An anonymous researcher has taken an unorthodox approach to achieve the dream of mapping out the entire remaining IPv4 internet, and has broken enough laws around the world to make them liable for many thousands of years behind bars in doing so, if current sentencing policy prevails.
Getting the sheer numbers of IPv4 addresses involved would take a huge amount of scanners to make billions of pings. While noodling around with an Nmap scripting engine the researcher noticed a lot of virtually unsecured IPv4 devices – only requiring the admin/admin, root/root login, or either admin or root with the password field blank. What if these could be used as a temporary botnet to perform?
“I did not want to ask myself for the rest of my life how much fun it could have been or if the infrastructure I imagined in my head would have worked as expected,” the report “Internet Census 2012” states.
“I saw the chance to really work on an Internet scale, command hundred thousands of devices with a click of my mouse, portscan and map the whole Internet in a way nobody had done before, basically have fun with computers and the Internet in a way very few people ever will.”
The report states a 46 and 60 kb binary was written in C with two parts; a telnet scanner to try the login connection and propagate and then control code to assign scan ranges and feed the results back. A reboot of the infected system would wipe the binary completely and the code didn’t scan traffic running though the device or any intranet-connected systems.
The code was set to run as lowest possible priority in the infected device to avoid interference and included a watchdog to make sure normal operations of the host weren’t overloaded. It also carried a readme file with a description of the project and an email address for the owner, or law enforcement, to get in touch if it was discovered.
After releasing the code overnight the report’s writer found 420,000 suitable botnet endpoints, accounting for around a quarter of the total number of suitable IPv4 systems with enough CPU and RAM and which ran Linux. The botnet was able to spread quickly and efficiently just using the four login combinations and was soon reporting back in healthy numbers.
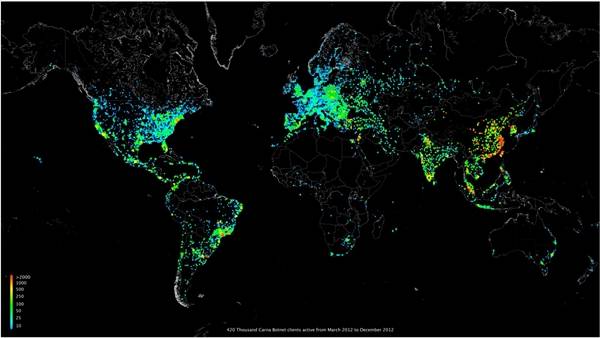
The Carna IPv4 botnet
“While everybody is talking about high class exploits and cyberwar, four simple stupid default telnet passwords can give you access to hundreds of thousands of consumer as well as tens of thousands of industrial devices all over the world,” Mark Bower, VP of product management at Voltage Security told El Reg.
“This is a great study which underlines the fact that once again exploitable weak links are abundant and ripe for compromise, even on embedded or industrial systems. While the researchers merely reported on security gaps, any attacker could quickly access these systems – maybe leading to downstream compromise of something much more valuable.”
The home spy
The vast majority of infected systems were consumer routers or set-top boxes but they also found Cisco and Juniper hardware, x86 equipment with crypto accelerator cards, industrial control systems, and physical door security systems.
“A lot of devices and services we have seen during our research should never be connected to the public Internet at all. As a rule of thumb, if you believe that ‘nobody would connect that to the Internet, really nobody’, there are at least 1000 people who did,” the report states.
“Whenever you think ‘that shouldn’t be on the Internet but will probably be found a few times’ it’s there a few hundred thousand times. Like half a million printers, or a Million Webcams, or devices that have root as a root password.”
The resultant botnet was used to build the botnet the report dubs Carna, named after the Roman goddess of physical health or door hinges, depending on which historical source you believe. But it soon found it was getting competition from a malicious botnet dubbed Aidra and the researcher adapted the binary to block this competitor where possible, but estimates it still has around 30,000 endpoints.
In all the project took nearly six months and the full scan was concluded by October last year. The report estimates that the remaining number of active IPv4 addresses is around 1.3 billion, out a total of around 4.3 billion. The complete scan data, all 9TB or it, is available for download, but not the botnet which created it.
“The actual research itself is noteworthy in that it is the most comprehensive Internet-wide scan. I’d like to see more projects of this kind, conducted legally, and sharing information about the real state of play on the internet,” said Mark Schloesser, security researcher at Rapid7 in an emailed statement.
“While the Internet Census 2012 provides interesting data, the way it was collated is highly illegal in most countries. Using insecure configurations and default passwords to gain access to remote devices and run code on them is unethical, and taking precautions to not interfere with any normal operation of the devices being used doesn’t make it OK,”
He has a point. Monday’s sentence of three years and five months in prison for Andrew Auernheimer, a member of the grey-hat hacking collective Goatse Security, after he used a server vulnerability to expose iPad user accounts is causing great concern to some in the security research industry.
The two situations aren’t exactly the same, but a strict interpretation of the law in both the US and elsewhere would make the Carna botnet used highly illegal and each node could be worth its own charge to an over-zealous prosecutor. No wonder the researcher in question wishes to remain anonymous. ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/03/19/carna_botnet_ipv4_internet_map/
