Cheeky Lavabit *did* hand over crypto keys to US government after all – printed in a 4
 Just under two months ago, we wrote about the closure of secure email service Lavabit.
Just under two months ago, we wrote about the closure of secure email service Lavabit.
Lavabit’s founder, Ladar Levison, explained that he was in a spot of legal bother that made it impossible for him to continue to operate with a clear conscience, so he would suspend the service.
He also noted that, much as he wanted to, he couldn’t give details about said legal bother.
All he could do was to point out that he had lodged an appeal and hoped to open up the service again one day.
Of course, the smart money was that law enforcement wanted access to data belonging to a certain Mr Edward Snowden, the National Security Agency (NSA) whisteblower, who was known to be a Lavabit user.
 We hedged our bets about the reasons here on Naked Security, since the only thing we knew was that we didn’t know whether the kerfuffle involved Snowden at all.
We hedged our bets about the reasons here on Naked Security, since the only thing we knew was that we didn’t know whether the kerfuffle involved Snowden at all.
But recently unsealed court documents [PDF, 162 pages, 16MB] now tell a bit more of the story.
The name Snowden is still mentioned only in passing (various redactions have suppressed names throughout the unsealed documents).
So we still don’t have official confirmation that Snowden, amongst others, was the target of the investigation.

That, however, hardly matters any more.
What matters is the intriguing tale of the court requiring Lavabit to hand over its SSL private keys, and Lavabit arguing that it ought not to comply, since that would give access to all messages to and from all customers, which would be unfair and unreasonable.
Very greatly simplified (and I hope I have not oversimplified to the point of misunderstanding), the court wanted Lavabit to enable law enforcement to intercept so-called email metadata for a particular user.
But due to the use of SSL/TLS at all times, with data kept encrypted in transit and at rest, even accessing mail headers was no simple matter – unless law enforcement were given Lavabit’s private keys.
(A MiTM, or man-in-the-middle, attack on encrypted traffic is trivial if you have all the encryption keys and certificates to use “in the middle.”)
Eventually, Lavabit had little choice but to comply, turning over five SSL private keys.
It still wasn’t game over for Lavabit user’s privacy, however, because Levison gamely supplied the cryptgraphic material in printed form, stretched over 11 pages in a four-point font.

To say that the law enforcement officers were underwhelmed is the understatement of the year, and matters were soon back in court, with “handing over the keys” quickly redefined to mean, “handing over the keys as computer-readable PEM files suitable for immediate use, and no more mucking around.”
Indeed, to guard against further stalling tactics, the government petitioned the court to fine Levison $5000 for every day he continued to dither.
At this point, Levison folded and complied, but pulled the plug on Lavabit at the same time, and that was that for the men-in-the-middle.
The New York Times reports that a prosecutor referred to the abrupt shutdown of Lavabit as “just short of a criminal act,” but, then, nearly-a-crime isn’t actually a crime.
What can we learn from this?
To me, one of the most interesting aspects of this story is the recognition by a non-tech-savvy court that at least part of the problem was the regrettable fact that Lavabit would need to put the privacy of 400,000 users at risk to secure the lawful surveillance of just one person.
As the court pointed out (this is a transcript, not a written judgement):
[Y]ou’re blaming the government for something that’s overbroad [the requirement to hand over the all-revealing SSL keys], but it seems to me that your client is the one that set up the system that’s designed not to protect that information, because you know that there needs to be access to calls that go back and forth to one person or another. And to say you can’t do that just because you’ve set up a system that everybody has to — has to be unencrypted, [read: in which all users are encrypted in the same way] if there’s such a word, that doesn’t seem to me to be a very persuasive argument.
In short, the court is as good as saying, “If you wanted to come up with this ‘but what about the privacy of all the 399,999 other users’ argument, why didn’t you implement the system so their individual privacy was better protected?”
 After all, Lavabit could have taken an approach more like the one used by Kiwi internet showman Kim Dotcom’s Mega service, so that each user’s encrypted traffic and content could stand (or fall) alone.
After all, Lavabit could have taken an approach more like the one used by Kiwi internet showman Kim Dotcom’s Mega service, so that each user’s encrypted traffic and content could stand (or fall) alone.
Of course, that wouldn’t have stopped Levison shuttering the entire service, effectively DDoSing all his users to protect the privacy of one of them.
But from a cryptographic point of view, it would have made a lot more sense to me.
Image of eye charts courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/5-2aAH5bvT0/
 After seizing the domain and servers of Silk Road – a black market, eBay-like online bazaar for heroin, ecstasy, other illegal drugs and every known type of prescription drugs – federal prosecutors on Wednesday released two separate set of charges against its alleged kingpin.
After seizing the domain and servers of Silk Road – a black market, eBay-like online bazaar for heroin, ecstasy, other illegal drugs and every known type of prescription drugs – federal prosecutors on Wednesday released two separate set of charges against its alleged kingpin.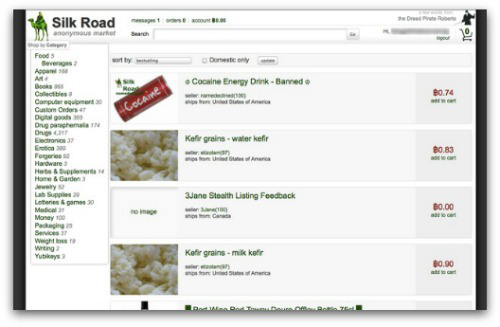 When Forbes’s Andy Greenberg in August
When Forbes’s Andy Greenberg in August 
 The
The  The popular Bitcoin discussion forum, Bitcointalk.org, was hacked and defaced on Wednesday. The site continues to be unavailable following a decision by administrators to take it down to investigate the full extent of the hack.
The popular Bitcoin discussion forum, Bitcointalk.org, was hacked and defaced on Wednesday. The site continues to be unavailable following a decision by administrators to take it down to investigate the full extent of the hack.