Online vicemart Silk Road shut by Feds
5 ways to prepare your advertising infrastructure for disaster
The notorious online drug market Silk Road has been shut down by the FBI, its suspected operator arrested and charged with narcotics trafficking conspiracy, computer hacking conspiracy, and money laundering conspiracy, and $3.6m worth of the bitcoin crypto-currency has been confiscated by federal agents.
The site’s alleged founder and main operator Ross William Ulbricht, aka “Dread Pirate Roberts” (DPR) was arrested in a public library in San Francisco on Tuesday. Silk Road’s Tor-based drug bazaar was shut down on Wednesday and users visiting the site were met with an FBI takedown notice.
Ulbricht made a number of operational security mistakes that linked his identity with various online personas associated with Silk Road, according to the FBI court complaint. However, there is no detail in the filing about how the FBI gained access to a Silk Road Tor server on which the site was based – an omission sure to disturb members of the security community at a time when new information is coming to light about the advanced capabilities of the American spy organization, the NSA.
“Silk Road has emerged as the most sophisticated and extensive criminal marketplace on the Internet today,” FBI agent Christopher Tarbell wrote in the FBI’s criminal complaint. “From in or about January 2011, up to and including in or about September 2013, ROSS WILLIAM ULBRICHT, a/k/a “Dread Pirate Roberts,” a/k/a “DPR,” a/k/a “Silk Road,” the defendant, owned and operated an underground website known as “Silk Road,” that provided a platform for drug dealers around the world to sell a wide variety of controlled substances via the Internet.”
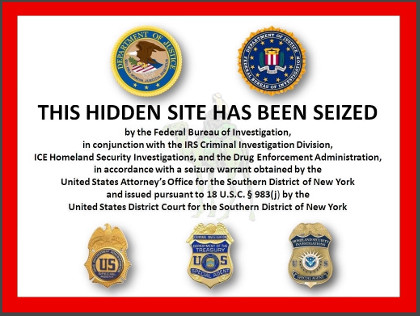
Silk Road shut for business’
Silk Road ran on Tor, a hidden computer network, and only accepted payments in the pseudo-anonymous BitCoin cryptocurrency. The FBI gained access to a Tor server on which the site was hosted and made a snapshot on July 2013.
The price of BitCoins crashed on Wednesday morning after news of the shutdown broke, adding grist to the Benjamin Lawsky, superintendent of the New York Department of Financial Services, characterization of the currency as “a virtual Wild West for narcotraffickers and other criminals“.
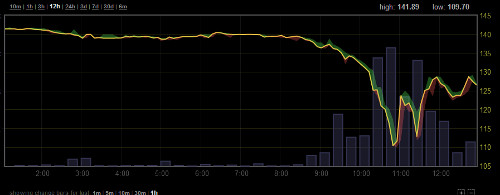
The Bitcoin exchange rate slumped after the site was taken down
The FBI says in its statement the it had “located in a certain foreign country the server used to host the silk road’s website,” and had gained access to it via a “mutual legal assistance request”.
This calls into question many of the widely-held beliefs about the security and anonymity of the Tor service.
There is also evidence that Ulbrich may have implicated himself and through lax security policies betrayed the details of the Tor servers.
One slip up was a posting on programmer QA site Stack Overflow under the name Ross Ulbricht that asked “How can I connect to a Tor hidden service using curl in php?”, before changing the account name to “Frosty”. A subpoena by the FBI showed the original account name.
Another screw up came with postings on two forums under the user name “Altoids” in early 2011 advertising the Silk Road, before posting several months later under the “Altoids” username on a Bitcoin forum asking for “IT pro in the bitcoin community” to help out on a “venture-backed company,” then advising them to contact the email address rossulbricht at gmail dot com.
The FBI also obtained data from Google on this Gmail account which closely associated access with separate logins to the Silk Road from similar locations in San Francisco.
Ulbricht had also arranged to have some nine fake identities sent to him for the purpose of procuring new servers. These documents were intercepted by customers and border patrol officials in early July, 2013, and led them to pay a visit to Ulbricht in San Francisco on July 26.
