The Syrian Electronic Army (SEA)’s hijacking late yesterday of the Internet domains of The New York Times, two Twitter services, and The Huffington Post’s UK site initially set off alarm bells over a potential domain-name system (DNS) security meltdown, but it appears the political hacktivist group’s modus operandi and mission were much more simple and straightforward.
It all started with a spearphishing email that duped a U.S. reseller of domain registrar Melbourne IT, which hosts The New York Times, Twitter, The Huffington Post, and other sites. But despite the SEA basically acquiring keys to the kingdom with potential access to Melbourne IT’s other high-profile domain customers, such as Google.com, Microsoft.com, Yahoo.com, Cisco.com, and Adobe.com, the hacktivists merely concentrated on controlling the domains of The New York Times, Twitter’s twimg.com image service and t.co URL-shortening service, and huffingtonpost.co.uk.
“There were tons of other domains [registered with Melbourne IT] that were a much better target. And they didn’t have a ‘lock’ in place — like mcafee.com, symantec.com, and cisco.com,” says HD Moore, chief research officer at Rapid7 and creator of Metasploit, who has been tracking the attacks. “They were really focused … The hack was really clunky, the redirects didn’t work for very long.”
What remains unclear is just what restrictions, if any, were in place for the compromised domain reseller to modify other domains under Melbourne IT’s purview, Moore says.
Moore says The New York Times’ email and other domains also were exposed in the attack, but it doesn’t appear the attackers went after them. “Any of the companies who did not have a lock in place would have been potentially vulnerable to unauthorized changes to their DNS servers, which, in turn, could allow incoming email to be stolen, which can also lead to rogue SSL certificates being created in their name via domain name validation,” he says.
A Cisco spokesperson says the company’s CSIRT team is working on locking down cisco.com with a registry lock.
Employing a so-called registry lock would have deflected the attack, a technique that Melbourne IT is now recommending for its high-profile customers. This measure basically prevents any modification by the registrar or any other registrar to the domain name or its contact information. Moore in his research found that twitter.com did, indeed, have such a lock in place, which saved the social network from massive disruption, but others did not.
In the past 16 hours, Moore found that the huffingtonpost.com, mapquest.com, patch.com, starbucks.com, techcrunch.com, tweetdeck.com, twimg.com, and vine.co domains, as well as others, all had applied the lock feature. Twitter’s t.co URL-shortening service that was hit by the attack has now been moved to a different registrar, he says.
There’s no evidence the SEA altered any of the exposed domains, he says, but it would have been possible with the access they gained in the hack. “Things could have been much worse,” Moore says.
Among the domains hosted by Melbourne IT that have not been locked down as of this posting are adobe.com, barnesandnoble.com, bbandt.com, cisco.com, ibm.com, mcafee.com, norton.com, prnewsire.com, symantec.com, tweetdeck.com, and vmware.com, according to Moore’s data.
“For mission critical names we recommend that domain name owners take advantage of additional registry lock features available from domain registries including .com – some of the domain names targeted on the reseller account had these lock features active and were thus not affected,” Melbourne IT said in a statement to its customers that was included in a blog post by Matthew Prince, co-founder and CEO of CloudFlare, a Web infrastructure and security company. “The credentials of a Melbourne IT reseller (username and password) were used to access a reseller account on Melbourne’s IT systems. The DNS records of several domain names on that reseller account were changed — including nytimes.com.”
Melbourne IT had not responded to requests for comment as of this posting. Several reports quote the registrar as confirming that the attack came from a spearphishing email sent to one of its resellers.
CloudFlare’s Prince also recommends using a registry lock on domains. “There is one sensible measure that domains at risk should all put in place immediately. It is possible to put what is known as a registry lock in place for your domain. This prevents even the registrar from making changes to the registry automatically. If you run a whois query against your domain, you can see if you have a registry lock in place if it includes three status lines: serverDeleteProhibited, serverTransferProhibited, and serverUpdateProhibited,” Prince said in his post.
The trade-off of employing a registry lock is that it makes automatic renewal more complicated. “There is more administrative overhead,” says David Ulevitch, CEO at OpenDNS. “It can be super-effective, and it can also be a pain. The trade-off is flexibility … that’s the nature of security.”
Malware Mystery
Meanwhile, the malware component of the attack still has security researchers baffled. The New York Times’ URL was redirected to a malware-poisoned site, which was up and down during the attack.
The fact that the SEA incorporated a malware redirect is “significant,” says Andre DiMino, a security researcher with DeepEnd Research. “If their sole purpose was to deface and get their message out, yet they are still piggybacking malware redirection to monetize [their attack], that’s a significant development.”
DiMino says without knowing what the malware is or does, it’s difficult to determine what this twist to the attack means.
