SUNNYVALE, Calif. — Aug. 27, 2013 — Centrify Corporation, the leader in Unified Identity Services across data center, cloud and mobile, today announced the availability of the Centrify User Suite, Mac Edition — the industry’s first solution to provide robust Active Directory-based authentication, policy management, single sign-on (SSO) and user self-service for connected and remote Mac OS X systems. With Centrify User Suite, Mac Edition (“Centrify for Mac”), on-premise and remote Macs and mobile devices are seamlessly integrated into Microsoft Active Directory (AD), leveraging organizations’ existing AD infrastructures, processes and skill sets to deliver enhanced security and easy management for IT, and simplified, secure access for Mac users at work.
Centrify is adding significant capabilities to Centrify for Mac. As a complement to its historic agent-based approach for providing Active Directory-based authentication and Group Policy management, Centrify has now added a cloud-based option for managing Macs. By extending the Centrify Cloud Service to manage remote Macs and providing administrators and users with self-service capabilities such as remote lock and remote wipe of a Mac, IT staff for the first time have the flexibility to use a single solution to manage Macs using a combination of both on-premise software and/or a cloud-based offering.
Also, Centrify is combining its Centrify for Mobile offering as part of the Centrify for Mac solution to deliver a new combined solution based on a per-user subscription pricing, allowing IT staff to manage their employees’ multiple devices — including Macs, iOS and Android devices — under an economical single per-user license, making Centrify unique in the market. In addition, data on Mac systems is now secured through centrally managed File Vault 2 full-disk encryption security policies and institution encryption keys to ensure protection of data at rest on these highly portable systems.
“With more than 10,000 students, faculty and staff across 23 facilities, we had to standardize on a unified identity approach for authentication and access rights that would enhance our security for all our public records and to ensure confidentiality for our user base,” said Cory Gearhart, executive director of Information Technology at Grand Island Public Schools. “Centrify was the unique vendor that was able to meet our IT needs for centralized access management of our Mac environment while also satisfying our users by providing a single set of login credentials for any computer or device to access a range of new applications and educational resources.”
“The Bring Your Own” trend involving Macs, mobile devices and new mobile applications means that IT organizations increasingly don’t own the endpoint devices or back-end application resources on their networks. At the same time, end users are increasingly challenged to deal with the password sprawl associated with the on-premise and cloud-based services they need to access in order to perform their jobs. Centrify provides a unified approach to managing an employee’s digital identity that spans their applications, Macs and mobile devices, providing the visibility and control required for IT organizations to achieve compliance, reduce costs and mitigate risks, while also increasing productivity and securing access for their user centric, mobile workforce.
One Directory to Manage “Bring Your Own Mac” and BYOD Environments
In many organizations, Macs are becoming more prevalent and disconnected from the corporate network, requiring a hybrid on-premise and cloud-based approach to comprehensively manage authentication, configure security policies, and enable user self-service features regardless of device location. At the same time, Apple is increasingly enabling Bring Your Own Mac with remote management and policy configuration for Macs based on technology similar to how Apple iPhones and iPads are managed today.
Centrify for Mac provides organizations with centralized administration, strengthened security, and simplified user experience through SSO across their users’ multiple mobile (iOS and Android) and computing devices. New capabilities in the solution include:
• Optional Enrollment of Macs in the Centrify Cloud Service Platform — for management of disconnected or remote Macs, user self-service, and support for new OS X Profiles being introduced by Apple. This allows IT administrators to extend self-service features to remote users, such as data protection via remote wipe or lock of stolen or misplaced Macs, and enables IT to apply new MDM profiles for Macs and mobile devices for auto configuration of VPN and Wi-Fi, including automated PKI certificate management for strong authentication.
• Integrated BYOD and Mac Offering — Centrify is combining its Mac management with its Centrify for Mobile offering to deliver a new combined solution based on a more economical per-user subscription pricing. Centrify’s pricing has changed from a per-device, perpetual license to a per-user subscription model, with support for up to five devices, in order to support users’ increasing use of Macs, smartphones and tablets as a natural extension of their work environment. Ideal for “Bring Your Own Mac” and BYOD environments, organizations get more functionality with support for a greater number of devices at a more economical price.
• Enhanced Mac Security Management Features — Centrify has added File Vault 2 full-disk encryption security policies. And as part of its smart card support for the Mac platform, Centrify has also added smart card name mapping, also known as the Alternate Identity Smart. Centrify for Mac ensures trusted security functions with FIPS-certified cryptographic services to meet the highest levels of security requirements, and supports Mac smart cards including Common Access Card (CAC) and (Personal Identity Verification) PIV.
