NSA to world+dog: We’re only watching 1.6% of internet, honest
Win Spectre Laptop with HP and The Register
The US’s National Security Agency (NSA) has issued a document titled The National Security Agency: Missions, Authorities, Oversight and Partnerships (PDF) that explains some of its operations – and includes a claim it “… touches about 1.6 per cent… “ of daily internet traffic and “…only 0.025 per cent is actually selected for review”.
Released on Saturday with little fanfare – albeit amid fresh claims that the spook nerve-centre is scrutinising every email in and out of the US – the document’s prologue explains that the NSA lacked tools to track one of the 9/11 hijackers. As a result “several programs were developed to address the U.S. Government’s needs to connect the dots of information available to the intelligence community and to strengthen the coordination between foreign intelligence and domestic law enforcement agencies”.
It goes on to detail the legal underpinnings of the agency’s work and identify the following methodology for its operations:
- NSA identifies foreign entities (persons or organizations) that have information responsive to an identified foreign intelligence requirement. For instance, NSA works to identify individuals who may belong to a terrorist network.
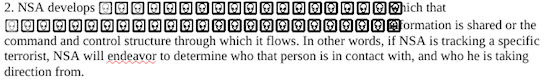
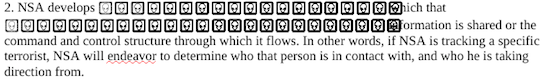
- NSA develops “the network” with which that person or organisation’s information is shared or the command and control structure through which it flows. In other words, if NSA is tracking a specific terrorist, NSA will endeavor to determine who that person is in contact with, and who he is taking direction from.
- NSA identifies how the foreign entities communicate (radio, e-mail, telephony, etc.)
- NSA then identifies the telecommunications infrastructure used to transmit those communications.
- NSA identifies vulnerabilities in the methods of communication used to transmit them.
- NSA matches its collection to those vulnerabilities, or develops new capabilities to acquire communications of interest if needed.
The money shot comes in a section titled “Scope and Scale of NSA Collection” that reads as follows:
“According to figures published by a major tech provider, the Internet carries 1,826 Petabytes of information per day. In its foreign intelligence mission, NSA touches about 1.6% of that. However, of the 1.6% of the data, only 0.025% is actually selected for review. The net effect is that NSA analysts look at 0.00004% of the world’s traffic in conducting their mission – that’s less than one part in a million.”
It also means the NSA is “touching” a couple of terabytes a day. And let’s also ponder just what “selected for review” means. Is it reading by humans? Processing by machines? Perhaps the probe launched by President Obama into his spooks’ activities will reveal all.
The NSA would have us believe that whatever’s going on, “NSA personnel are obliged to report when they believe NSA is not, or may not be, acting consistently with law, policy, or procedure”.
“This self-reporting is part of the culture and fabric of NSA,” the document continues. “If NSA is not acting in accordance with law, policy, or procedure, NSA will report through its internal and external intelligence oversight channels, conduct reviews to understand the root cause, and make appropriate adjustments to constantly improve.”
The Reg imagines leakers workings for contractors were not on the NSA’s list of “external intelligence oversight channels”. Whistleblower Edward Snowden thrusting himself into that role may be the reason this document was published. ®
Bootnote
Here at Vulture South we write in a word processor (Lotus Symphony) and then enter the results into The Reg‘s content management system. While cutting and pasting sections of the document into Symphony, we found some oddities.
For example, the list describing the NSA’s methodology, in point 2, looks like this even when pasted unformatted:
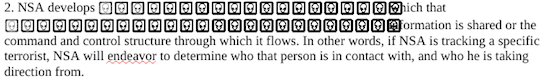
We found several such instances throughout the document and imagine it is the NSA’s idea of a joke.
Win Spectre Laptop with HP and The Register
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/08/12/nsa_says_it_only_watches_one_point_six_per_cent_of_the_internet/