New Apple iPhone 5s to feature “Touch ID” fingerprint authentication
After months of speculation, Apple has unveiled the latest iteration of its iPhones, with the usual fanfare and drama from Apple, and obsessive queuing from fans.
Catching most headlines have been the usual details of improved camera and battery life, and the availability of an “affordable” model, the 5c, a plastic affair in a wide range of colours. The main metal model will offer only gold, silver or grey.
Of most interest from a security viewpoint is a fingerprint-based authentication system in the top-of-the-line 5s, referred to as “Touch ID”.

The authentication system, based on a new material for the home button and a metal sensor ring around it, has been the subject of numerous rumours and leaked photos and specs already.
Speculation about Apple’s interest in fingerprints goes back at least as far as 2009, resurfaces each time a new version of the iPhone is launched, and has grown steadily ever since Apple’s pricey acquisiton of fingerprint tech firm AuthenTec last summer.
Today’s confirmation at the iPhone 5s/5c launch ceremony makes it all official at last.
According to Apple’s promotional material, the sensor:
uses advanced capacative touch to take, in essence, a high-resolution image of your fingerprint from the sub-epidermal layers of your skin. It then intelligently analyses this information with a remarkable degree of detail and precision.
 As well as unlocking the phone, the sensor will be able to approve purchases at the Apple store.
As well as unlocking the phone, the sensor will be able to approve purchases at the Apple store.
Fingerprint authentication has been a common sight in laptops for some time, with major vendors including Dell, Lenovo and Toshiba pushing their own built-in variations, usually available as an option alongside more traditional login methods.
There are also a range of other implementations available, including many smartphone apps and external readers supported by the Windows Biometric Framework and some leading password managers.
Fingerprints thus probably rank a little above facial recognition as the most widely-deployed biometric authentication technique at the moment.
In the past, however, they have proven rather unreliable, plagued with security worries, although suspected flaws are not always proven. Nevertheless, many fingerprint scanners seem to be open to spoofing.
Fingerprints are not secret: we leave copies of them wherever we go, even if we’re trying hard not to, as cop show afficionados will be well aware.
Once someone devious has got hold of a copy, purely visual sensors can be fooled by photographs, while more sophisticated techniques which measure textures, temperatures and even pulses are still open to cheating using flesh-like materials, or even gelatin snacks.
Just how hard it will be to defeat Apple’s recognition system remains to be seen, but as crypto guru Bruce Schneier has pointed out, there’s a big danger in using fingerprints to access online services: the temptation to store the fingerprint info in a central database.
Unlike passwords, of course, if your fingerprint data is lifted from a hacked database, you can’t simply change it, short of getting mediaeval on your hands with acid, sandpaper or some other hardened-gangster technique.
So, as expected, Apple has opted to keep all information local to the iPhone – indeed, it is apparently kept in a “secure enclave” on the new A7 chip and can only be accessed by the print sensor itself.
Expect this storage area and the connections to it to become the subject of frenzied investigations by hackers of all persuasions.
Of course, Apple is not alone in looking into fingerprints, with arch-rivals Samsung also rumoured to be making moves in that direction. (Samsung was a major customer of AuthenTec before it was acquired.)
In the long term, how similar their approaches are may be a significant issue for all of us, whatever our smartphone affiliation and whether or not we worry much about privacy, and not just thanks to the inevitable legal rumpus.
There are two basic approaches to security: either the way things work is kept proprietary and secret, as far as possible, or it’s made open for general consumption, and more importantly for verification.
 A cross-vertical group, the FIDO Alliance, was set up earlier this year to develop open specifications for biometric authentication standards, with members including Google, PayPal, hardware makers like Lenovo and LG, and a raft of biometrics and authentication specialists. Beleaguered phonemaker BlackBerry is the latest big-name inductee.
A cross-vertical group, the FIDO Alliance, was set up earlier this year to develop open specifications for biometric authentication standards, with members including Google, PayPal, hardware makers like Lenovo and LG, and a raft of biometrics and authentication specialists. Beleaguered phonemaker BlackBerry is the latest big-name inductee.
The alliance’s aim, to create a universal approach to implementing biometrics in combination with existing passwords and two-factor dongles, is a noble goal.
Sadly, given Apple’s history of playing well with others, it’s pretty likely that, as with their connector cables and DRM systems, their fingerprint setup will remain aloof from any attempts to build a truly universal consensus.
Even if a two-culture system prevails, widespread deployment in mass-market handhelds may well be a gamechanger for the adoption of biometric authentication. Touch ID and its inevitable followers could be a major part of all our futures.
Follow @VirusBtn
Follow @NakedSecurity
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/5V4x4PFGG8E/
 Linus Torvalds is a very clever man – he invented Linux, after all – but he seems to struggle with simple human decency.
Linus Torvalds is a very clever man – he invented Linux, after all – but he seems to struggle with simple human decency.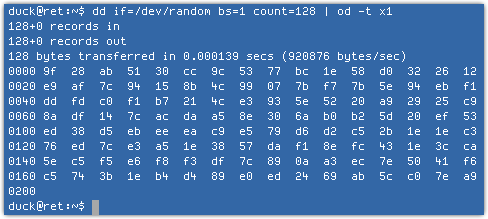
 After all, modern Intel CPUs have an instruction called RDRAND which is supposed to use thermal noise, generally considered an unpredictable byproduct of the fabric of physics itself, to generate high quality random numbers very swiftly.
After all, modern Intel CPUs have an instruction called RDRAND which is supposed to use thermal noise, generally considered an unpredictable byproduct of the fabric of physics itself, to generate high quality random numbers very swiftly.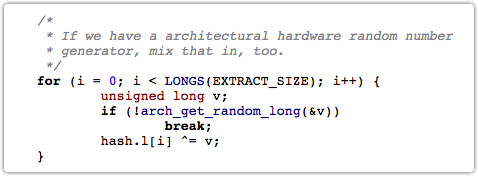

 A US appeals court has upheld a previous decision from a district court that ruled Google violated wiretap laws when it collected personal data from unencrypted Wi-Fi networks in 2010.
A US appeals court has upheld a previous decision from a district court that ruled Google violated wiretap laws when it collected personal data from unencrypted Wi-Fi networks in 2010. The internet search giant revealed this accidental collection of personal data back in May 2010, making a public apology at the time.
The internet search giant revealed this accidental collection of personal data back in May 2010, making a public apology at the time.