Intelligence files kept hidden for nearly 80 years have shown that the British government was bugging King Edward VIII’s phones in the days leading up to his abdication.

Neil Forbes Grant’s telegram confirming the King’s abdication.
Government officials were clearly panicking about what Edward would do and how the news would be received, so they monitored calls from Buckingham Palace and the King’s Windsor residence Fort Belvedere, as well as stopping telegrams leaking the news of his abdication and intimidating journalists to keep a lid on the news.
The London editor of the Cape Times, Neil Forbes Grant, was dragged in to face Home Secretary Sir John Simon after sending a telegram to South Africa on 6 December, 1936 saying that the King was going to give up the throne. The missive was one of two the General Post Office had intercepted with the leaked news.
Sir John lambasted Grant, reminding him that a false rumour that the country had lost the Battle of Waterloo in 1815 caused a financial crisis and ruined many people, and tried to pressure him to reveal his “highly placed source”.
“I asked him if he did not realise that his responsibilities as a journalist and an Englishman made the sending of such a message without definite authority as to its truth very improper and reckless,” Simon wrote.
Grant refused to give up his source and Simon relented, asking him to keep the interview “absolutely secret and between ourselves”. He also told Grant that there was “no truth” to the abdication rumour.
Edward abdicated at Fort Belvedere four days after Grant sent the telegram.
The papers come from a pile of documents deemed too sensitive and “difficult” to be stored in the classified section of the National Archives. Instead they were kept in a locked vault under the Cabinet Office.
Released through the National Archives, the collection shows the government’s frantic attempts to control the situation as Edward prepared to give up his throne to marry Mrs Wallis Simpson, an American divorcee and socialite. Edward, as head of the Church of England, could not marry Wallis while her former husband still lived – but he refused to give her up. In response, Sir John asked the GPO to monitor the King’s phone calls from 5 December, 1936.
The papers also show that the King himself asked the police to guard Simpson’s residence overlooking Regent’s Park a few months before his abdication. Edward asked Chief Inspector Storries to help make Simpson’s house “burglar proof” and to take steps to stop her from being “annoyed by pressmen, press photographers and other curious persons”. He also asked Storries to keep the instructions to himself.
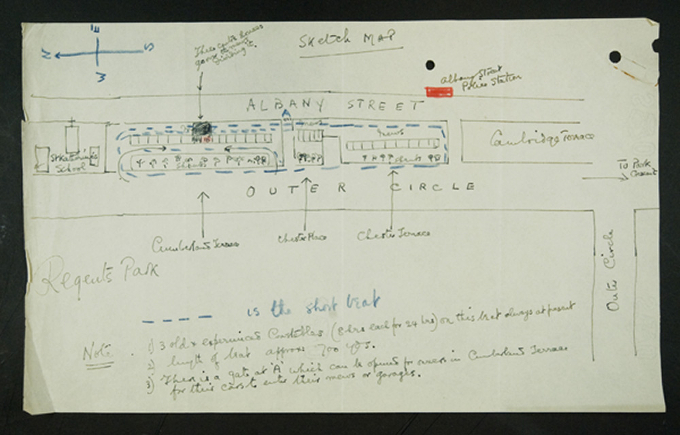
A sketch of Chf Insp Storries’ security arrangements around Wallis Simpson’s house
Among the documents was a handwritten diagram of the stepped-up patrol around Simpson’s house, which police later had to deny the existence of when questioned by American newspapermen.
Other papers released by the Cabinet Office outline a drunken night during Winston Churchill’s August 1942 mission to Moscow and his first face-to-face meeting with Soviet dictator Josef Stalin. Sir Alexander Cadogan, permanent under-secretary at the Foreign Office, was along for the trip and later wrote to Viscount Halifax that things weren’t going that well until Churchill got Stalin alone.
“Nothing can be imagined more awful than a Kremlin banquet, but it has to be endured. Unfortunately, Winston didn’t suffer it gladly. However, next morning, he was determined to fire his last bolt, and asked for a private talk, alone, with Stalin,” he wrote.
At around 1am, Cadogan was called to Stalin’s private rooms and found the war leaders a little worse for wear.
“There I found Winston and Stalin, and Molotov who has joined them, sitting with a heavily-laden board between them: food of all kinds crowned by a sucking [sic] pig, and innumerable bottles,” he said.
“What Stalin made me drink seemed pretty savage: Winston, who by that time was complaining of a slight headache, seemed wisely to be confining himself to a comparatively innocuous effervescent Caucasian red wine. Everyone seemed to be as merry as a marriage bell.
“I think the two great men really made contact and got on terms, Certainly, Winston was impressed and I think that feeling was reciprocated … Anyhow, conditions have been established in which messages exchanged between the two will mean twice as much, or more, than they did before.” ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/05/23/british_government_spied_on_own_king_cabinet_office_papers/


