Adobe’s first update since the Big Breach
 Adobe’s Patch Tuesday fixes are out.
Adobe’s Patch Tuesday fixes are out.
This is business as usual, promised long in advance and expected toay, so there isn’t anything in it related to the company’s recent network intrusion woes. (We hope!)
There’s a RoboHelp update, discussed in APSB13-24, and fixes for Version XI of Acrobat and Reader, discussed in APSB13-25.
The RoboHelp bug allows potential RCE, or Remote Code Execution, so you definitely want the APSB13-24 patch if you’re a RoboHelp user.
The Reader XI and Acrobat XI vulnerability is a little different, and it’s just the sort of bug that Adobe could have done without right now, because it’s what is known as a regression.
If you’re on Reader X or Acrobat X, you’re not affected and can stand down from high alert. For now, anyway.
In programming, a regression is when you make new changes that inadvertently counteract various previous changes and, hey presto, a bug that you thought you’d got rid of returns.
If you like, a regression is a sort of anti-patch, where you repeat a mistake you fixed already.
Adobe isn’t giving a lot of detail away, but does say:
This update resolves a regression that permitted the launch of javacript scheme URIs when viewing a PDF in a browser (CVE-2013-5325).
The scheme in a URI is the part at the beginning, like http://, or mailto:, that tells your browser how to get to the resource you’ve just specified.
Until fairly recently, most browsers allowed you to go the address bar and run JavaScript directly, by prefixing it with the scheme identifier javascript:, for example like this:
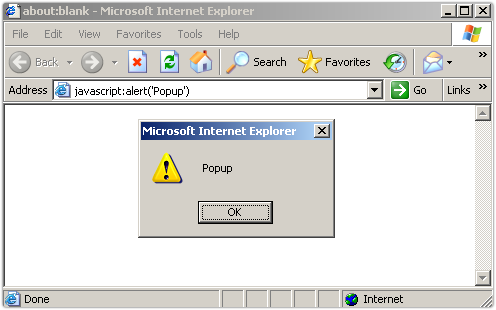
The hazards quickly became obvious once scammers starting luring you into “pasting the following web address into the address bar,” but including a JavaScript-based URL, not one that used HTTP.
→ There are hundreds of different legal URL schemes, from aaa: (a protocol to do with login, dealing with authentication, authorisation and accounting) to z39.50: (a search and indexing protocol that was made pointless by the web).
JavaScript-based URLs are now considered harmful in your browser’s address bar, and so browsers simply ignore them.
So will your Adobe PDF plugin, once you’ve updated.
Should you patch Reader and Acrobat?
And that raises an interesting question: should you apply this patch?
After all, some of you might be feeling a bit cagey about accepting Adobe’s patches right now.
The company just admitted that hackers were able to break in and exfiltrate 40GB of product source code from the corporate network, almost certainly including Acrobat.
What if the crooks were also able to make commits? (That’s where you save back changes so they can be compiled into the next build.)
If they did so, and their changes weren’t spotted, malicious modifications could now be part of an official release.
My own opinion is that this is highly unlikely, not least because modern software engineering tools make it comparatively easy to track the changes to the source code files in a product between builds.
Easy for me to say, of course – as an OS X user my PDF needs are met without having Reader or Acrobat installed, so a botched release wouldn’t affect me directly.
Nevertheless, remember that this patch deals with fixing a regression – “repatching” a previous patch – rather than with a shepherding in a huge raft of changes throughout the product.
So it’s reasonable to assume that if Adobe’s recent unauthorised visitors really had made any malware-related modifications, they’d surely have been spotted before release.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/Kai837pPfgQ/
 This month is
This month is  Many apps require more than the basic default permissions. For instance, you can reasonably expect an SMS app to send and receive text messages just as a mapping app will request your GPS location.
Many apps require more than the basic default permissions. For instance, you can reasonably expect an SMS app to send and receive text messages just as a mapping app will request your GPS location. One of the great things about modern mobile phones is their ability to connect to the internet in many ways, but continually probing for wireless networks gives away information about your identity and location, and blindly connecting to unencrypted access points can let your
One of the great things about modern mobile phones is their ability to connect to the internet in many ways, but continually probing for wireless networks gives away information about your identity and location, and blindly connecting to unencrypted access points can let your