 A “small but very potent” botnet run by an identity theft service has tentacles reaching into computers at some of the country’s largest consumer and business data aggregators, security journalist Brian Krebs has revealed following a seven-month investigation.
A “small but very potent” botnet run by an identity theft service has tentacles reaching into computers at some of the country’s largest consumer and business data aggregators, security journalist Brian Krebs has revealed following a seven-month investigation.
The service, which sells the Social Security numbers, birth records, credit and background reports of millions of US residents, has for the past two years run at ssndob[dot]ms (Krebs calls it simply SSNDOB, and I’ll follow suit).
SSNDOB markets itself on underground cybercrime forums as “a reliable and affordable service that customers can use to look up SSNs, birthdays and other personal data on any U.S. resident”, Krebs writes, charging from 50 cents to $2.50 per record and from $5 to $15 for credit and background checks.
The transactions are carried out mostly via largely unregulated and anonymous virtual currencies, including Bitcoin and WebMoney.
The source of SSNDOB’s data remained a mystery until earlier this summer, when the service was attacked and its database raided.
The alleged attackers – teenage hackers apparently associated with the hacktivist group UGNazi – pilfered personal information for celebrities including Beyonce, Kanye West, Jay-Z, First Lady Michelle Obama, CIA Director John Brennan, and then-FBI Director Robert Mueller.
They then exposed the data on exposed.su.
Exposed.su – which has apparently been taken down – is a Soviet Union domain that lists SSNs, birthdays, phone numbers, and current and previous addresses for dozens of top celebrities, Krebs says.
KrebsOnSecurity.com obtained and reviewed the database that the hackers stole from SSNDOB.
Analysis of the networks, network activity and credentials used by SSNDOB administrators eventually revealed that they were running a botnet – i.e., a network of hacked computers that they could remotely control to carry out their dirty work.
Two of the hacked servers belonged to LexisNexis, which maintains a massive database of legal and public records-related information.
LexisNexis confirmed to Krebs that the two systems listed in an interface for the botnet – both public-facing LexisNexis servers – had been compromised, while the botnet’s dashboard indicates that the infection was planted as far back as 10 April 2013.
Two more compromised servers were located inside the networks of Dun Bradstreet, a data aggregator that licenses information on businesses and corporations for use in credit decisions, business-to-business marketing and supply chain management, Krebs writes.
The botnet administration panel shows the Dun Bradstreet machines as having been infected at least as far back as 27 March 2013.
A fifth server on the botnet was located at internet addresses assigned to Kroll Background America, a company that provides employment background, drug and health screening, Krebs reports.
The company has since been taken over by HireRight, a background-checking firm managed by Altegrity, a holding company that owns both the Kroll and HireRight properties.
The Kroll/HireRight machine’s takeover extends back to at least June 2013.
LexisNexis confirmed to Krebs that its servers did in fact appear to have been compromised starting in April but that the company didn’t find any evidence that “customer or consumer data were reached or retrieved” from the breached systems. It’s still investigating the breach.
For its part, Dun Bradstreet said that it’s investigating, but it gave no further details. Altegrity declined to confirm or deny the apparent breaches.
The FBI confirmed to Krebs that it’s “aware of and investigating this case” but declined to comment further except to say that the investigation is ongoing.
Beyond PII
Beyond the potential loss of personally identifiable information (PII) that can be used to perpetrate identity theft, something far more valuable is at stake, fraud experts told Krebs.
 Namely, the breached firms have control of massive amounts of data about consumers’ and businesses’ habits and practices – a collection of data known in the industry as knowledge-based authentication (KBA) that’s used to determine how likely it is that a given credit application is valid or fraudulent, mostly based on how accurately an applicant answers a set of questions about their financial and consumer history, Krebs writes.
Namely, the breached firms have control of massive amounts of data about consumers’ and businesses’ habits and practices – a collection of data known in the industry as knowledge-based authentication (KBA) that’s used to determine how likely it is that a given credit application is valid or fraudulent, mostly based on how accurately an applicant answers a set of questions about their financial and consumer history, Krebs writes.
