How much is a tiger worth?
How much is a tiger worth?
For a poacher, these extremely endangered animals are enormously profitable.
According to the World Wildlife Fund, parts from a single tiger can fetch as much as $50,000 on the black market.
I can’t verify these claims, so take them with a grain of salt, but for what it’s worth, one site, TigersInCrisis.com, says that in Taiwan, a bowl of tiger penis soup (to boost virility) goes for $320, and a pair of tiger eyes (to fight epilepsy and malaria) for $170. Powdered tiger humerus bone (for treating ulcers, rheumatism and typhoid) brings up to $1,450 per lb. in Seoul, the site claims.
The internet, unfortunately, has facilitated this enormously profitable wildlife trafficking.
Special agents with the US Fish and Wildlife Service, for example, began spotting online sale postings for frozen tiger cubs in the late 1990s.
The wildlife-trade monitoring network TRAFFIC found, as of July 2012, 33 tiger products on Chinese online auction websites, including bracelets, pendants, and tiger-bone glue. According to National Geographic, ads even promoted “blood being visible in items.”
Such online sales are part of a much larger wildlife-trafficking industry, which WWF estimates to be worth $7.8 to $10 billion per year.
The WWF estimates that there are now as few as 3,200 tigers left in the wild, while TRAFFIC puts it at 2,500 breeding adult tigers, with the number on the decline.
Those precious few are watched over with considerable anxiety by conservationists.
Therefore, it is understandable that when the head of the monitoring program at Panna Tiger Reserve in central India was alerted in July to an attempt to break into his professional email account – the inbox of which contains the encrypted geographic location of a GPS-collared, endangered Bengal tiger – a frightening new term for a very specific form of internet crime came into being.
The term: cyber poaching.
The head of the monitoring program, Krishnamurthy Ramesh, told National Geographic that the attempted break-in was promptly prevented by the organisation’s server.
National Geographic reports that even if the GPS data had been obtained, it was encrypted and could only be decoded with two data sets: “specialized data-converter software” and specific information from the radio-collar product worn by the tiger in question.
He said:
“They couldn’t even see the data—it would look like unusual numbers or symbols.”
I hope he’s right. After all, as Paul Ducklin said when Adobe was breached earlier this month, when it comes to encryption, the devil’s in the details – details that may include what salting, hashing and stretching algorithms are used, for example. (See Paul’s article for an explanation of these encryption intricacies.)
Does that even come into play when you’re talking about “specialized data-converter software” and specific information from the collar itself?
I hope, for the tiger’s sake, that Ramesh is right, and that the creature’s whereabouts is in data that’s safely tucked away.
That tiger, designated Panna-211, is a 2.5-year-old male who in February 2013 was fitted with a nearly $5,000 collar outfitted with both satellite and ground-tracking capabilities.
The collar, which lasts about eight months, was configured to provide GPS data every hour for the first three months and every 4 hours for the next 5 months.
Computerworld’s Darlene Storm, in her coverage of the story, linked to Telemetry Solutions, a vendor of GPS collars and pods for tracking large mammals.
Telemetry Solutions’s large GPS collar is advertised as providing accuracy within 2.5 meters, or about 8.2 feet.
That sounds like it’s plenty close enough to suit a poacher.
National Geographic reports that the battery for the tiger’s collar expired in July, and the satellite feedback in the collar stopped working.
Around the same time, Ramesh was alerted that someone in Pune—more than 620 miles (1,000 kilometers) away from his office in Dehradun—had tried to access his email.
Was it a poacher with hacking skills, trying to access the GPS location data for a very valuable target? Or was it merely an innocent mistake?
It’s unknown.
But the mere possibility of online data about endangered species falling into the wrong hands was enough for the forest department of the state that contains the reserve to start an inquiry, in collaboration with police.
Whether or not the incident points to the emergence of so-called cyber poachers, experts say that wildlife criminals are growing increasingly tech-savvy.
Wildlife-governance specialist Andrew Zakharenka, of the US-based Global Tiger Initiative, told National Geographic that as internet connectivity and wealth has increased in developing countries, so too has demand increased for the perceived luxury goods of wildlife products.
That demand coincides with criminals using cell phones, SIM cards, and email, as well as online black markets for wildlife goods.
We’ve previously seen GPS hacked in theoretical scenarios, such as in July, when University of Texas/Cockrell School of Engineering graduate students hijacked an $80 million yacht by spoofing GPS signals.
Students from the engineering school did the same thing to a drone in June 2012.
Criminals may also have tracked a burglary victim by sticking GPS devices on her car so they could determine when her house would likely be empty and they might best break in.
Is one isolated attempt to break into an inbox containing encrypted GPS data for a rare, profitable target – an endangered Bengal tiger – enough to warrant the coining of a new term for an exotic new type of cyber criminal that could well be entirely hypothetical?
I don’t know.
But, given the facts – criminals are increasingly tech-literate, the wildlife market is extremely profitable, and some forms of GPS equipment have proved to be hackable – I would refrain from saying that conservationists are overreacting.
With as few as 2,500 tigers left, and numbers dwindling, the stakes are too high not to take even the most unlikely threats very seriously.
National Geographic reports that since the possible hacking attempt, the collared tiger has been seen more than three times and photographed twice.
A dedicated team now stays within 1,600 feet (500 meters) of the tiger at all times to deter poachers.
In January, the conservationists at the reserve will deploy surveillance drones and wireless sensors to detect human intrusions into the forest.
As Ramesh told National Geographic, if conservationists’ worst fears about technology-enhanced poaching do come to pass, the cyber poachers will be, in turn, battling technology-enhanced warriors, fighting on behalf of tigers.
Let’s hope the cyber conservationists win.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/gdtu-ROGixM/
 Organised crime is becoming increasingly entwined with hacking, creating a “service-orientated industry” and making the internet “the single most important” factor facilitating major organised crime and drug trafficking, according to the head of Europol.
Organised crime is becoming increasingly entwined with hacking, creating a “service-orientated industry” and making the internet “the single most important” factor facilitating major organised crime and drug trafficking, according to the head of Europol. Rebecca Ann Sedwick, a 12-year-old Florida girl,
Rebecca Ann Sedwick, a 12-year-old Florida girl,  How much is a tiger worth?
How much is a tiger worth?
 News has been spreading that Twitter is
News has been spreading that Twitter is 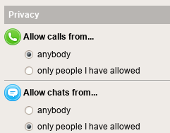 Other services that allow for private messaging have had to implement the blocking of unsolicited messages. If Twitter changes this option to be the new default it will likely end in tears.
Other services that allow for private messaging have had to implement the blocking of unsolicited messages. If Twitter changes this option to be the new default it will likely end in tears.