 A 15-year-old Canadian girl from Nova Scotia has pleaded guilty to a vicious, planned attack on a female, autistic student, and an attorney is seeking to ban her from social media as part of her sentencing.
A 15-year-old Canadian girl from Nova Scotia has pleaded guilty to a vicious, planned attack on a female, autistic student, and an attorney is seeking to ban her from social media as part of her sentencing.
Steve Drake, Novia Scotia Crown attorney, said that the girl should be barred from online venues including Facebook, Twitter and Instagram, lest she perpetrate cyber bullying, according to CBC News:
Social media is a reality. Facebook might be a staple in the social lives of young people but if it’s used as a vehicle for the commission of crime, what I said to the court is that someone should take away the key.
Drake said that the 15-year-old – whom, Drake said, police described as the “bully of all bullies” – planned the attack for lunchtime.
She forced a second student to film the attack and to post it on Facebook.
The prosecutor’s description of the assault, which took place at Sherwood Park Education Centre in Sydney earlier this year:
The accused stood and waited for the victim to come through the hall at lunchtime, stated her name and then sucker punched her, knocked her on the floor and proceeded to grab her by the hair and kick her in the head and facial area.
It all happened in approximately 10 to 12 seconds. It was brutal.
It was mere luck that the victim only suffered bruises, Drake said.
CBC News reports that the Crown and defence have requested a lengthy probation period for the girl. A sentence is expected on 30 October.
Nova Scotia has been shaken in the past year by cyber bullying, including the tragic death of Rehtaeh Parsons.
Rehtaeh, of Nova Scotia, committed suicide in April at the age of 17 after allegedly being gang-raped by four boys.
Two 18-year-old Canadian men were arrested in August and charged with child abuse images crimes over allegedly cyber bullying the young woman.
Three weeks after Rehtaeh’s death, Nova Scotia legislators announced the new Cyber-Safety Act.
Part of the act was an anti-cyber bullying law, put into effect in August, that enables victims to apply for protection orders and gives them the ability to identify and sue alleged cyber bullies.
The law’s intent, of course, is to protect victims and to hold bullies – and even their parents – responsible.
It has come under fire, however, for being overly broad, threatening the rights of free expression, and for giving already difficult children the tools to financially ruin their parents.
Jesse Brown, writing for Macleans, said this is how the Cyber Safety Act will attempt to stop online abuse:
Someone feels that you’re cyberbullying them. They visit or phone the court and request a protection order against you (minors, or some reason, cannot do so, only adults). A judge decides if their claim meets the law’s definition. The definition of cyberbullying, in this particular bill, includes ‘any electronic communication’ that ‘ought reasonably be expected’ to ‘humiliate’ another person, or harm their ’emotional well-being, self-esteem or reputation.’
If this is the standard, I don’t know a person who isn’t a cyberbully.
Drake believes this is the first time in Nova Scotia that a social media ban has been requested in such a case, but said that a judge ordered a 12-year-old Manitoba girl to stay off Facebook while she spends a year on probation for online threats against two other girls.
As far as whether social media bans are enforceable, Drake likened it to banning a drunk driver from climbing back behind the wheel or from taking another drink.
In this case, social media can be monitored by a vigilant public, he said:
At some point in time if you’re on Facebook, people will know and if someone who’s interested in making sure that this probation order is enforced sees that the person’s on Facebook, no different than someone driving along the highway and calling in a drunk driver.
There are many well-intentioned efforts at play in this case. It’s a relief to see such efforts devoted to protecting children before a victim turns into yet another suicide, such as the recent, heartbreaking case of Rebecca Ann Sedwick.
It strikes me as common sense that the earlier the intervention, the more likely that cyber bullying won’t result in suicide.
It might be a natural reaction to vent fury at the parents of bullies, but perhaps a more effective approach to cyber bullying would be to demand that social networks such as Facebook or Tumblr respond quickly and decisively to shut it down as soon as it’s discovered.
I’m thinking here of a 2011 case wherein a Facebook page was set up to bully a New Zealand college student.
As the New Zealand Herald reported at the time, the page – called “Putting your stick away after a hard day of being a social outcast” – was set up by a fellow student and featured a photo of the targeted boy.
It was taken down after sparking internet furor, the paper reported.
Supporters and anti-bullying campaigners took to online parenting forums, urging people to contact Facebook to have the page removed. The supporters posted hundreds of responses decrying the bullying, resulting in the Facebook page being taken down.
That happened, the paper said, within the span of 3 hours.
Unfortunately, many of the anti-bullying posters themselves used bullying language on the bullies.
This has been a hard week, between this case and the arrest of two Florida girls, one of whom bragged about cyber-bullying Rebecca Sedwick.
Before you vent your fury at this 15-year-old Nova Scotia girl, or at her parents, or the Florida girl or her parents, or anybody, for that matter, please, maintain calm.
Remember people can be good.
It’s up to all of us to keep an eye out for bullying and to address it quickly, firmly, and to do so without becoming bullies ourselves.
Image of no entry sign courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/u2rGTYdH7pk/


 For example, we’ve had
For example, we’ve had 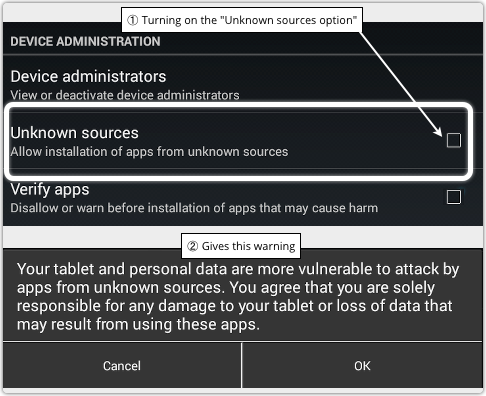
 Just about two years ago, Google’s Open Source Programs Manager, Chris DiBona, came out with am extraordinary claim.
Just about two years ago, Google’s Open Source Programs Manager, Chris DiBona, came out with am extraordinary claim. Google has
Google has  A
A  A 15-year-old Canadian girl from Nova Scotia has pleaded guilty to a vicious, planned attack on a female, autistic student, and an attorney is seeking to ban her from social media as part of her sentencing.
A 15-year-old Canadian girl from Nova Scotia has pleaded guilty to a vicious, planned attack on a female, autistic student, and an attorney is seeking to ban her from social media as part of her sentencing. If you like to stand out from the crowd then you may have taken the decision to set yourself apart from the legions of Android users and iOS fans when it came to choosing a tablet.
If you like to stand out from the crowd then you may have taken the decision to set yourself apart from the legions of Android users and iOS fans when it came to choosing a tablet.