Avivah Litan, a fraud analyst with Gartner, told Krebs that KBA has become “the gold standard of authentication” among nearly all credit-granting institutions:
Let’s say you’re trying to move money via online bank transfer, or apply for a new line of credit… There are about 100 questions and answers that companies like LexisNexis store on all of us, such as, “What was your previous address?” or “Which company services your mortgage?”
They also have a bunch of bogus questions that they can serve up to see if you really are who you say you are.
Litan says that Dun Bradstreet does more or less the same thing for businesses.
Paradoxically, problematically, the people who fail to answer some of the questions likely don’t remember the answers, Litan said, whereas the criminals are the ones breezing through, since they have the data right at hand.
She told Krebs this story, heard from a fellow fraud analyst who had the chance to eavesdrop when a mortgage lender was asking KBA questions of a credit applicant who was later determined to have been a crook:
The woman on the phone was asking the applicant, “Hey, what is the amount of your last mortgage payment?”, and you could hear the guy on the other line saying hold on a minute… and you could hear him clicking through page after page for the right questions.
In fact, Litan told Krebs, the death knell is likely tolling for KBA.
That’s probably a good thing, given that she and others have been saying for years that the major KBA providers have been compromised.
The problem, she says, is that we just don’t have any good alternatives that are easy to implement. We lack a sufficient software alternative.
 Nor are there biometric identifiers ready to be rolled out for use by the entire US population at this point, and perhaps there never will be.
Nor are there biometric identifiers ready to be rolled out for use by the entire US population at this point, and perhaps there never will be.
As always, Krebs’ report is thorough and fascinating, so please do give it a read. He offers tons more detail on the investigation, including, for example, the finding that the identity theft service has served more than 1.02 million unique Social Security numbers to customers and nearly 3.1 million date of birth records since its inception in early 2012.
What he doesn’t offer, of course, is an alternative to the KBA on which these data brokers rely.
That’s a problem that needs time and serious work to figure out, Litan has written.
In the meantime, she says, service providers must be made aware that they can’t count on “the veracity and reliability of the process to indeed authenticate the ‘right’ and legitimate individual.”
One stark example of this that received much media attention was that of Mat Honan, the journalist whose Twitter account went berserk and whose devices were wiped after a fraudster called up Apple support and tricked them into handing over control to his iCloud account in August 2012.
How do you defend against such knowledge-dependent attacks?
It’s hard, as Paul Ducklin notes in his writing about Honan.
KBA attacks seem to be harder still, given the wealth of information to be stolen from data brokers.
Entrepreneurs, there’s a big, fat, potentially very profitable business opportunity waiting for you.
Oh, and while Cybersecurity Awareness Month in the US doesn’t start until next week, there’s no reason to delay getting rid of potential zombies (bot infections) on your own computer.
Remember that while this botnet is particularly valuable to the crooks because the infected computers are inside networks with juicy content, any zombified computer is a usable and useful tool for cybercriminals.
Be part of the solution, not part of the problem!
Sophos Anti-Virus on all platforms detects and blocks the various components of this malware as Troj/Delf-FPW.
Image of Social Security theft, credit history and fingerprint security courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/iuIggGLcNWM/
 A “small but very potent”
A “small but very potent”  Namely, the breached firms have control of massive amounts of data about consumers’ and businesses’ habits and practices – a collection of data known in the industry as knowledge-based authentication (KBA) that’s used to determine how likely it is that a given credit application is valid or fraudulent, mostly based on how accurately an applicant answers a set of questions about their financial and consumer history, Krebs writes.
Namely, the breached firms have control of massive amounts of data about consumers’ and businesses’ habits and practices – a collection of data known in the industry as knowledge-based authentication (KBA) that’s used to determine how likely it is that a given credit application is valid or fraudulent, mostly based on how accurately an applicant answers a set of questions about their financial and consumer history, Krebs writes. Nor are there biometric identifiers ready to be rolled out for use by the entire US population at this point, and perhaps there never will be.
