MoJ fined £140K for EMAILING privates of 1,000 inmates
Email delivery: 4 steps to get more email to the inbox
A monumentally silly clerical error led to the personal details of all the prisoners serving at HMP Cardiff being emailed to three of the inmates’ families.
Data watchdogs at the Information Commissioner’s Office (ICO) have slapped a £140K fine on the Ministry of Justice over the serious data breach, which was only discovered after one of the recipients of the August 2011 mailout contacted the prison.
An email from the prison clerk about an upcoming visit had apparently included a file containing the inmates’ details. “The file included a spreadsheet containing sensitive information including the names, ethnicity, addresses, sentence length, release dates and coded details of the offences carried out by all of the prison’s 1,182 inmates,” the ICO reports.
An internal investigation discovered that the same massive slip-up had occurred TWICE before within the previous month, with details sent to different inmates’ families. Both of the previous incidents went unreported. Each of the three breaches arose because of the same mistake by the same untrained member of staff, an investigation (PDF) concluded.
A request for a booking had been made by a family member of an inmate. The clerk had intended to send him an email about the visit. In doing so, she accidentally “pasted” a text file containing the details of the inmates at the prison as an attachment to the email. The two prior incidents had occurred as a result of the same mistake, by the same clerk.
The police and a member of the prison’s staff were sent to the recipients’ home addresses following the incident to ensure the files had been deleted. The unauthorised disclosures were reported to the ICO in September 2011.
The ICO’s investigation blamed the problem on a “clear lack of management oversight at the prison, with the clerk working unsupervised despite only having worked at the prison for two months and having limited experience and training”. A lack of audit trails or other checks also meant that the disclosures would have gone unnoticed if they hadn’t been reported by one of the recipients.
The investigation also found fault in how prisoners’ records were handled, with unencrypted floppy disks regularly used to transfer large volumes of data between the prison’s two separate networks, Quantum (a secure and restricted network) and a less secure systems used for booking visits.
The prisoner data is stored on a database which is held on a network system called Quantum. It is a secure accredited network system meeting HM Government IT standards for handling information up to a RESTRICTED marking, and access to it is strictly controlled.
There is a separate non-networked system, the biometrics system, used for booking and processing visits, and other security-related matters for prisoners. The two systems are physically separate. There are daily transfers of data from the Quantum system to update the biometrics system, to facilitate visits and other prisoner movements.
The only way the information can be transferred from the Quantum system to the biometrics system is to carry out a ‘profile dump’ of all inmate details. The transfer is done at the start of each day by the booking clerk who locates the text file via Windows Explorer on the Quantum system and then, using the ‘copy and paste’ function, places the file on an unencrypted floppy disc.
ICO deputy commissioner and director of data protection, David Smith, said: “The potential damage and distress that could have been caused by this serious data breach is obvious. Disclosing this information not only had the potential to put the prisoners at risk, but also risked the welfare of their families through the release of their home addresses.
“Fortunately it appears that the fall-out from this breach was contained, but we cannot ignore the fact that this breach was caused by a clear lack of management oversight of a relatively new member of staff. Furthermore the prison service failed to have procedures in place to spot the original mistakes.
“It is only due to the honesty of a member of the public that the disclosures were uncovered as early as they were and that it was still possible to contain the breach,” he concluded.
The ICO fined the Ministry of Justice because the National Offender Management Service, which is responsible for commissioning and delivering prison and probation services across England and Wales, is an executive agency of the government department. ®
Free Regcast : Microsoft Cloud OS
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/10/22/inmate_detail_mailout_data_breach/
 A job interview is a difficult way to find out whether a job candidate will wind up doing a good job if he or she gets hired.
A job interview is a difficult way to find out whether a job candidate will wind up doing a good job if he or she gets hired. 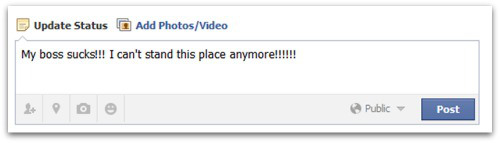
 Keeping things tucked down on Facebook and other social media spaces is a baseline way to attempt to maintain your privacy, but keep in mind that privacy isn’t legally guaranteed in all countries or in all US states.
Keeping things tucked down on Facebook and other social media spaces is a baseline way to attempt to maintain your privacy, but keep in mind that privacy isn’t legally guaranteed in all countries or in all US states. 