4 free tools for Cyber Security Awareness Month
 Regular readers of Naked Security will know that we aren’t terribly prone to commercialism.
Regular readers of Naked Security will know that we aren’t terribly prone to commercialism.
We don’t think we need to be.
The brand we represent is pretty obvious, what with the domain name nakedsecurity.sophos.com and the corporate logo on every page, where we say, “Award-winning news, opinion, advice and research from SOPHOS.”
Nevertheless, we’d like to use this article to offer you some free Sophos stuff.
Here’s why we’ve decided to do this right now:
- It’s half way through National Cyber Security Awareness Month.
- We’ve been urging you do DO THESE 3 things, including making sure you seek out and get rid of any malware lurking on your computer.
- As a result, numerous people, from readers to journalists, have been asking, “Where would you sugggest that I start?”
- We’ve been encouraging techies who act as unofficial home IT support to help their friends and family with item (2).
- They’ve been asking, “Where would you sugggest that I start?”
So here is a brief and, we trust, unpushy list of four free tools you can find on our website.
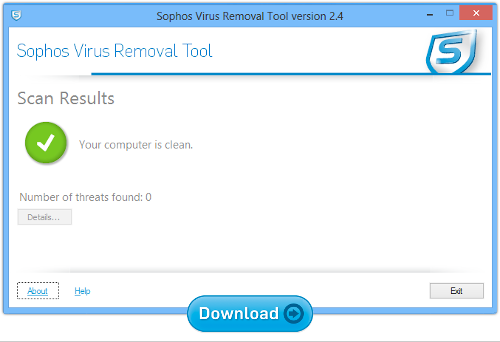
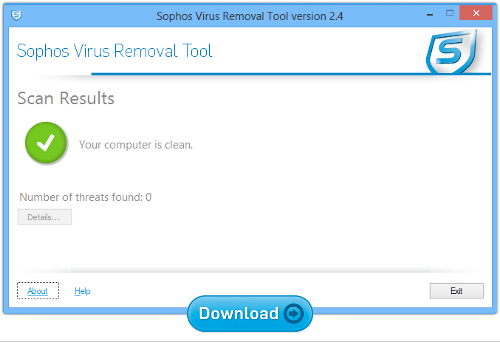
Sophos Virus Removal Tool
This is a simple and straightforward tool for Windows users. It works alongside your existing anti-virus to find and get rid of any threats lurking on your computer.
It does its job without requiring you to uninstall your incumbent product first. (Removing your main anti-virus just when you are concerned about infection is risky in its own right.)
Download and run it, wait for it to grab the very latest updates from Sophos, and then let it scan through memory and your hard disk. If it finds any threats, you can click a button to clean them up.
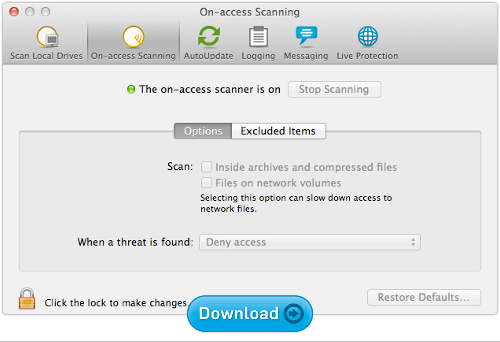
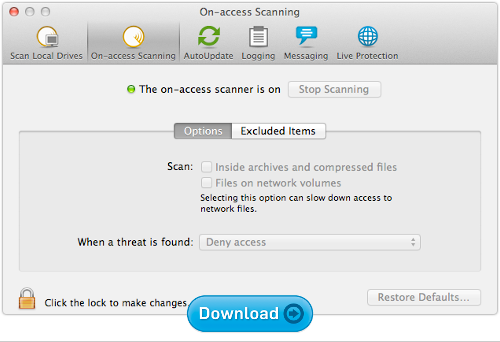
Sophos Anti-Virus for Mac Home Edition
Yes, Macs get viruses too.
And even if you never see a virus that directly attacks your Mac, the chances are good that you’ll encounter malware from your Windows-using friends (or even from your own Windows partition, if you dual-boot your Mac).
