing?
Let us know your take in the comments section below.
Image of sock puppet courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/2OHl4tcFyaw/
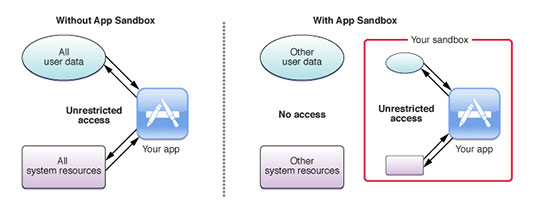
 A US man in West Haven, Connecticut has been arrested for allegedly Tweeting threats to executives, players and coaches of the
A US man in West Haven, Connecticut has been arrested for allegedly Tweeting threats to executives, players and coaches of the 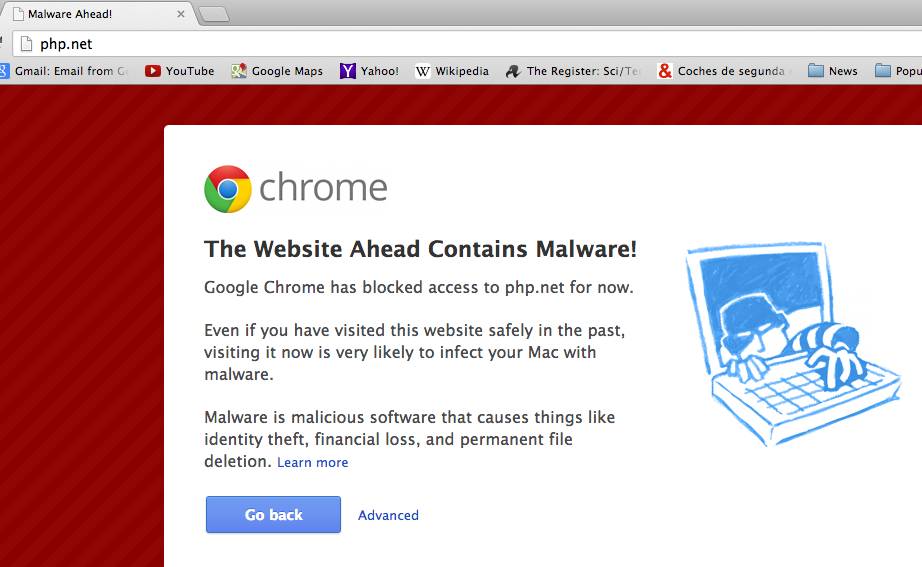
 Information security has become such a booming business that it seems there is a conference somewhere in the world every single week.
Information security has become such a booming business that it seems there is a conference somewhere in the world every single week.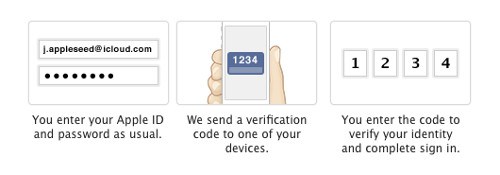
 Katalov demonstrated that by simply acquiring the Apple ID and password of another user, whether they have enabled two-factor authentication or not, he can download their iPhone/iPad/iPod backups and documents from iCloud and see their pictures, music, emails, contacts, documents, presentations, spreadsheets or anything else without the victim being alerted.
Katalov demonstrated that by simply acquiring the Apple ID and password of another user, whether they have enabled two-factor authentication or not, he can download their iPhone/iPad/iPod backups and documents from iCloud and see their pictures, music, emails, contacts, documents, presentations, spreadsheets or anything else without the victim being alerted. Vice.com’s Martin Robbins
Vice.com’s Martin Robbins  The firm claims to have administrator access that enables it to manage its clients’ Wikipedia presence.
The firm claims to have administrator access that enables it to manage its clients’ Wikipedia presence.