Free whitepaper – What you need to know about cloud backup
Video Whistleblower Edward Snowden, who blew the lid off the US government’s massive internet surveillance project PRISM, has vanished from his Hong Kong hideout.
Word of his disappearance came as it emerged that the 29-year-old’s girlfriend is apparently a pole-dancing blogger who yesterday wrote: “Sometimes life doesn’t afford proper goodbyes.”
Snowden, a former CIA technician, leaked documents about the programme and gave interviews to reporters in a hotel in the Chinese territory – but he disappeared after checking out on Monday. He is thought to still be in Hong Kong, but his exact whereabouts are unknown.
The gutsy whistleblower, who told hacks he now fears for his life, hopes to find sanctuary in Iceland where one member of parliament has already promised to safeguard him – but it is not yet known how he will be able to use the country as a safe bolt-hole.
He chose Hong Kong as a safe haven, but one of its top politicians warned him that it was in his “best interests” to leave Hong Kong because the US has an extradition treaty that could have hauled him back home to face the music.
Regina Ip, chair of Hong Kong’s New People’s Party and former security secretary, warned that the country was “definitely not a safe harbour” for Snowden, which would be “obliged to comply with the terms of the extradition treaty”.
“It’s actually in his best interest to leave Hong Kong,” she said.
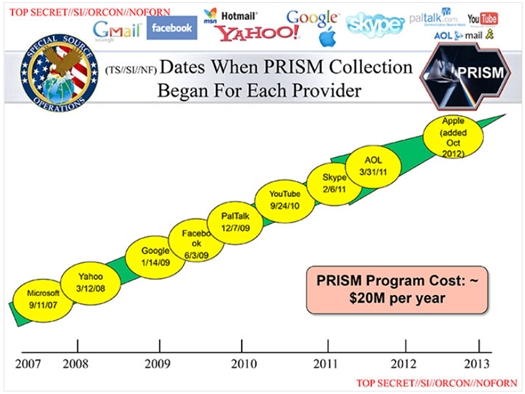
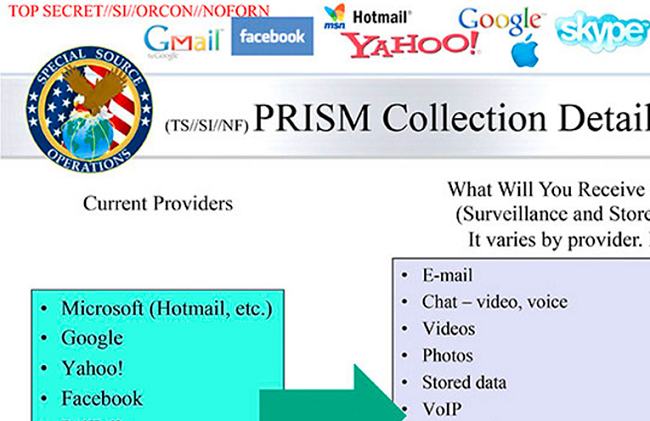
The ex-CIA bod revealed that the NSA’s snooping scheme PRISM allows spooks to request private and sensitive data from internet giants about their users’ online activities – from emails and chat logs to voice call data. America’s spymaster James Clapper has insisted PRISM is only used on foreigners, so that’s all right then.
When Snowden leaked the information to newspapers, he was working in Hawaii for Booz Allen Hamilton, a defence contractor hired for NSA work. Investigators are still scratching their heads about how the $200,000-a-year staffer managed to access information on PRISM: speaking to the Washington Post Joel Brenner, a former NSA inspector general, said a probe into the leak should focus on how the techie “had access to such a startling range of information”.
“The spy you want in an organization may not be the executive assistant to the secretary of state; it may be the guy in the bowels of the IT department because he has system-administrator privileges and because that person is also in a position to insert malware into your system to facilitate remote access,” Brenner added.
Although few details about Snowden’s private life have emerged, journalists have tracked down his parents to Pennsylvania, where they rebuffed questions. A statement from his family is expected to be issued today.
But the most eyebrow-raising glimpse into the life of the ballsy-geek-turned-deep-throat can be found on a blog titled L’s Journey, which is updated by a pole dancer named as Lindsay Mills: the 28-year-old exhibitionist circus performer and erotic dancer is understood to be his girlfriend, and is pictured in various states of undress.
She also describes life in Hawaii in purple prose; documenting the “adventures of a world-traveling, pole-dancing super hero”, it veers between erotica and a confessional diary. The couple have been together since 2009 after meeting in Japan and moved to the US island state together.
Below is a video of Miss Mills in action:
Snowden is not thought to have warned his girlfriend about his PRISM whistleblowing, which appears to have caught her by surprise. Her latest blog post, written on 10 June, stated:
For those of you that know me without my super-hero cape, you can probably understand why I’ll be refraining from blog posts for awhile. My world has opened and closed all at once. Leaving me lost at sea without a compass. Surely there will be villainous pirates, distracting mermaids, and tides of change in this new open water chapter of my journey. But at the moment all I can feel is alone. And for the first time in my life I feel strong enough to be on my own. Though I never imagined my hand would be so forced.
As I type this on my tear-streaked keyboard I’m reflecting on all the faces that have graced my path. The ones I laughed with. The ones I’ve held. The one I’ve grown to love the most. And the ones I never got to bid adieu. But sometimes life doesn’t afford proper goodbyes. In those unsure endings I find my strength, my true friends, and my heart’s song. A song that I thought had all but died away, when really it was softly singing all along. I don’t know what will happen from here. I don’t know how to feel normal. But I do know that I am loved, by myself and those around me. And no matter where my compass-less vessel will take me, that love will keep me buoyant.
For people with little tolerance for wordy bloggerese, there’s also a picture of her in just a bra and knickers while spinning a globe. One of the site’s most popular tags is “rear portaits”, which pulls up similar images.
The bespectacled whistleblower’s girlfriend is now considering closing her blog and social networking accounts after the world’s attention turned her way.
She tweeted:
The blog generally focusses on stories of walking out into the wild and getting naked, or pole dancing with other circus performers.
There is however one depiction of an uncomfortable karaoke night she forced “E” to come along to, in a bid to prove to her friends that her partner actually existed. There is also a description of a fancy-dress party at which the nubile young dancer dressed up as a “super spy”.
While the apparently heartbroken poledancer has little to celebrate, aside from the lucrative book deals and photo-shoot offers that will inevitably come her way, any techie looking for a job in Hawaii has reason to be a bit happier.
Anyone looking for a sysadmin job on the islands is in luck, as Booz Allen are looking to fill a junior role in Honolulu that just opened up.
The job ad said: “Applicants selected will be subject to a security investigation and may need to meet eligibility requirements for access to classified information; Secret clearance is required.
“Integrating the full range of consulting capabilities, Booz Allen is the one firm that helps clients solve their toughest problems, working by their side to help them achieve their missions. Booz Allen is committed to delivering results that endure.” ®
Free whitepaper – Steps to Take Before Choosing a Business Continuity Partner
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/06/11/nsa_surveillance_whistleblower_disappears/