Sophos for Mac stops threats for Windows and Mac alike, protecting you and those you share files with.
Choose from blocking viruses in real time (on-access protection), scanning at scheduled times, or running a check whenever you want.
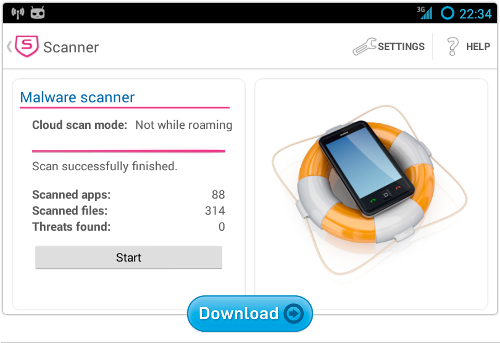
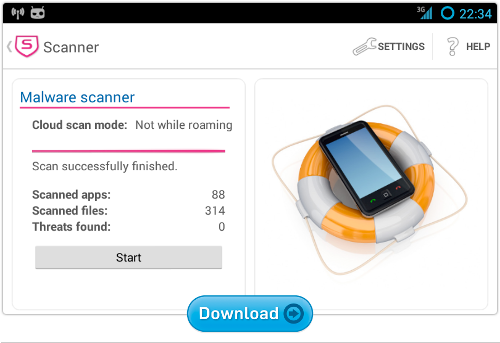
Sophos Mobile Security for Android
Our Sophos Mobile Security app protects your Android device without reducing performance or battery life.
Using up-to-the-minute threat data from SophosLabs, we automatically scan apps as you install them.
As well as malware protection, you’ll also get: loss and theft protection with remote lock and wipe, a security advisor to alert you if you inadvertently activate risky configuration settings, and a privacy advisor to help you decide whether an app is asking for permission to do too much.
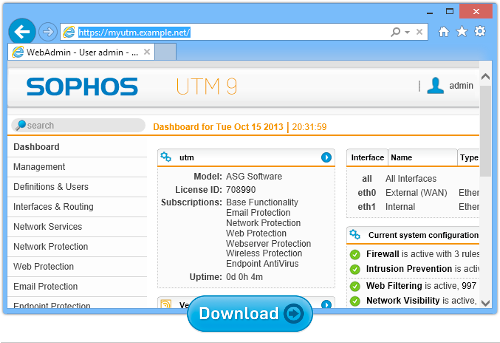
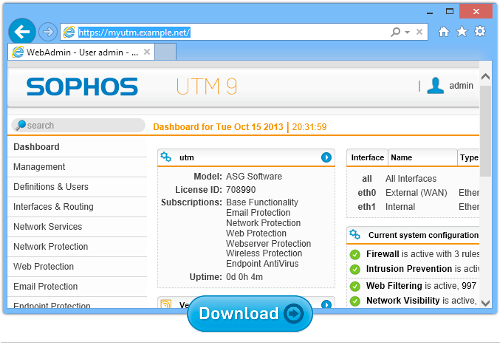
Sophos UTM Home Edition
You’ll need a spare computer to install it on, and you’ll probably want to get your unofficial home support techie to set it up for you, but if you do, you’ll have our award winning network security device for businesses, 100% free for home use.
That includes all the Sophos UTM features: email scanning, web filtering, a VPN, web appplication security, and everything you need to keep up to 50 devices on your home network secure.
In you live in a shared house, or you have children to look out for online, this could be just the product you need.
Better yet, you get 12 free licences for Sophos Anti-Virus for Windows that you can install and manage throughout your household, right from the UTM web console.
You can get any or all of these tools free of charge from our website.
Only the UTM requires registration – we need an email address so we can send you a licence key. For the others, we don’t even ask who you are.
So, if you’ve been thinking, “I really ought to get more serious about cybersecurity,” just remember that there’s no time like the present.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/upChQmTD6T0/

 I heard that Oracle won the America’s Cup recently which leads me to give them some unsolicited advice.
I heard that Oracle won the America’s Cup recently which leads me to give them some unsolicited advice.  Regular readers of Naked Security will know that we aren’t terribly prone to commercialism.
Regular readers of Naked Security will know that we aren’t terribly prone to commercialism.