SophosLabs has asked us to remind you about a destructive malware threat that calls itself CryptoLocker.
Sophos Anti-Virus detects it by the name Troj/Ransom-ACP, because that’s exactly what it does: holds your files to ransom.
Demanding money with menaces
Malware that encrypts your data and tries to sell it back to you, or else, is not new.
In fact, one of the earliest pieces of malware that was written specifically to make money, rather than simply to prove a point, was the AIDS Information Trojan of 1989.
 That Trojan scrambled your hard disk after 90 days, and instructed you to send $378 to an accommodation address in Panama.
That Trojan scrambled your hard disk after 90 days, and instructed you to send $378 to an accommodation address in Panama.
The perpetrator, one Dr Joseph Popp, was tracked down in the USA, extradited to the UK to stand trial, displayed increasingly shambolic behaviour, and was ultimately kicked out of Britain and never convicted.
Fortunately, his malware was similarly shambolic: it used simplistic encryption algorithms, and every computer was scrambled in the same way, so free tools for cleanup and recovery soon became available.
Sadly, the crooks behind the CryptoLocker malware haven’t made the same coding mistakes.
The malware seems to do its cryptography by the book, so there is no way to recover your scrambled files once it has triggered. (You could, I suppose, try paying the ransom, but I recommend that you do not.)
What CryptoLocker does
When the malware runs, it proceeds as follows:
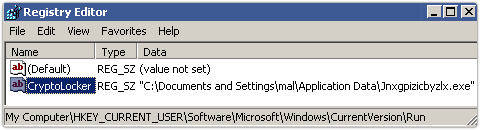
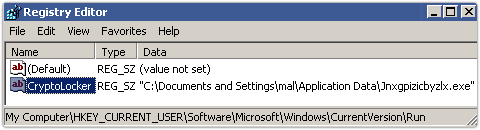
1. CryptoLocker installs itself into your Documents and Settings folder, using a randomly-generated name, and adds itself to the list of programs in your registry that Windows loads automatically every time you logon.
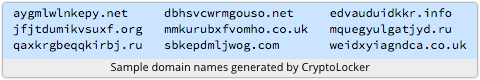
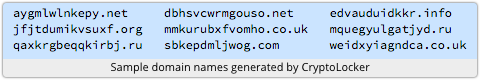
2. It produces a lengthy list of random-looking server names in the domains .biz, .co.uk, .com, .info, .net, .org and .ru.
3. It tries to make a web connection to each of these server names in turn, trying one each second until it finds one that responds.
4. Once it has found a server that it can reach, it uploads a small file that you can think of as your “CryptoLocker ID.”
5. The server then generates a public-private key pair unique to your ID, and sends the public key part back to your computer.
→ Remember that public-key cryptography uses two different keys: a public key that locks files, and a private key that unlocks them. You can share your public key widely so that anyone can encrypt files for you, but only you (or someone to whom you have given a copy of your private key) can decrypt them.
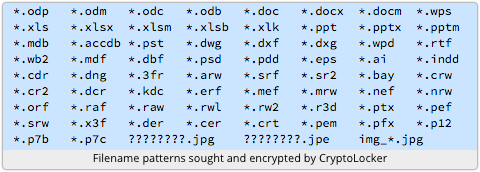
6. The malware on your computer uses this public key to encrypt all the files it can find that match a largish list of extensions, covering file types such as images, documents and spreadhseets.
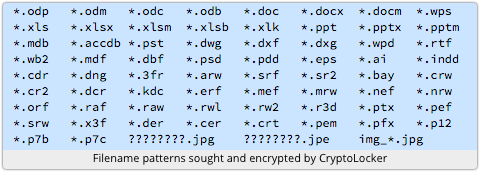
→ Note that the malware searches for files to encrypt on all drives and in all folders it can access from your computer, including workgroup files shared by your colleagues, resources on your company servers, and possibly more. The more privileged your account, the worse the overall damage will be.
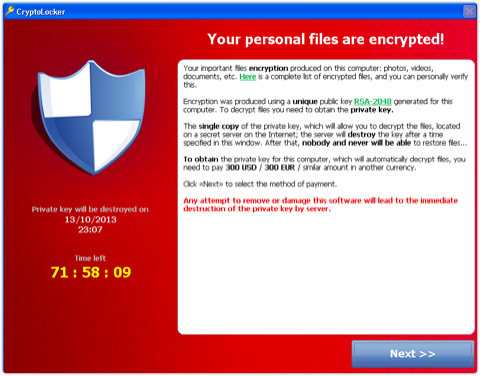
7. The malware then pops up a “pay page,” giving you a limited time, typically 100 hours, to buy back the private key for your data, typically for $300. (The price point is suprisingly similar to what it was back in 1989.)
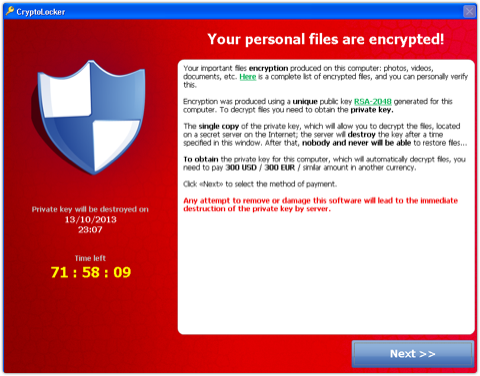
→ With the private key, you can recover your files. Allegedly. We haven’t tried buying anything back, not least because we know we’d be trading with crooks.
What we have seen
SophosLabs has received a large number of scrambled documents via the Sophos sample submission system.
These have come from people who are keenly hoping that there’s a flaw in the CryptoLocker encryption, and that we can help them get their files back.