Nor are there biometric identifiers ready to be rolled out for use by the entire US population at this point, and perhaps there never will be. 

 On Monday night, a very hush-hush Facebook tiptoed into testing an “Autofill with Facebook” feature – autofill your credit card information, that is – that it will begin rolling out to some users this week, according to
On Monday night, a very hush-hush Facebook tiptoed into testing an “Autofill with Facebook” feature – autofill your credit card information, that is – that it will begin rolling out to some users this week, according to  We really didn’t want to write another Apple iOS 7 story.
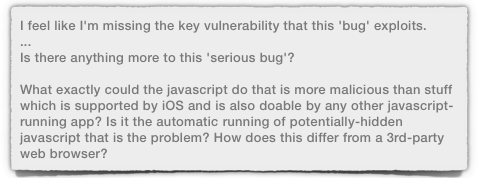
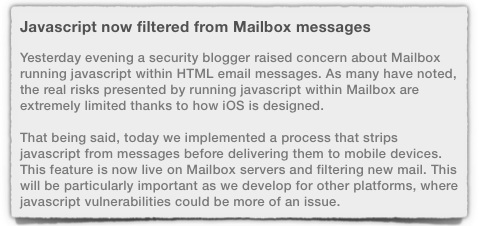
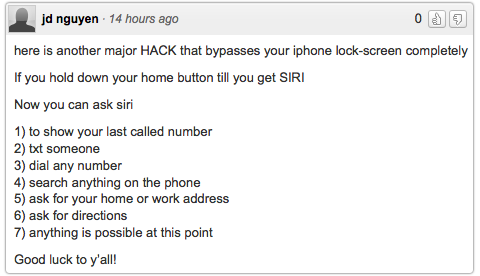
We really didn’t want to write another Apple iOS 7 story. But we didn’t want to enter a public wrangle with a concept we agree with strongly in principle.
But we didn’t want to enter a public wrangle with a concept we agree with strongly in principle.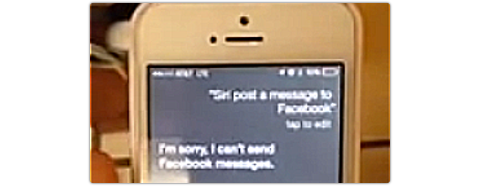
 It is time to start thinking of our hearts as random number generators. That’s so they can serve as passwords to secure medical devices that are vulnerable to hacking, researchers at Rice University have proposed.
It is time to start thinking of our hearts as random number generators. That’s so they can serve as passwords to secure medical devices that are vulnerable to hacking, researchers at Rice University have proposed.  Yahoo announced in June 2013 that it was going to recycle inactive email addresses by giving them to other users who wanted them.
Yahoo announced in June 2013 that it was going to recycle inactive email addresses by giving them to other users who wanted them. A “small but very potent”
A “small but very potent”  Namely, the breached firms have control of massive amounts of data about consumers’ and businesses’ habits and practices – a collection of data known in the industry as knowledge-based authentication (KBA) that’s used to determine how likely it is that a given credit application is valid or fraudulent, mostly based on how accurately an applicant answers a set of questions about their financial and consumer history, Krebs writes.
Namely, the breached firms have control of massive amounts of data about consumers’ and businesses’ habits and practices – a collection of data known in the industry as knowledge-based authentication (KBA) that’s used to determine how likely it is that a given credit application is valid or fraudulent, mostly based on how accurately an applicant answers a set of questions about their financial and consumer history, Krebs writes. Nor are there biometric identifiers ready to be rolled out for use by the entire US population at this point, and perhaps there never will be.
Nor are there biometric identifiers ready to be rolled out for use by the entire US population at this point, and perhaps there never will be.