Venafi Launches New Threat Center
SALT LAKE CITY, UT – October 9, 2013 – Venafi, the market-leading cybersecurity company in Next-Generation Trust Protection (NGTP), today announced the release of Venafi Threat CenterTM. Recognizing the sharp rise in cyber-criminals who exploit the trust established by cryptographic keys and digital certificates, Venafi created Threat Center to focus specifically on the increase in trust-based attacks and their impact on Global 2000 enterprises. Another industry first, Venafi Threat Center offers insight into and intelligence about this new threat vector and provides strategies to mitigate these attacks.
On a global basis, every organization and government entity is under attack. Cyber-criminals are using keys and certificates as an attack vector to compromise enterprises and to disguise their activities within organizations. Recent Ponemon Institute research validates that every organization has fallen prey to attacks on keys and certificates in the last two years. Due to the lack of insight into key and certificate inventories, more than 60% of organizations take at least 24 hours to one week to replace compromised keys and certificates. This delay results in an average $398 million exposure for every organization over two years.
Access Venafi Threat Center, including new research regarding attacks on keys and certificates, here.
Secure Socket Layer (SSL) and Transport Layer Security (TLS) have fast become two of the most widely deployed and popular techniques that cyber-criminals use to mask their communications between remote access tools (RAT) and command and control (C2). Unfortunately, the millions of dollars organizations spend on perimeter-based security solutions are for naught; compromised keys and certificates provide cyber-criminals with unfettered trusted access and status. Forrester Research has recognized that “enterprise awareness of attacks on keys and certificates is in its infancy; most don’t understand how to detect or respond to an attack.” (July 2013 commissioned study entitled “Attacks on Trust: The Cybercriminal’s New Weapon,” conducted by Forrester Consulting on behalf of Venafi.)
“For too long organizations have blindly trusted keys and certificates that provide little visibility into their threat risk exposure,” said Jeff Hudson, Venafi CEO. “Malicious actors have taken note of this blind trust and use it nefariously against organizations and government entities. The results are clear: terabytes of valuable information and intellectual property are being pilfered from them for months before a compromise is even detected. Venafi Threat Center is at the forefront of Next-Generation Trust Protection (NGTP), helping organizations respond to and remediate trust-based attacks.”
Venafi Threat Center provides organizations with information about current threats related to compromised keys and certificates, an understanding of how encryption keys and certificates establish trust, and insight into recommended strategies to protect against attacks on trust. Venafi Threat Center also provides details about the Venafi Trust Protection Platform, which empowers organizations to detect trust-based attacks and rapidly respond to mitigate them.
Sample reports on the new Venafi Threat Center site include:
“Broken Trust: Exposing the Malicious Use of Digital Certificates Cryptographic Keys: – iSIGHT Partners and Venafi
“Attacks On Trust: The Cybercriminal’s New Weapon” – Commissioned Forrester Consulting Study
“2013 Annual Cost of Failed Trust Report: Threats Attacks” – Ponemon Institute
“Is Your APT Strategy Leaving the Door Open?” – Venafi
About Venafi
Venafi is the market leading cybersecurity company in Next-Generation Trust Protection (NGTP). As a Gartner-recognized Cool Vendor, Venafi delivered the first trust protection platform to secure cryptographic keys and digital certificates that every business and government depend on for secure communications, commerce, computing, and mobility. As part of an enterprise infrastructure protection strategy, Venafi Director prevents attacks on trust with automated discovery and intelligent policy enforcement, detects and reports on anomalous activity and increased threats, and remediates errors and attacks by automatically replacing keys and certificates. Venafi Threat Center provides research and threat intelligence regarding trust-based attacks. Venafi customers are among the world’s most demanding, security-conscious Global 2000 organizations in financial services, insurance, high tech, telecommunications, aerospace, healthcare and retail. Venafi is backed by top-tier venture capital funds, including Foundation Capital, Pelion Venture Partners and Origin Partners. For more information, visit www.venafi.com.
Article source: http://www.darkreading.com/vulnerability/venafi-launches-new-threat-center/240162444
 Microsoft’s Tenth Anniversary Patch Tuesday
Microsoft’s Tenth Anniversary Patch Tuesday 
 Adobe’s Patch Tuesday fixes
Adobe’s Patch Tuesday fixes 
 All communications coming from visitors and athletes at the 2014 Winter Olympics in Russia will be monitored by newly strengthened telephone and internet spying technologies.
All communications coming from visitors and athletes at the 2014 Winter Olympics in Russia will be monitored by newly strengthened telephone and internet spying technologies. The work has included laws that require all telephone and ISP providers to install SORM boxes in their technology.
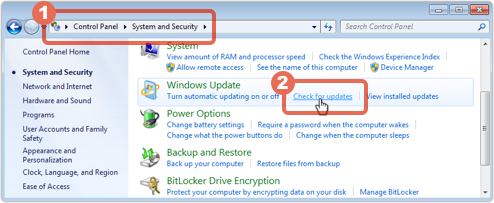
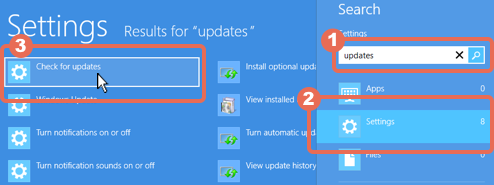
The work has included laws that require all telephone and ISP providers to install SORM boxes in their technology.  Microsoft marked yesterday’s tenth anniversary of
Microsoft marked yesterday’s tenth anniversary of  Otherwise, I guess it could always consider giving him some gift vouchers, though it may want to check how the security community reacted when
Otherwise, I guess it could always consider giving him some gift vouchers, though it may want to check how the security community reacted when