BullGuard Launches New Version Of Internet Security Software Suite
LONDON, October 15, 2013 /PRNewswire/ —
Elegantly simple interface for all levels of users, enhanced behavioural detection – and vulnerability detection, backups and tune-ups that run silently in the
background with minimal impact on system resources
– Improved behavioural detection engine identifies new threats and prevents
zero-day attacks*
– Enhanced user interface similar provides intuitive one-click functions for all
features
– Updated backup, tune-up and vulnerability scanner for faster and more
intuitive operation
– Silently runs in the background, identifying vulnerabilities and protecting
with minimal impact on the system
– Basic and advanced modes for all levels of user expertise
– Free 24/7 support and free upgrades
BullGuard [http://www.bullguard.com ] a global leader in internet and mobile security, has today announced the release of the new version of BullGuard Internet Security [http://www.bullguard.com/products/bullguard-internet-security.aspx ], its most progressive and intuitive security suite to date.
(Photo: http://photos.prnewswire.com/prnh/20131015/647332 )
BullGuard Internet Security is designed to offer industry-leading protection, silent and efficient background operation and to appeal to any level of user ability.
Alex Balan, Head of Product Management, BullGuard, said: “It is our most advanced security suite yet, and one that offers a significantly improved degree of control and operation.”
Improved behavioural detection
Notable enhancements include advancements in the behavioural detection engine which can prevent zero-day malware threats. Additional tools include a smart-filter for safe browsing, an advanced firewall and protection against Advanced Persistent Threats (APTs) and Targeted Attacks.
An all-new user interface and improvements to usability means default functions for all the key tools in Internet Security are accessible with one click.
Further control is available directly through the main interface.
Easy to use
Importantly, BullGuard Internet Security is designed to be used by anyone, from the complete novice to those who like to retain full control over the minutiae of system security. A choice of basic or advanced setting displays ensures that unnecessary or unwanted functions are hidden from sight to simplify core operation for new users, while those who desire more advanced control will find access to an impressive level of fine-tuning.
Redesigned backup
BullGuard Internet Security retains the rich array of tools that go beyond core security, helping to make it the most complete solution for system protection and maintenance on the market. A 5GB Backup module has been redesigned from the ground up so users can easily create a backup of a file or folder that is regularly synchronised with BullGuard’s servers.
Silent and efficient background scans
Before installation begins, the software scans a system for potential threats and eliminates any detected malware to ensure a system is clean. The installation process is streamlined to require virtually no user interaction.
When installed, BullGuard Internet Security regularly scans a system and performs automatic maintenance tasks such as vulnerability detection, backup and tune-up quietly in the background without using up valuable system resources or interrupting the user.
Building on a strong reputation
Balan adds: “As ever, we’ve placed a strong focus on ensuring that our excellent reputation in the security market remains intact by revising and improving core security. We’ve also further improved usability by ensuring that the majority of tasks can be set to run in the background, with as little user interaction and impact on system resources as possible. In short, once installation is complete a user can let it do its job with minimal interaction.”
Improving on its predecessors wasn’t easy. Over the last four years BullGuard has never missed a Virus Bulletin VB100 award. We also consistently score in the top three, in tests by independent assessors AV-TEST Lab and AV-Comparatives.
In addition to the improvements, all of the regular tools BullGuard Internet Security users have come to expect are present, including a powerful Spamfilter, advanced parental controls, a game mode and free 24/7 support for help with any of the software’s features or advice on threats and general security issues.
New BullGuard Internet Security is available for GBP44.95 for up to three users, with free upgrades to new versions. For more information visit http://www.bullguard.com.
* Zero-day attacks are new types of malware that have just been created and as a result their ‘signature’ is not yet known. At a general level they are difficult to protect against because they haven’t yet been identified which means many computers are potentially vulnerable.
About BullGuard:
Launched in 2002, BullGuard is one of the fastest growing internet and mobile security brands. Today, its product portfolio also includes award-winning antivirus, premium 24/7 protection suite, web-based identity and social media protection that works across all devices, as well as PC and mobile backup software solutions. BullGuard’s philosophy has always remained the same – to combine technical excellence with a genuine understanding of consumer needs, creating simple, easy-to-use products that deliver complete protection, and to enable customers to control and manage their digital footprint.
For two consecutive years (January 2012 and 2013), BullGuard Internet Security has won a coveted “Best Buy” award from Which?. BullGuard Internet Security comes with an award-winning Antivirus program, Parental Control and Online Backup for your most valued files and precious photos.
Article source: http://www.darkreading.com/applications/bullguard-launches-new-version-of-intern/240162678
 Some Google users who don’t want their faces used to pimp bagel shops (or spas, or Nexus 7, or whatever ads Google can squeeze money out of) are replacing their photos with
Some Google users who don’t want their faces used to pimp bagel shops (or spas, or Nexus 7, or whatever ads Google can squeeze money out of) are replacing their photos with 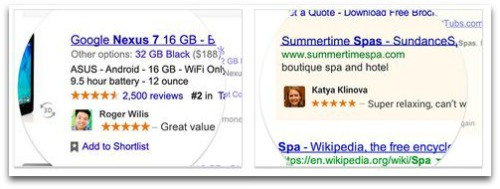
 Members of the embedded systems hacker collective /dev/ttys0 spend their time playing around with devices like home routers and set-top boxes.
Members of the embedded systems hacker collective /dev/ttys0 spend their time playing around with devices like home routers and set-top boxes. We’ve talked about how the Wi-Fi Protected Setup (WPS) feature, intended to improve security, typically makes your wireless access point
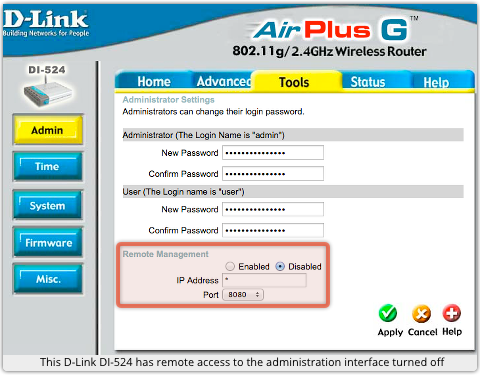
We’ve talked about how the Wi-Fi Protected Setup (WPS) feature, intended to improve security, typically makes your wireless access point 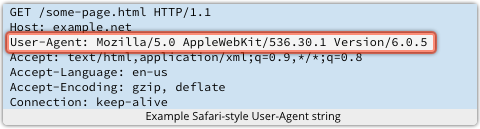
 Yahoo has confirmed it will finally enable encryption by default for its web-based email starting on 8 January 2014, according to
Yahoo has confirmed it will finally enable encryption by default for its web-based email starting on 8 January 2014, according to