Angry Brazilian whacks NASA to put a stop to … er, the NSA
Supercharge your infrastructure
Multiple NASA websites were defaced last week by a Brazilian hacktivist who may have misread the sites’ URLs, because he wasn’t protesting about the US space agency giving joyrides to inhuman stowaways – he was protesting against NSA spying.
“BMPoC” hit kepler.arc.nasa.gov and 13 other sites with messages protesting against US spying on Brazil, as well as a possible US military intervention in Syria.
It’s hard to believe anyone would confuse the NSA spy agency with NASA, the space agency, except for satirical purposes or to mock script kiddies in some way, so we can only guess that the hackers behind the attack hit NASA because it’s a US government agency whose systems are noted for being insecure.
NASA is at one level a scientific research agency with numerous links to universities. The notoriously weak security practices in much of academia have spilled over to the space agency. NASA’s less than stellar information security practices have been repeatedly criticised by government auditors.
The defacement messages themselves are all over the place, grammatically, and less than coherent logically.
NASA HACKED! BY #BMPoCWe! Stop spy on us! The Brazilian population do not support your attitude! The Illuminati are now visibly acting!
Obama heartless! Inhumane! you have no family? the point in the entire global population is supporting you. NOBODY! We do not want war, we want peace!!! Do not attack the Syrians.
A list of the defaced domains along with links to entries on defacement archive Zone-h can be found on Pastebin.
The hacked domains are maintained by various scientific missions within NASA such as the Kepler Mission, Ames Academy for Space Exploration and NASA’s Office of Planetary Protection, Virtual Astrobiology, a NASA recruitment domain, NASA Lunar Science Institute among others, CyberWarZone reports. Brief checks suggest most of the domains were returned to service by Monday morning.
A NASA spokesman played down the significance of the digital graffiti attacks, telling Fox News that everything was under control.
“A Brazilian hacker group posted a political message on a number of NASA websites. … Within hours of the initial posting, information technology staff at the Ames Research Center discovered the message and immediately started an investigation, which is ongoing,” he said. “At no point were any of the agency’s primary websites, missions or classified systems compromised.”
The same hacker/hacking group also hit NASA back in April, HackRead reports. Last time around the defacement had no politically-related content.
“NASA might be picked on simply because it represents low-hanging fruit,” writes Lisa Vaas, in a commentary on the hacking on Sophos’ Naked security blog. “Somebody ought to tell BMPoC that he/she/they are bullies kicking sand in the face of rocket scientists who have better things to do than mop up after an attack that’s spurred by a head-scratcher of a so-called rationale that’s unrelated to NASA’s mission.” ®
Supercharge your infrastructure
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/09/17/defacers_hit_nasa_in_nsa_protest/
 You’ll soon be enjoying the adulation of the whole jailbreaking scene, a writeup on Naked Security, and the prospect of a job/lawsuit (or both!) with/against Apple.
You’ll soon be enjoying the adulation of the whole jailbreaking scene, a writeup on Naked Security, and the prospect of a job/lawsuit (or both!) with/against Apple.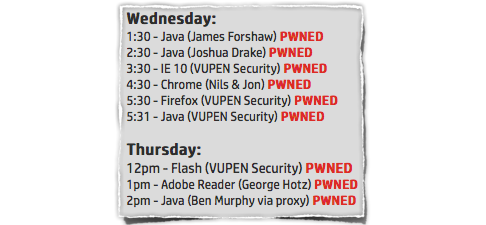
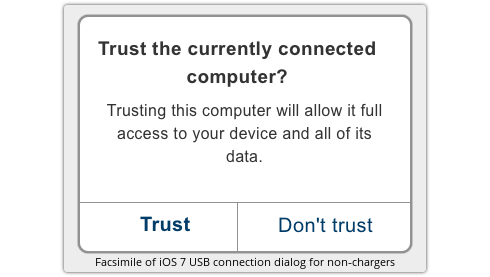
 Crooks can now purchase a low-cost, booby-trapped bank card reader bundled with a suite of money-stealing support services that make fraud crimes even easier.
Crooks can now purchase a low-cost, booby-trapped bank card reader bundled with a suite of money-stealing support services that make fraud crimes even easier. Oracle Java, easily the most attacked and successfully exploited browser plugin, is on my radar again after finding new ways to fail at security.
Oracle Java, easily the most attacked and successfully exploited browser plugin, is on my radar again after finding new ways to fail at security.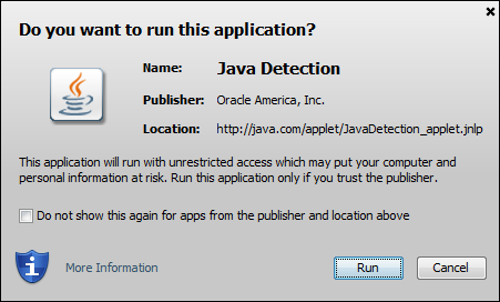
 Because they intend on discontinuing one of the most popular versions of Java (1.6) in April 2014 (a
Because they intend on discontinuing one of the most popular versions of Java (1.6) in April 2014 (a  Argentinian police have arrested a teenager, dubbed “the superhacker”, who was allegedly bleeding $50,000 (£31,500) per month out of international money transfer and gambling websites.
Argentinian police have arrested a teenager, dubbed “the superhacker”, who was allegedly bleeding $50,000 (£31,500) per month out of international money transfer and gambling websites.