Crimelords: Stolen credit cards… keep ’em. It’s all about banking logins now
Ensure Ease of Recovery with Asigra’s Agentless Software
Stolen bank login information attracts an even higher price than credit card numbers on underground cybercrime bazaars, and EU logins are worth more than American ones, according to research by McAfee.
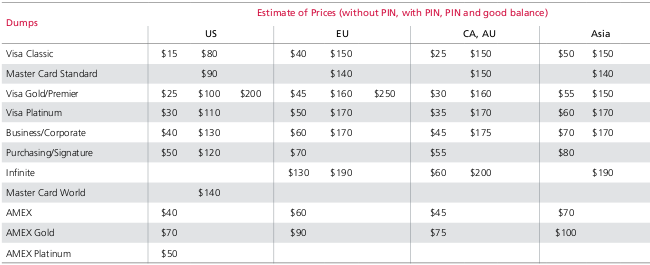
The Intel-owned security division’s Cybercrime Exposed paper highlights trends in the thriving digital underground, including the ease with which criminals can buy personal information online. For example, buying credit card details without a PIN costs around £16 apiece, a price that rises to £65 with a PIN or £130 with a PIN and a guaranteed good balance.
European Union online banking logins cost 4–6 per cent of the account balance while US online banking logins cost 2 per cent of the account balances. That means an online banking account with a £3,000 plus balance or an American equivalent with $8,000 is worth more these days than a credit card record even in cases where a crooks is also offering to sell a PIN number.
McAfee researchers also discovered that PayPal logins cost six to 20 per cent of the account balance. Western Union transfer details cost 10 per cent of the transfer amount.
Raj Samani and François Paget of McAfee obtained their figures from the going rate on underground cybercime markets, which the two researchers report are stepping further into the background thanks to various law enforcement crackdowns.
“Such underground platforms are implementing stronger mechanisms to ensure that participants are who they purport to be (or at the very least are not law enforcement officials). Ironically, while the platforms that facilitate the services marketplace for illegal activities are going deeper underground, the trade in zero-day vulnerabilities is more transparent than ever before,” Samani and Paget report.
The technical barrier to getting involved in cybercrime has been lowered thanks to various Cybercrime-As-A-Service offerings. These include cybercrime-infrastructure-as-a-service (renting out botnets to send spam), bulletproof hosting, password cracking and DDoS for hire offers.
It also includes Crimeware-As-A-Service, a domain that includes the identification and development of the exploits used for the intended operation (droppers, downloaders, keyloggers, bots, and more). This category includes the availability of hardware that may be used for financial fraud (for example, ATM card skimming kit, the McAfee researchers explain.
Another category highlighted by the McAfee duo – Research-As-A-Service – covers the grey market involving the sale of zero-day vulnerabilities. “The sale of vulnerabilities has recently become a growth area for researchers and brokers alike,” Samani and Paget conclude.
Back in the day high-minded security researchers reported security problems direct to vendors, sometimes getting a less than thankful response in return. These days security researchers in it purely for the money – so-called green hat hackers from the likes of Vupen Security in France and Endgame System in the US – have risen to the fore. Both organisations shun vendors-run programs instead preferring to sell exploits to Western governments. Independent brokers facilitate the same type of legal but ethically questionable trade and the rewards can be high, as the McAfee team report. One broker was reportedly able the broker to facilitate the sale of an Apple iOS exploit for $250,000 and pocket 15 per cent (or $37,500) in commission.
This is right at the elite end of the market. An Adobe Reader exploit, for example, will fetch a far more modest fee of between $5,000 and $30,000. There’s also a market for Java, operating systems and browser exploits. Browser exploits are second only to iOS pwnage tricks, according to figures cited by McAfee, commanding a fee of $60,000 to $150,000 for Firefox or Safari zero-days and perhaps higher for Chrome or Internet Explorer malfeasance.
More details about the exploit vulnerability marketplace, which is legal, together with the changing landscape of the underground economy, can be found found in McAfee’s Cybercrime Exposed whitepaper here (PDF). ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/07/02/mcafee_cybercrime_exposed/