• Enhanced Mobile Features — New Apple iOS features include support for volume purchase programs and MyCentrify app optimized for iPads. New Android features include support for more than one hundred security policies for Samsung SAFE devices for controlling passwords, Exchange email, Wi-Fi, Bluetooth, firewall settings, roaming policies and much more.
“Increasingly we find that knowledge workers and other end users have anywhere from two to four computing devices each as users continue to work while they are mobile,” said David McNeely, Centrify senior director of product management. “With Centrify, organizations can easily secure and manage access and authentication for all the devices users need. The bottom line is that users get single sign-on from any device to any app to help them be more productive at work, while enterprise IT centrally manages and secures all applications and devices these users need for their work.”
Pricing and Availability
The new Centrify User Suite, Mac Edition is available today from Centrify and authorized partners worldwide. Pricing is $48 per user/year for up to five devices (any combination of Mac and/or Mobile devices per user) and includes standard support. Centrify User Suite, Premium Edition is also available and combines Centrify for SaaS with Centrify for Mac to provide users with single sign-on to an unlimited number of web and SaaS applications, as well as Mac and mobile management, and is priced at $72 per user/year for use on up to five devices and unlimited SaaS apps. To learn more, or to obtain a free trial, visit http://www.centrify.com/mac.
About Centrify
Centrify provides Unified Identity Services across the data center, cloud and mobile that results in one single login for users and one unified identity infrastructure for IT. Centrify’s solutions reduce costs and increase agility and security by leveraging an organization’s existing identity infrastructure to enable centralized authentication, access control, privilege management, policy enforcement and compliance. Centrify customers typically reduce their costs associated with identity lifecycle management and compliance by more than 50%. With more than 5,000 customers worldwide, including 40% of the Fortune 50 and more than 60 Federal agencies, Centrify is deployed on more than one million server, application and mobile device resources on-premise and in the cloud. For more information about Centrify and its solutions, call (408) 542-7500, or visit http://www.centrify.com/.
Article source: http://www.darkreading.com/end-user/centrify-delivers-unified-identity-solut/240160477
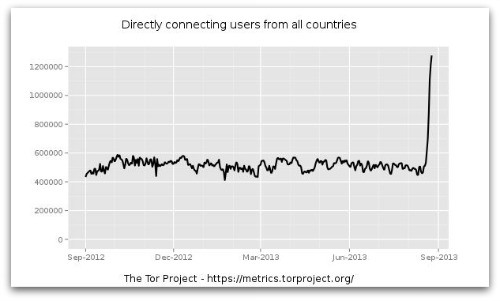
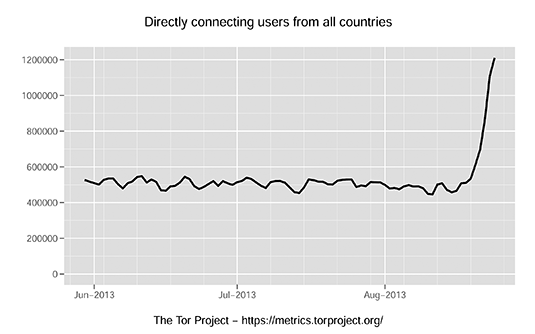
 Other significant events that may have led to an increase in Tor usage during August include the sudden and voluntary closing of secure email providers Lavabit, used by Snowden, and Silent Circle on 8 August.
Other significant events that may have led to an increase in Tor usage during August include the sudden and voluntary closing of secure email providers Lavabit, used by Snowden, and Silent Circle on 8 August.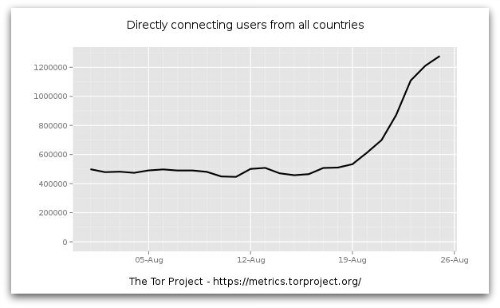 The folk on the tor-talk mailing list are suspicious too. The last exchange on the subject reflects a feeling among some that the growth is unnatural:
The folk on the tor-talk mailing list are suspicious too. The last exchange on the subject reflects a feeling among some that the growth is unnatural: Six months ago, we wrote about a
Six months ago, we wrote about a