Shavlik Powers Up Mobile Capability With Mobile Device Management
MINNEAPOLIS, Sept. 3, 2013 /PRNewswire/ — Shavlik is pleased to announce the release of Shavlik Mobile Device Management (MDM) for the management of smartphones, tablets and rugged devices. As IT departments realign to the new realities of User-Oriented IT, they are coming to terms with securing a mobile, global, 24-hour workplace. One of the central considerations in this IT shift is the need to secure a diverse set of mobile devices. To fulfill this pressing IT need, Shavlik has created Shavlik Mobile Device Management. This product is a rich addition to Shavlik’s legacy in agentless endpoint patching technology, virtualization security, and third party patching as well as an easy-to-use means of managing Windows, Android, and iOS devices.
The new world of device management and security extends beyond the office and the domain of servers, workstations and desktops to devices that roam the mobile space. Keeping track of mobile devices while ensuring a company’s data is safe presents a host of challenges to IT. These challenges are amplified by daily news headlines related to stolen or compromised data that have been contained on unsecured devices. In addition to the crush of corporate mobile devices, IT departments must manage employee devices used for business (BYOD). This increases the pressure to find robust, affordable and easy to use mobile management software.
Shavlik Mobile Device Management provides a comprehensive, integrated mobile device management solution that helps customers handle operational and IT transformation with ease and efficiency. Shavlik’s mobile device management solutions enable enterprise IT and business operations organizations to reduce the time, cost, and risks associated with managing mobile devices and business critical application delivery. Shavlik MDM streamlines and automates mobile device and infrastructure management tasks across, wireless LAN and WAN, and ensures that the wireless environment is secure.
“Today it is simply not enough to maintain the security of desktops, workstations and servers,” said Robert Juncker, vice president of engineering, Shavlik. “The new measure of protection is protecting your data wherever it is and Shavlik has its customers covered with Shavlik MDM.”
Shavlik MDM Suite Benefits
— Manage Any Device – Leverage a single consolidated mobile management
solution that allows you to manage every aspect of your mobile devices –
both rugged and smart devices – as well as the business critical and
consumer applications they utilize
— Minimize Risk – Eliminate complexity through a validated solution and
fully integrated mobile device and application management technology
— Improve ROI – Leverage the full functionality of a complete mobile
device and application management solution in a single integrated,
Web-based console
— Increase User Productivity – Redefine your user experience by providing
the industry’s most comprehensive mobile management solution designed to
dramatically increase business efficiencies and significantly increase
user productivity
Shavlik MDM enables companies to:
— Lock out apps
— Control rights and permissions to corporate systems (e.g. Exchange,
Intranet, CRM)
— Remote kill / wipe for lost or stolen devices
— Locate and map devices
— Remotely install and update applications and operating systems
— Troubleshoot and monitor the health of mobile devices For more information on the Shavlik Mobile Device Management suite please contact your Shavlik sales representative.
About Shavlik
Shavlik is a pioneer in agentless patch management and a leader in innovative network security and management solutions. Since 1993, Shavlik has been at the forefront of patch security, first by providing the only third-party patch management to Microsoft SCCM customers and later asserting industry leadership in the patching of virtual machines. Its products and solutions include Shavlik Protect, Shavlik SCUPdates, and Management Intelligence.Shavlik’s “Just Add Water and Stir” approach allows customers to get up and running in as little as thirty minutes.
Article source: http://www.darkreading.com/management/shavlik-powers-up-mobile-capability-with/240160738
 Aberdeen City Council has been
Aberdeen City Council has been 

 The ongoing data leak saga between medical firm LabMD and “The Man,” in the form of the Federal Trade Commission (FTC) of the United States, has entered its next stage.
The ongoing data leak saga between medical firm LabMD and “The Man,” in the form of the Federal Trade Commission (FTC) of the United States, has entered its next stage. Daugherty’s doughtily-named book claims to document “a government power grab and intimidation that if not for the fact that it is all real, would make for an a brilliant novel.”
Daugherty’s doughtily-named book claims to document “a government power grab and intimidation that if not for the fact that it is all real, would make for an a brilliant novel.” An Indian electronics and communications engineer who describes himself as a “security enthusiast with a passion for ethical hacking” has
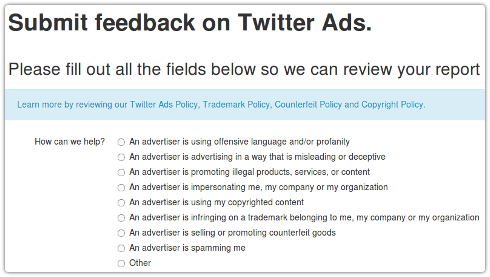
An Indian electronics and communications engineer who describes himself as a “security enthusiast with a passion for ethical hacking” has 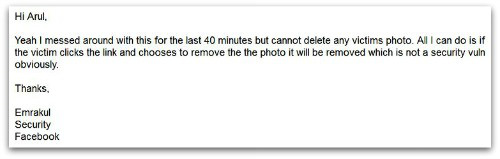

 The ongoing data leak saga between medical firm LabMD and “The Man,” in the form of the Federal Trade Commission (FTC) of the United States, has entered its next stage.
The ongoing data leak saga between medical firm LabMD and “The Man,” in the form of the Federal Trade Commission (FTC) of the United States, has entered its next stage. Daugherty’s doughtily-named book claims to document “a government power grab and intimidation that if not for the fact that it is all real, would make for an a brilliant novel.”
Daugherty’s doughtily-named book claims to document “a government power grab and intimidation that if not for the fact that it is all real, would make for an a brilliant novel.” A soldier was made to sign a non-disclosure agreement by the US Army after pointing out a security flaw which allowed accounts on shared PCs to be accessed without proper authentication.
A soldier was made to sign a non-disclosure agreement by the US Army after pointing out a security flaw which allowed accounts on shared PCs to be accessed without proper authentication.