Ulbricht’s alleged online alias of ‘Dread Pirate Roberts’ had made numerous postings on Silk Road seeking identity documents from users. This is a rookie mistake that breaks dead rapper the Notorious B.I.G’s advice to dealers and lowlifes – “don’t get high off your own supply”.
A further point of compromise was that Ulbrich’s real life Google+ profile had shared videos from obscure economics thinktank the Ludwig von Mises Institute – the same videos were linked to by the signature of the Dread Pirate Roberts account on the Silk Road.
According to the complaint, Ulbricht employed several administrators on the Silk Road paying them $1,000 to $2,000 a week. They called him “boss” and “captain” the FBI said.
Bitcoin murder contract
The indictment states Silk Roads made scads and scads of cash, generating some $1.2bn in bitcoin transactions of which $80m was siphoned off by Dread Pirate Roberts during the course of its life. But it was not without problems the FBI claims.
The complaint accuses Ulbricht’s alleged online alias Dread Pirate Roberts of paying a third-party to murder another user of the site, who was trying to extort him.
The Dread Pirate Roberts was contacted in March 2013 by a Silk Road user “FriendlyChemist” claiming to have the details of thousands of the buyers and sellers on the anonymous illegal drug and services marketplace.
“FriendlyChemist” attempted to extort some $500,000 from him in exchange for the information, and eventually stated he needed the money because they owed money to a group of suppliers that used the Silk Road handle “redandwhite”.
Dread Pirate Roberts allegedly got in touch with redandwhite and, when FriendlyChemist continued attempting to extort him, asked if they could have the user killed. Dread Pirate Roberts then supplied them information on FriendlyChemist, including the person’s whereabouts (British Columbia, Canada), the FBI state.
“I would like to put a bounty on his head if it’s not too much trouble for you. What would be an adequate amount to motivate you to find him? Necessities like this do happen from time to time for a person in my position,” Dread Pirate Roberts wrote to redandwhite, who suggested a cost of between $150,000 and $300,000. They settled on a price of $150,000, which was transferred in bitcoins.
Though redandwhite claimed to have offed the person in question, and at the request of Dread Pirate Roberts sent a photo of the body, the FBI says the Canadian Police are not aware of any homicide associated with this case. Nor do they have information on anyone with the details of the aforementioned “FriendlyChemist”.
The shutdown of Silk Road follows the vanishing of Tor-hosted file sharing service Freedom Hosting in early August, and the similarly unexpected and unexplained shutdown of rival Tor-hosted drug mart in September.
“Regrettably it has come time for Atlantis to close its doors. Due to security reasons outside of our control we have no choice but to cease operation of the Atlantis Market marketplace. Believe us when we say we wouldn’t be doing this if it weren’t 100% necessary. Due to the urgency we are allowing all users to withdrawal all their coins for one week before the site, and forum, are shut down permanently,” Atlantis wrote at the time. Perhaps they knew something the Dread Pirate Roberts didn’t? ®
5 ways to reduce advertising network latency
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/10/02/silk_road_shutdown/
 Nervous reader, were you unsettled by the recent news that Yahoo’s email address recycling scheme had resulted in new account holders
Nervous reader, were you unsettled by the recent news that Yahoo’s email address recycling scheme had resulted in new account holders  Rather, the funds were dispersed as a discount code to spend in the
Rather, the funds were dispersed as a discount code to spend in the  It’s been nearly 10 months, but finally, the wait is over: We can now run Facebook searches to find
It’s been nearly 10 months, but finally, the wait is over: We can now run Facebook searches to find  That was apparent when the social network
That was apparent when the social network  It’s good to remember that Facebook doesn’t drag information out of people. Besides photos we’re tagged in without our permission, most everything that’s in our Graphs is up because we put it there.
It’s good to remember that Facebook doesn’t drag information out of people. Besides photos we’re tagged in without our permission, most everything that’s in our Graphs is up because we put it there.