Next Generation For SIEMs? Ease Of Use, Analyze More Data
The next generation of security information and event management (SIEM) systems will inevitably include new features, but security companies are currently focused on solving their customers problems in managing and operating the current crop of products.
While SIEM systems have been around for more than decade, companies continue to have troubles deploying and maintaining the systems. More than half of businesses need at least a pair of full-time analysts to operate the systems, while 44 percent required more than a few weeks to deploy their SIEM system, according to a survey by security-management firm EiQ Networks.
Those problems have made creating an easy-to-use SIEM system the most requested feature for the future, says Nicole Pauls, director of product management for IT-management firm SolarWinds.
“We are trying to adapt to an evolving threat space, and it does not require that we cobble together new tools,” she says. “What it really requires is that we make the tools better, so we can adapt to the threat space faster.”
With security experts recommending that companies continuously monitor their networks to gain better visibility into potential threats, more businesses are considering SIEM systems or have already embarked on network-monitoring projects. No wonder: The deployment of security-intelligence systems continues to be the top strategy for reducing the costs of a breach, correlating with a $4 million reduction in breach costs, according to the Ponemon Institute’s Cost of Cybercrime study released this month.
Yet, SIEM deployments are difficult. The complexity of integrating a variety of different data feeds requires knowledgeable security analysts. Add to that the problems in getting all the necessary stakeholders in a company to cooperate, and plenty of SIEM projects have stalled, says Mark Nicolett, managing vice president of network security for business intelligence firm Gartner. Unfortunately, vendors typically tow a marketing line of easy deployment, rather than frankly discuss the difficulties of deploying the analysis environment.
“I don’t think it is possible to ask the vendor the right set of questions to determine how difficult the deployment is going to be,” Nicolett says, adding that–without easier deployments–adding more features is a non-starter. “It is all fun to talk about what is coming next, but if it is not operational useful, who cares.”
[A high rate of false positives is a problem that affects many types of security systems, but a few proactive steps can help cut them down to size. See 3 Steps To Keep Down Security’s False-Positive Workload.]
While the marketing lines for most security-intelligence product makers may not change, executives know that they must tame the unruly learning curves of their SIEM products or risk falling behind in the market.
“There is still a lot of the vision of SIEM that has yet to be realized–things like behavioral analysis and better correlation of events,” say SolarWinds’ Paul. “We need to give customers better analysis out of the box.”
To deliver better analysis, SIEM vendors and service providers are aiming to allow companies to easily incorporate more data, threat-intelligence feeds and other information into the SIEM systems. Yet, the products also have to take into account the context of the data and the risks that a company faces, says Vijay Basani, president and CEO of EiQ Networks, a security-management services provider.
“We can take gobs of data, and spit out lots of information, but we don’t know what is important for your company,” he says. “I think that is going to change very dramatically. Approaches, like focusing on best practices, will help companies focus on the right questions.”
A large part of the move to incorporating more data in future SIEM offerings is pairing the appliances and services with a threat-intelligence feed. A number of vendors have launched threat information sharing exchanges and forums where security experts can work together on the analysis. AlienVault has the Open Threat Exchange, CyberSquared has developed Threat Connect, and Hewlett Packard recently announced Threat Central. The services combine malware analysis and open-source intelligence tools with social networking and crowdsourced analysis to create a virtual space for learning about the latest threats.
Whether Balkanized analysis environments will deliver the features needed to fuel better SIEM products is another question. Eric Schou, director of product marketing for enterprise security products at HP, believes the crowdsourced model will work because it gives each participant more value than they typically put in.
“If there isn’t that value and if they don’t feel like it improves their security posture, then they won’t take part,” says Schou.
Yet, the crowdsourced model and a mountain of threat data may not improve the effectiveness of SIEMs, warns Gartner’s Nicolett. More data is not necessarily a good thing, when you cannot even properly analyze what you have, he says.
“We are not suffering from a lack of data,” he says. “We are suffering from a lack of intelligence in analyzing it.”
