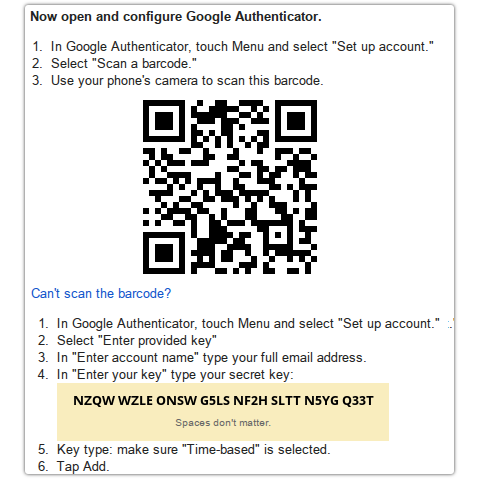
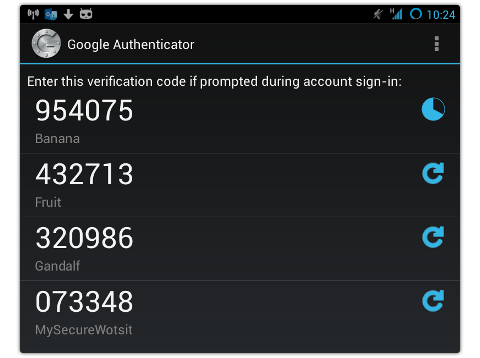
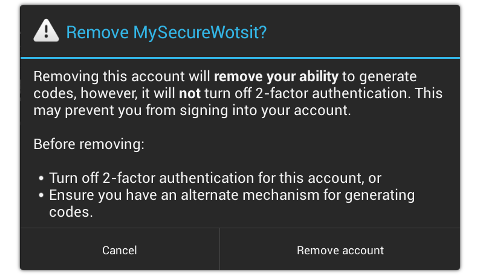
Tor traffic torrent: It ain’t the Syrians, it’s the BOTS
Win a Samsung 40-inch LED HDTV with The Reg and HP!
The recent spike in traffic on the Tor anonymizing relay network is probably due to botnet activity rather than any recent political developments, research by Tor Project members has concluded.
The overall number of clients accessing the Tor network on a daily basis has more than doubled since around mid-August, but so far researchers have been at a loss to find any reason for the increase.
Partly this is due of the design of the Tor network itself. Preserving users’ anonymity is the whole point of the project, so the network doesn’t keep logs of IP addresses or other identifying information that could help pin down where the extra traffic is coming from.
Members of the “Tor Talk” mailing list have posted numerous theories, ranging from increased activism in Syria, to public reaction to recent revelations about US surveillance operations, to an attempt by an unknown force to DDoS the Tor network itself. But according to Tor Project member Roger Dingledine, who has been investigating the matter for the past week or so, none of these is likely to be correct.
“The fact is, with a growth curve like this one, there’s basically no way that there’s a new human behind each of these new Tor clients,” Dingledine wrote in a blog post on Thursday.
Instead, Dingledine believes Tor client software was installed on millions of computers surreptitiously, “pretty much overnight,” probably hidden inside some other, as-yet-undetermined software package.
“Since no large software or operating system vendors have come forward to tell us they just bundled Tor with all their users, that leaves me with one conclusion: somebody out there infected millions of computers and as part of their plan they installed Tor clients on them,” he wrote.
The most likely explanation is that someone is trying to set up a botnet that uses the Tor network to conceal the source of its packets. The problem, Dingledine observes, is that Tor wasn’t really designed with that kind of traffic in mind.
“My first observation is ‘holy cow, the network is still working’,” he wrote. “I guess all that work we’ve been doing on scalability was a good idea.”
There is still more work to be done, however, and the increase in traffic has caused measurable strain on the network. What steps the Tor Project will take to make the network more resilient to botnets and other anomalous traffic spikes are still open to debate. For now, Dingledine encourages all Tor users to upgrade to Tor 0.2.4, which introduces a new connection-handshaking method that uses fewer CPU resources.
“In parallel, it would be great if botnet researchers would identify the particular characteristics of the botnet and start looking at ways to shut it down (or at least get it off of Tor),” Dingledine says.
“And finally, I still maintain that if you have a multi-million node botnet, it’s silly to try to hide it behind the 4000-relay Tor network … Another facet of solving this problem long-term is helping them to understand that Tor isn’t a great answer for their problem.” ®
Win a top of the range HP Spectre laptop
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/09/05/tor_traffic_spike_botnet/
 The good news is that the problem isn’t
The good news is that the problem isn’t