Cloud Security Corporation Secures $2 Million Financing From Kodiak Capital Group, LLC
NEWPORT BEACH, Calif., Sept. 13, 2013 /PRNewswire/ — Cloud Security Corporation, (OTCBB: CLDS) a leading technology company focused on the next generation of Internet Security, announced that it has entered into a $2 million common stock purchase agreement with Kodiak Capital Group, LLC, a Newport Beach based institutional investor. The Company has agreed to file a registration statement with the U.S. Securities Exchange Commission (“SEC”) covering the shares that may be issued to Kodiak under the terms of the common stock purchase agreement. After the SEC has declared the registration statement related to the transaction effective, the Company has the right at its sole discretion over a period of one year to sell up to $2 million of its common stock to Kodiak under the terms set forth in the agreement. Proceeds from this transaction will be used to fund the company’s expansion and for general corporate purposes.
“We’re very thankful to Kodiak for this recognition,” commented Safa Movassaghi, Chief Executive Officer, of Cloud Security. “Kodiak shares our opinion that Cloud Security Corporation is well positioned in the rapidly developing internet security sector. With this capital infusion we will continue to develop and deploy innovative technology that improves cybersecurity.”
Under the terms of the agreement, there are no upper limits to the price that Kodiak may pay to purchase the Company’s common stock and this transaction in no way impedes or changes the Company’s goals. The Kodiak financing commitment simply strengthens the Company’s balance sheet and makes available an additional source of funding. Under the terms of the agreement, Kodiak has covenanted not to cause or engage in any manner whatsoever, any direct or indirect short selling or hedging of the Company’s shares of common stock.
Ryan Hodson, Managing Director of Kodiak, said, “After a successful week at Techcrunch and the Deutsche Bank Technology Conference we are pleased to formalize our partnership with Cloud Security Corporation; we are happy to add them to our growing disruptive technologies portfolio.”
About Kodiak Capital Group, LLC
Kodiak is an institutional investor headquartered in Newport Beach, CA. Kodiak makes private investments in public and private entities utilizing proprietary equity and debt instruments. These investments provide long-term strategic capital offering companies certainty, flexibility and consistency. Kodiak’s investments are in a wide range of industries emphasizing alternative energy, consumer products, life sciences, natural resources, and social media technology. For more information, visit www.kodiak-capital.us.
About Cloud Security Corporation
Cloud Security Corporation is an innovative cloud computing company that creates security, technology, and products. The Company develops products in the remote-access computing sector including enhanced security connections. Cloud Security Corporation has developed patent-protected remote access security devices such as MyComputerKey(TM). The Company also develops online application security products and is expanding into other verticals.
Article source: http://www.darkreading.com/management/cloud-security-corporation-secures-2-mil/240161279
 57% of college students view their Facebook postings through rose-tinted glasses, blithely seeing nothing inappropriate.
57% of college students view their Facebook postings through rose-tinted glasses, blithely seeing nothing inappropriate. If college students need further help with keeping safe on Facebook, as in, keeping safe their chances of ever getting hired, it would behoove them to take a peek at one site that collates
If college students need further help with keeping safe on Facebook, as in, keeping safe their chances of ever getting hired, it would behoove them to take a peek at one site that collates  Three quarters of UK women support the Government’s proposals to make internet porn ‘opt-in’, according to a new survey from market research company Kantar.
Three quarters of UK women support the Government’s proposals to make internet porn ‘opt-in’, according to a new survey from market research company Kantar. The online poll, which used a representative sample of 1,234 people, also discovered that women especially felt that social media companies could play a bigger role in tackling online bullying and trolling, with 91% of women feeling that organisations such as Twitter and Facebook could be more proactive in tackling trolls and bullies.
The online poll, which used a representative sample of 1,234 people, also discovered that women especially felt that social media companies could play a bigger role in tackling online bullying and trolling, with 91% of women feeling that organisations such as Twitter and Facebook could be more proactive in tackling trolls and bullies. Mega-popular blogging and content management system WordPress has just put out version 3.6.1.
Mega-popular blogging and content management system WordPress has just put out version 3.6.1.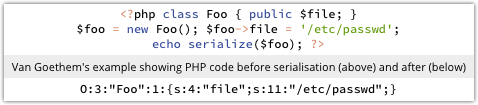
 Police are investigating yet another British newspaper group in the
Police are investigating yet another British newspaper group in the  He gives a pair of homework assignments for finding out what the remote access number is for your voicemail and how simple it might be for somebody to “hack” your number by simply calling and entering a default PIN (which can be as simple as the last digits of your phone number, for example).
He gives a pair of homework assignments for finding out what the remote access number is for your voicemail and how simple it might be for somebody to “hack” your number by simply calling and entering a default PIN (which can be as simple as the last digits of your phone number, for example).