If next-generation products can deliver that combination of intelligence and usability, only then will companies benefit.
Have a comment on this story? Please click “Add Your Comment” below. If you’d like to contact Dark Reading’s editors directly, send us a message.
Article source: http://www.darkreading.com/monitoring/next-generation-for-siems-ease-of-use-an/240162875
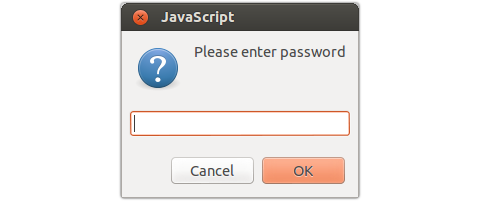
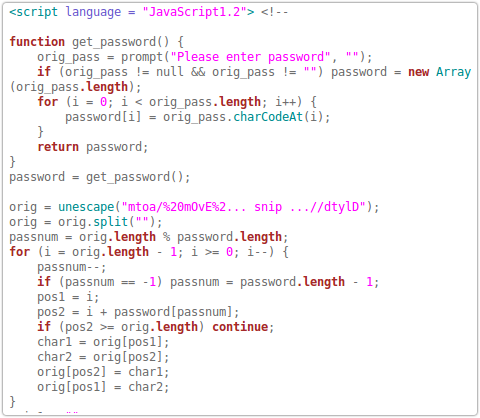
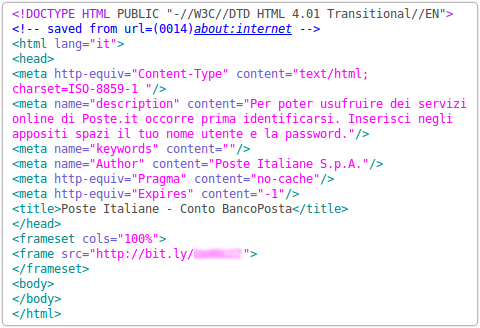
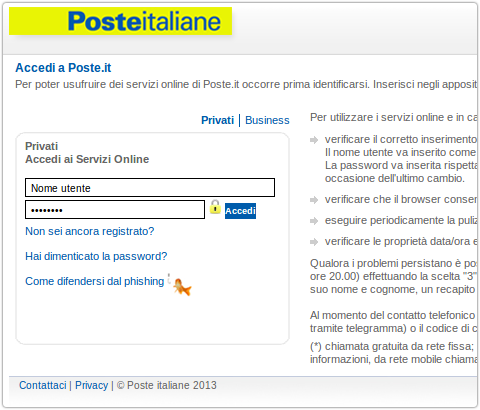
 Earlier this week a colleague pointed out an intriguing phishing sample that he had come across.
Earlier this week a colleague pointed out an intriguing phishing sample that he had come across. 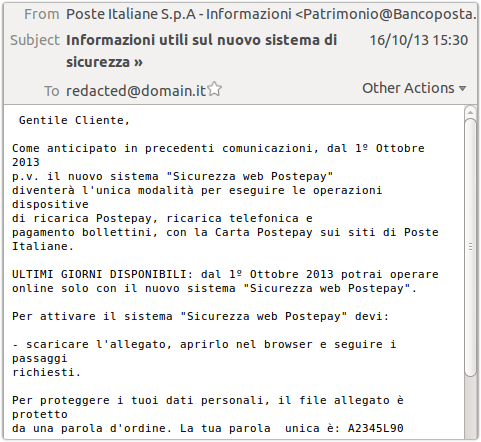
 Continuing with my “extra” Chet Chat podcasts when there are special occasions, this week I interviewed Robert Slade for advice on how to stay safe for National Cyber Security Awareness Month #NCSAM.
Continuing with my “extra” Chet Chat podcasts when there are special occasions, this week I interviewed Robert Slade for advice on how to stay safe for National Cyber Security Awareness Month #NCSAM.