New Barracuda NG Firewall F600 Models Launched
Campbell, Calif. – October 15, 2013 – Barracuda Networks, Inc., a leading provider of security and storage solutions, today announced the availability of five new models of the Barracuda NG Firewall F600, all with increased performance. The F600 models feature new, multiple port options and hot-swappable power supplies to accommodate varying network requirements.
With configuration options of 1 GbE copper, 1 GbE fiber-optic and 10 GbE fiber-optic interfaces, the new product range is ideal for internal LAN segmentation – and fast access to internal resources such as applications, print servers and databases. The models also allow rule-based traffic intelligence with WAN optimization, WAN compression and link management to ensure the best use of bandwidth across all locations. Integrated, rack-friendly, redundant power supplies can be included for organizations requiring high fail-safe performance and high availability. IT administrators benefit from easy, centralized management and affordable pricing without limitations on the number of users.
“The new Barracuda NG Firewall F600 models offer powerful next-generation firewall capabilities, with variable port options – up to 2 ports 10 GbE fiber – and fail safe security thanks to redundant power supplies,” said Klaus Gheri, VP Network Security, Barracuda. “This combination makes the new F600 models a great solution for networks requiring high performance and high availability at a very reasonable price.”
Key highlights of the Barracuda NG Firewall F600 models include:
Firewall throughput: up to 5.7 Gbps
VPN throughput: up to 1.6 Gbps
IPS throughput: up to 2.6 Gbps
Up to 400,000 simultaneous sessions
Up to 35,000 new sessions per second
Internal dual hot-swappable power supplies (optional)
Multiple port options:
Standard 8 ports 1 GbE copper
+4 ports 1 GbE copper or
+4 ports 1 GbE fiber or
+2 ports 10 GbE fiber
Pricing and Availability
The new F600 models of the Barracuda NG Firewall are available immediately. The US list price for the Barracuda NG Firewall F600 models starts at $8,999 USD for the appliance and US list price of $1,599 USD for Energize Updates. An optional Instant Replacement subscription featuring priority replacement of failed hardware and complimentary refresh of four-year old hardware units is available starting at US list price of $1,599 USD per year. International pricing and availability vary by region.
Resources
Images: Barracuda NG Firewall 5.4 images can be downloaded at – http://bit.ly/ngfwf600
Latest Blog Post: New Features in Barracuda NG Firewalls – https://www.barracuda.com/blogs/pmblog?bid=2140
Product Blog: The Barracuda NG Firewall blog provides ongoing updates, commentary and analysis related to Barracuda’s NG Firewall product suite – http://bit.ly/ngfirewall54
About Barracuda NG Firewall
The Barracuda NG Firewall is an enterprise-grade network firewall that combines comprehensive next-generation firewall capabilities – based on application visibility and user-identity awareness – with optimal efficiency and throughput. The Barracuda NG Firewall meets the enterprise requirements of massive scalability, easy and efficient management across dispersed networks, low resource consumption, and high performance for business-critical applications. Coordinated WAN optimization, centralized management and cloud-hosted content filtering and reporting are just a few of the key features. The Barracuda NG Firewall is also available as a virtual appliance. To learn more, visit: www.barracuda.com/ngfirewall.
About Barracuda Networks, Inc.
Protecting users, applications, and data for more than 150,000 organizations worldwide, Barracuda Networks provides powerful, easy-to-use, affordable IT solutions. The company’s customer-centric business model focuses on delivering high-value, subscription-based IT solutions for security and storage. For additional information, please visit http://www.barracuda.com or on Twitter: @barracuda.
Article source: http://www.darkreading.com/perimeter/new-barracuda-ng-firewall-f600-models-la/240162624
 Some Google users who don’t want their faces used to pimp bagel shops (or spas, or Nexus 7, or whatever ads Google can squeeze money out of) are replacing their photos with
Some Google users who don’t want their faces used to pimp bagel shops (or spas, or Nexus 7, or whatever ads Google can squeeze money out of) are replacing their photos with 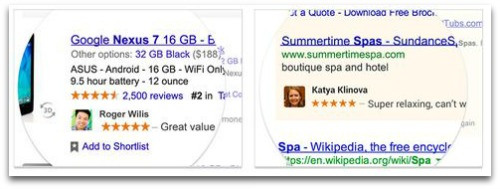
 Members of the embedded systems hacker collective /dev/ttys0 spend their time playing around with devices like home routers and set-top boxes.
Members of the embedded systems hacker collective /dev/ttys0 spend their time playing around with devices like home routers and set-top boxes. We’ve talked about how the Wi-Fi Protected Setup (WPS) feature, intended to improve security, typically makes your wireless access point
We’ve talked about how the Wi-Fi Protected Setup (WPS) feature, intended to improve security, typically makes your wireless access point 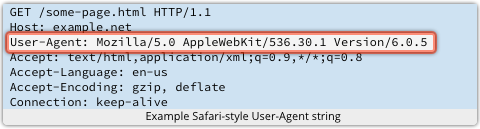
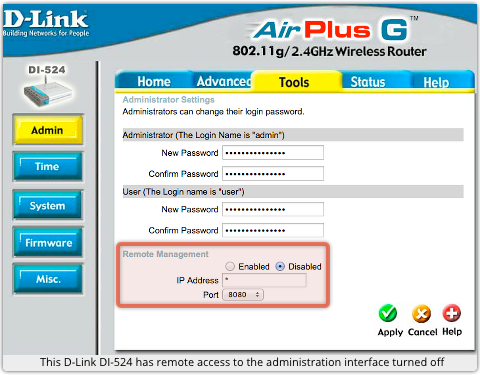
 Federal money earmarked to thwart terrorist attacks in the US is instead getting funneled into increasingly pervasive surveillance of citizens, the
Federal money earmarked to thwart terrorist attacks in the US is instead getting funneled into increasingly pervasive surveillance of citizens, the