It’s not clear why the malware was involved, Rapid7’s Moore says. It could have been in place to set up a longer-term attack, he says, but given how short the malware site was up and running, it wouldn’t have made much of an impact.
“From 3 p.m. and on, the website only loaded once or twice,” Moore observed.
The one sure thing is that the end user continues to be the weakest link, and phishing remains the tried-and-true method of snaring victims. “You can have all the technical controls, patching, and pen test your networks to death. But just a simple email that looks really great allows access to the network,” DeepEnd Research’s DiMino says.
Know Your Registrar
The SEA’s attacks were a vivid reminder of the delicate trust relationship with a domain registrar, one that is often forgotten until it’s time to renew the domain registration. The way the attackers breached The New York Times and the others via Melbourne IT and gained control of its registry records is a supply chain wake-up call, experts say.
“It makes it all the more compelling for companies today — to understand and secure the digital linkages they’re making with their partners, suppliers, social networks, and content vendors, as in this particular case. The application layer remains an easy target that hackers exploit to retrieve the company’s most sensitive data, financial information, and records,” says Bala Venkat, chief marketing officer for Cenzic.
Rapid7’s Moore recommends keeping tabs on your domains and regularly confirming that you “still own them.”
[From the Washington Post and CNN to the Twitter feeds of the Associated Press and Reuters, hacktivists have news outlets — and their social-media presence — in their crosshairs. See How Hacktivists Have Targeted Major Media Outlets.]
The relatively good news was that the SEA, which supports Syrian president Bashar al-Assad, kept to its hacktivist roots. “They were brilliant and stupid at the same time,” OpenDNS’s Ulevitch says, noting how the redirected URLs struggled to remain online. A worst-case scenario would have been that they would have used their attack to embed a zero-day Flash exploit via Twitter and amassed a 10 million-host botnet, he says.
“It was high-profile, certainly — they got a lot of publicity for it,” Ulevitch says. “But there aren’t a lot of IT admins cleaning up today because 10 million computers were infected by a botnet.”
“This was more of a modern-day defacement than a real intrusion,” Rapid7’s Moore says.
Have a comment on this story? Please click “Add Your Comment” below. If you’d like to contact Dark Reading’s editors directly, send us a message.
Article source: http://www.darkreading.com/attacks-breaches/syrian-electronic-army-strikes-again-in/240160551
 Pinterest and StumbleUpon have patched critical vulnerabilities in their services that could have enabled an attacker to discover users’ email addresses.
Pinterest and StumbleUpon have patched critical vulnerabilities in their services that could have enabled an attacker to discover users’ email addresses.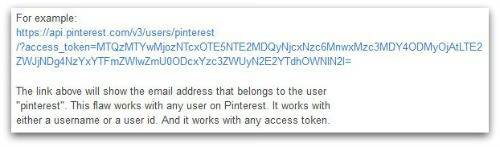
 The security researcher had an altogether different experience with StumbleUpon, a site that caters to some 30 million users. He discovered a similar flaw that allowed him to view the name, age, gender, location and email address of any of its users but was unable to gain permission to reveal the exploit.
The security researcher had an altogether different experience with StumbleUpon, a site that caters to some 30 million users. He discovered a similar flaw that allowed him to view the name, age, gender, location and email address of any of its users but was unable to gain permission to reveal the exploit.
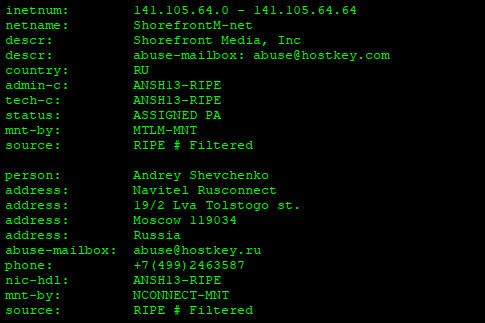
 Slightly more than a week after the Syrian Electronic Army (SEA) redirected readers of Time, CNN and The Washington Post through its
Slightly more than a week after the Syrian Electronic Army (SEA) redirected readers of Time, CNN and The Washington Post through its 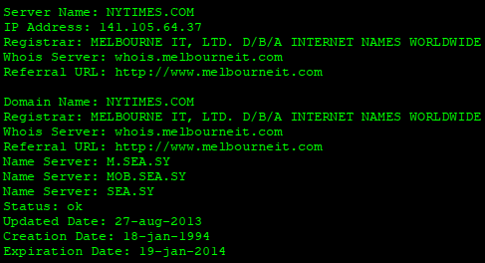
 I hear from many IT professionals at conferences, seminars and customer engagements that their management wants to know that they are “secure”. The answer they want is an answer you really shouldn’t give.
I hear from many IT professionals at conferences, seminars and customer engagements that their management wants to know that they are “secure”. The answer they want is an answer you really shouldn’t give.