Another 5 tips to help keep you safe on Facebook
Last month we gave you 5 tips to make your Facebook account safer. Following on from that, here’s another five…
1. Stop search engines from indexing your profile
Facebook’s great for keeping in touch with friends and family but you might not want just anyone finding your profile via Google or other search engines. Here’s how to fix that:
Click on the cog icon at the top right of your screen and then click Privacy Settings.
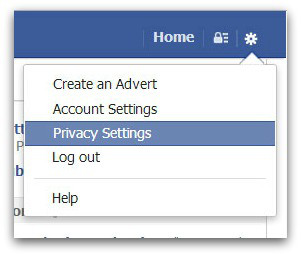
Now that you are in the Privacy Settings and Tools area of Facebook, find ‘Who can look me up?’ and the setting that says ‘Do you want other search engines to link to your timeline?’
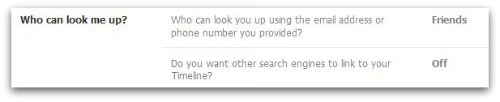
This is likely on by default, so click Edit and then remove the tick from the box which says ‘Let other search engines link to your timeline’.
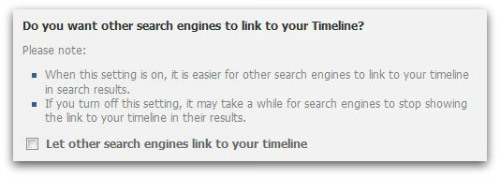
Note: It may take a bit of time for search engines to stop showing the link to your timeline in their results so don’t expect it to disappear immediately from search results.
2. Block someone on Facebook
Just as in real life, some people on the web can prove challenging for a number of reasons. If you don’t want someone to see your profile or things you write on Facebook, you can block them – and here’s how to do just that.
Click on the padlock icon that you see in the top right hand corner of the screen. Now click on How do I stop someone from bothering me?
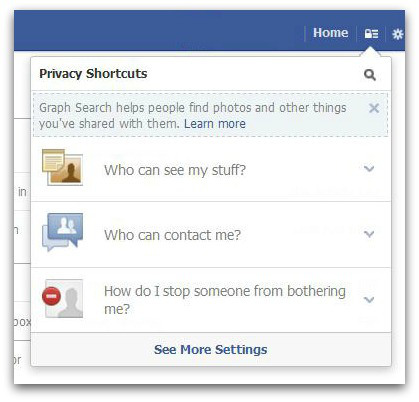
Now either enter a name or email address and click Block.
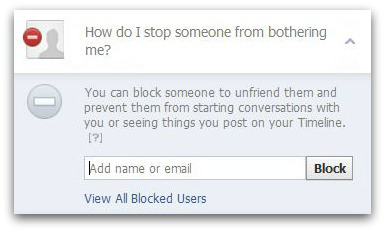
The person you block won’t get any notification that they’ve been blocked and they will now no longer be able to initiate conversations with you or see anything that you post on your timeline either.
3. Public computer? Use a one-time password
If you would like to use Facebook from a public location, such as a computer in an internet cafe or library, you can use a one-time password to access your Facebook account, keeping your actual password safe. This password is sent to you by text message and will expire after 20 minutes.
Note: you do have to link your mobile number with your Facebook account in order to use this function.
All you need to do is send “otp” as a text message to the number listed next to your country and mobile carrier on the one-time password list on Facebook. If you’re in the US, you can send the same message to 32665. Unfortunately, it isn’t available everywhere, and the number of countries and carriers is fairly limited at the moment.
After you’ve sent the message, you will receive a reply from Facebook with your OTP, a one-time password of eight characters (or with instructions on how to link your mobile to your Facebook account).
You can now login to Facebook in the normal way, substituting this temporary password for your regular one.
*Always* remember to sign out of Facebook once you are finished, especially if you are signed in on a public computer. If you do leave your account signed in the next person to use the computer will have access to it, even without your password.
→ Even though we’ve just showed you how to use OTPs, we recommend avoiding public computers, such as those in libraries and internet cafes, as much as your digital lifestyle will permit. At the least, work on the (admittedly pessimistic) assumption that anything you type in or view on screen may be sent to cybercrooks, and stick to things you don’t mind being public.
4. Block an app from accessing your information
If you already have an app installed on Facebook but you now want to prevent it from accessing your personal information then blocking it is quite simple.
Click on the cog icon found at the top right of the screen and then click on Account Settings.
Look to the left pane and click on the fifth option from the top; Blocking.

Then look for the last option – Block apps.
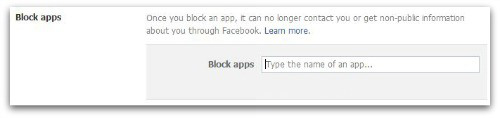
All you need to do is put in the name of the app you want to block and then press enter.
5. Remove something from your timeline
If you or someone else has put something on your timeline which you want to remove, it’s pretty easy to do.
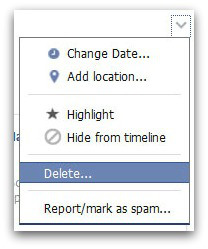
Firstly, navigate to your timeline and find the story you wish to block from appearing. Next, move your mouse to the top right corner of the story and you will see what looks like an arrow head appear. Click on that and you’ll be shown a box.
You now have two options here. You can either choose to Hide from timeline which will stop the post from showing on your page (but it will still appear in newsfeeds and search).
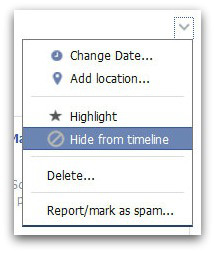
Or you can remove it completely by clicking on Delete.
This is just a small selection of tips to help you safeguard your Facebook profile. If you have any others please do add them in the comments below.
And if you would like to stay up to date on the latest Facebook scams and other internet threats then please do consider liking the Naked Security page on Facebook if you haven’t done so already.
Follow @SecurityFAQs
Follow @NakedSecurity
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/UaoyK6vEorU/
 Researchers regularly come up with revolutionary ideas to replace the clunky, fiddly and mostly rather insecure passwords we use for almost all of our authentication needs.
Researchers regularly come up with revolutionary ideas to replace the clunky, fiddly and mostly rather insecure passwords we use for almost all of our authentication needs.  The biostamp idea proposed a hybrid of body and technology.
The biostamp idea proposed a hybrid of body and technology.