But as far as we can see, there’s no backdoor or shortcut: what the public key has scrambled, only the private key can unscramble.
In the clumsy but categorical words of the criminals themselves:
The single copy of the private key, which will allow you to decrypt the files, located on a secret server on the Internet; the server will destroy the key after a time specified in this window. After that, nobody and never will be able to restore files.
And that’s why SophosLabs wanted us to write this article, since they’re faced with the sad job of telling the victims that their files are as good as deleted.
How the threat gets in
SophosLabs reports two main infection vectors: via email attachments and via botnets.
Email attacks are fairly easy to avoid: take care with attachments you weren’t expecting, or from people you don’t know well.
Infection via a botnet is a little different, since the crooks are using the fact that you are already infected with malware as a way to infect you with yet more malware.
That’s because most bots, or zombies, once active on your computer, include a general purpose “upgrade” command that allows the crooks to update, replace, or add to the malware already on your PC.
So take our advice: make it your task today to search out and destroy any malware already on your computer, lest it dig you in deeper still.
What you can do
Take this story as a warning, and don’t forget that there are many other ways you could lose your files forever.
For example, you could drop your laptop in the harbour (it happens!); a thief could run off with your computer (it happens!); or you could entrust your files to a cloud service that suddenly shuts down (it happens!).
The endgame is the same in all cases: if you have a reliable and recent backup, you’ll have a good chance of recovering without too much trouble.
Prevention, in this case, is significantly better than cure:
- Stay patched. Keep your operating system and software up to date.
- Make sure your anti-virus is active and up to date.
- Avoid opening attachments you weren’t expecting, or from people you don’t know well.
- Make regular backups, and store them somewhere safe, preferably offline.
Don’t forget that services that automatically synchronise your data changes with other servers, for example in the cloud, don’t count as backup.
They may be extremely useful, but they tend to propagate errors rather than to defend against them.
To the synchroniser, a document on your local drive that has just been scrambled by CryptoLocker is the most recent version, and that’s that.
Further information
For more information, including links to our support knowledgebase, our sample submission system, and how to find us on the IT social business network Spiceworks, please see this article on the Sophos corporate blog.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/62_gEqAbSR8/
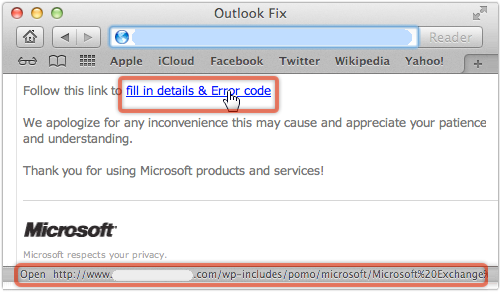
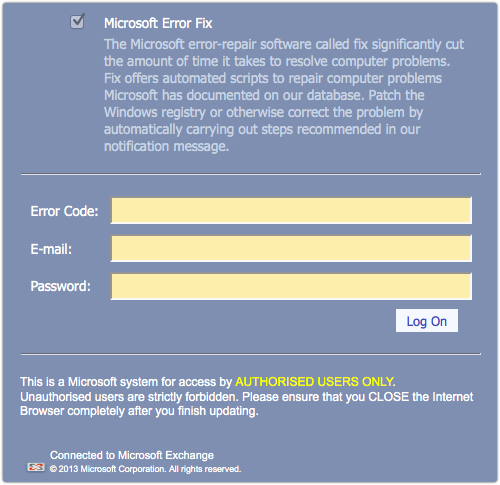
 We get an awful lot of spam in our spamtraps.
We get an awful lot of spam in our spamtraps.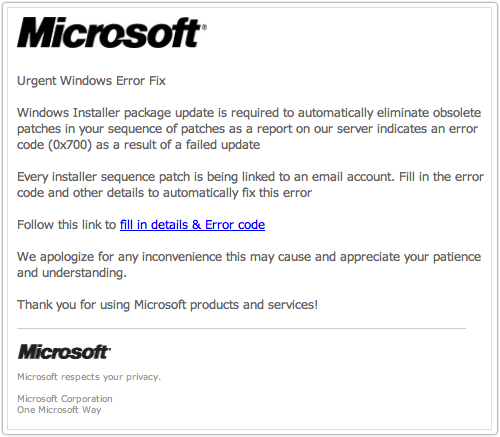
 In December 2012, Facebook announced a slew of privacy changes, one of which –
In December 2012, Facebook announced a slew of privacy changes, one of which – 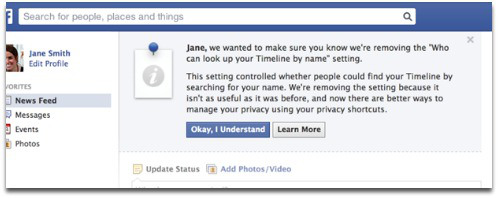
 Adobe’s source code – the code for flagship products behind an
Adobe’s source code – the code for flagship products behind an  At any rate, hopefully, given the lack of protection they put on the source code, the hackers who stole Adobe’s code won’t prove to be very adept at exploiting it.
At any rate, hopefully, given the lack of protection they put on the source code, the hackers who stole Adobe’s code won’t prove to be very adept at exploiting it.  That Trojan scrambled your hard disk after 90 days, and instructed you to send $378 to an accommodation address in Panama.
That Trojan scrambled your hard disk after 90 days, and instructed you to send $378 to an accommodation address in Panama.



 That Trojan scrambled your hard disk after 90 days, and instructed you to send $378 to an accommodation address in Panama.
That Trojan scrambled your hard disk after 90 days, and instructed you to send $378 to an accommodation address in Panama.