Webroot Unveils New SecureAnywhere For Home Users
Broomfield, Colo., USA – October 7, 2013 – Webroot, a leader in cloud-based security intelligence solutions, today announced the release of the latest updates to their Webroot SecureAnywhere portfolio for individuals and families. Since their introduction, Webroot SecureAnywhere solutions have garnered critical acclaim for their superior protection and performance. According to a recent survey, the percentage of consumers who would recommend Webroot SecureAnywhere was nearly double that of the next closest competitor.
Webroot’s latest release brings customers even better protection with new detection technology to block emerging malware and phishing attacks more quickly, a completely redesigned interface for easy monitoring and control, and extended platform support to unify protection across PCs, Macs, and Androidtrade and Apple iOS devices. Other enhancements include web content filtering, an expanded management website, advanced user authentication, and integration of the Webroot Backup Sync with the Microsoft Windows Explorer environment.
WATCH THE VIDEO: See what’s new in the latest edition of SecureAnywheretrade with Webroot security expert Joe Jaroch.
Cloud-based Webroot SecureAnywhere threat detection offers connected consumers an alternative to the traditional security solutions that have proven ineffective against today’s malware, and caused significant performance slow-downs on the devices they were meant to protect. Webroot SecureAnywhere installs in seconds and scans most devices in less than two minutes, and its cloud-based threat detection architecture means there are no security updates or patches to download. All users are protected against the latest threats from the moment they are discovered – anywhere in the world.
“The volume of new malware and phishing attacks increased by over 50% last year, and the sophistication of these attacks is increasing as well,” said Mike Malloy, executive vice president of products and strategy at Webroot. “With the newest release of Webroot SecureAnywhere, we have integrated powerful, new protection features that address these emerging threats in real time. Our customer data shows that less than one-half of one percent of SecureAnywhere users have gotten infected since switching to our solution, the best protection in the security industry. Webroot’s cloud-based threat intelligence simply responds more quickly and more effectively than traditional security products to protect all of our users as soon as they are attacked by a new threat.”
Real-Time Defense against Phishing Attacks
Phishing attacks often spoof legitimate sites, and most phishing sites are only active for a few hours, disappearing after they’ve obtained the target’s banking credentials, passwords or other sensitive data. This makes such a major security risk incredibly difficult to track. The latest update to Webroot SecureAnywhere protection introduces real-time anti-phishing technology to quickly analyze a website when it is accessed by a user and automatically block it if it is a phishing site.
Webroot Infraredtrade Provides Advanced Detection of Zero-Day Malware
Webroot has introduced a powerful new threat detection engine called Infrared. Utilizing data from the Webroot Intelligence Networktrade (WIN) cloud security service, Webroot Infrared analyzes unknown files by correlating their behavior, and origin and makes an assessment of the associated risk before the file is allowed to run. The Webroot Infrared engine also customizes protection to the individual device based on a combined analysis of the operating system, applications, and prior threats which have been observed.
Enhanced Protection for Multi-device Users
Webroot research has shown an increase in households with a mix of PCs, Macs, and Android and iOS tablets and smartphones, and all of the updated Webroot SecureAnywhere solutions include multi-platform protection with a single license. In addition, Mac users now have more advanced protection with the addition of System Analyzer and Backup Sync. Further, these multi-platform households now have a consistent user interface for their Windows and Mac security, and can manage both platforms from within the online Webroot SecureAnywhere management environment.
Key features of Webroot SecureAnywhere consumer protection:
Set it and forget it – continuous protection without interruptions or slowdowns
Real-time anti-phishing identifies and blocks fake websites that trick you into entering your personal information
Warns you about infected websites before you visit them
Protects and simplifies managing passwords – you remember just one
Automatically backs up photos and files with up to 25GB of online storage you can access from all your devices
Social network protection including Facebook and Twitter
Advanced protection for tablets and smartphones
Analyzes devices and operating systems to detect system issues
Wipes away all traces of online activity and makes deleted files unrecoverable
Automatically scans Androidtrade apps and downloads for mobile threats
Remotely locks or wipes data from smartphones and tablets and helps locate lost or stolen devices
Lets you manage security on all your devices from anywhere through one simple interface
Purchasing and Availability
Webroot SecureAnywhere Consumer Portfolio: Ranging from Webroot SecureAnywhere AntiVirus, Webroot SecureAnywhere Internet Security Plus, Webroot SecureAnywhere Complete, iOS SecureWeb, and Android Mobile, the new services from Webroot are designed to fit your specific needs. The Webroot SecureAnywhere consumer product family is available now online at http://www.webroot.com and at select retailers. Existing customers will receive this new product version for free. For additional product information, visit http://www.webroot.com/us/en/home/.
About Webroot
Webroot is bringing the power of software-as-a-service (SaaS) to Internet security worldwide with its suite of Webroot SecureAnywhere solutions for consumers and businesses, and security intelligence solutions for enterprises and technology partners focused on cyber-security. For more information, visit http://www.webroot.com or call 800.772.9383. Read the Webroot Threat Blog: http://blog.webroot.com. Follow Webroot on Twitter: http://twitter.com/webroot.
Article source: http://www.darkreading.com/end-user/webroot-unveils-new-secureanywhere-for-h/240162304
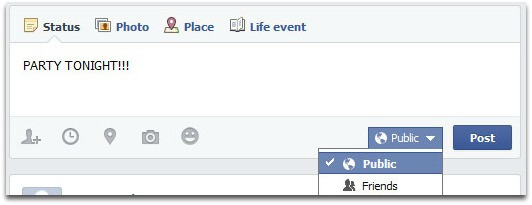
 As it is, the public posting of a party on Facebook has left the Seales with a home that’s still a bit sticky, with the smell of vomit lingering days after the bacchanalia.
As it is, the public posting of a party on Facebook has left the Seales with a home that’s still a bit sticky, with the smell of vomit lingering days after the bacchanalia. Just a couple of weeks ago
Just a couple of weeks ago  It’s Get Ready For Microsoft Patch Tuesday time again already, and
It’s Get Ready For Microsoft Patch Tuesday time again already, and