Customer Success Testimonial: Recovery is Everything
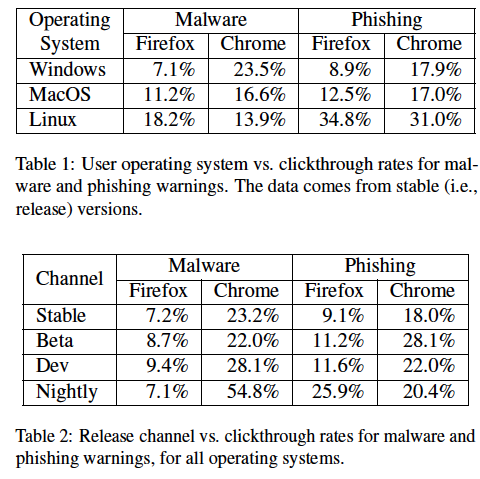
The Chinese hacking crew that made headlines worldwide after a high-profile series of attacks against the New York Times last year has returned with assaults against South East Asia, at least according to threat intelligence firm Cyber Squared.
The latest attacks are unusual because instead of using standard tactics such as spear phishing, they feature a malicious document delivered via Dropbox.
The innocent-looking Word document contains a malicious embedded custom backdoor that interacts with a WordPress blog used as the command-and-control channel by the hackers.
The attackers have simply registered for a free Dropbox account, uploaded a document that contains embedded malware, and then publicly shared it with their targeted users.
The shift in tactics offers benefits for cyberspies because it means that victims are less likely to realise they are even under attack.
Many organisations are not scrutinising web traffic to services such as WordPress or Dropbox, which are far less likely to raise alarm bells than unexplained links to IRC chat servers in China, for example. As an added bonus, malware can be distributed via essentially anonymous accounts on Dropbox, so attackers are less likely to be traced.
How it works
The malicious documents deliver a backdoor called Yayih using a Flash exploit, as a blog post by Cyber Squared on the attack explains. Yayih has previously been associated with other APT-style attacks.
After the malware has placed copies of itself in the victim’s PC’s systems folders, it contacts a hacker-controlled WordPress blog, which also contains links to other blogs containing coded instructions for compromised zombie drones.
“Traditionally attackers compromise their midpoint infrastructure – such as web servers and SMTP relays – to launch and maintain their targeted attacks,” Adam Vincent, chief exec of Cyber Squared, explained.
“In this case, the attacker used Dropbox to distribute the malware and WordPress for first-stage command and control. This represents a shift from existing methods where attackers leverage their own infrastructure to directly spear-phish and interact with their victims.”
Political motivations?
The attack appears to be targeted at individuals and organisations associated with commerce and trade within the Association of Southeast Asian Nations (ASEAN) member nations.
“One of the documents used in the attack (the decoy document) was a US-ASEAN business council internal memo,” Vincent explained. “The document that was opened when the victim clicked on the malicious attachment was a decoy document so the user was unaware that they had been compromised.
“This suggests the recipients would likely have an interest in, or an affiliation with the ASEAN [so] most likely [would be] individuals or representatives of regional member nations.
“The ASEAN itself, as well as many of the associated regional member nations, would be of strategic diplomatic, economic, or military interest to China,” he added.
The ASEAN is an international, non-governmental, geo-political and economic association that represents the interests of 10 south-east Asian countries. Cyber Squared reckons a Chinese hacking crew is to blame.
“Based on threat intelligence of this particular threat developed within ThreatConnect.com, it is highly likely that this activity is part of the same Chinese APT threat group that compromised the New York Times for several months during the fall of 2012 and again in the spring of 2013,” the security intelligence firm concludes.
“This incident reinforces that Comment Crew, aka APT1, is not the only Chinese Advanced Persistent Threat (APT) group using web-enabled content as a command and control technique to interact with their victim’s hosts.”
Vincent told El Reg: “Anyone within ASEAN would have been fair game.”
The Dropbox ASEAN hackers are thought to be based in Beijing and are sometimes known as the DNSCalc gang, the researchers claim. The group has targeted media organisations in the Philippines and other victims in the region before.
The more famous APT1 crew has been linked to a PLA division based in the suburbs of Shanghai.
Rob Kraus, a director of research at managed security services firm Solutionary, said Cyber Squared’s findings illustrate the need for Dropbox and WordPress to develop a “process for taking down or disabling accounts if they are identified as malware/APT CC hosts”.
It came from the CLOUD
The abuse of cloud-based systems by malware authors and cyberspies itself comes as no great surprise, according to Kraus.
“Cloud infrastructure has been used to host malware content used in conjunction with droppers and downloader components for malware for some time,” Kraus explained.
“Regardless of whether or not this is an APT or standard mass-distributed malware, it is not real surprise the attackers are using legitimate infrastructure and cloud computing to accomplish their goals.”
Cyber Squared reached its findings based on data from its ThreatConnect community, a collaborative cyber intelligence exchange whose members include government agencies, banks, non-profits, and manufacturers in various industries. The exchange – run by Cyber Squared and akin to a neighbourhood watch scheme – collects, analyses and shares threat intelligence. ®
Requirements Checklist for Choosing a Cloud Backup and Recovery Service Provider
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/07/12/apt_crew_abuse_dropbox_hit_se_asia/