Adobe investigating attacks on PDFs using zero-day flaw
Vulnerability researchers at FireEye are reporting that Adobe’s Reader software has a zero-day flaw that hackers are already exploiting in the wild.
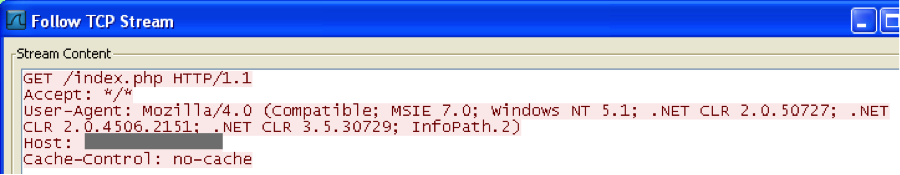
You’ve been pwned (click to enlarge)
The flaw is found in Adobe Reader 9.5.3, 10.1.5, and 11.0.1 and involves sending a specially crafted file to the target. Once opened, the malware installs two DLLs – one that shows an error message and opens a decoy PDF document, and a second that opens a backdoor to allow the code to communicate with a remote server.
“We have already submitted the sample to the Adobe security team. Before we get confirmation from Adobe and a mitigation plan is available, we suggest that you not open any unknown PDF files,” said the FireEye team in a blog post.
Adobe has responded with a brief blog post acknowledging that the problem has been noted and is being investigated further. No doubt its security engineers will be burning the midnight oil to investigate the issue and try and find a workaround or patch.
Those poor devils are having a very busy time of it this month. Last week Adobe rushed out two emergency patches for Flash after attackers started using them in active attacks. But while most people can get by without Flash, PDFs are another matter – by some estimates, Reader is on 90 per cent of PCs in the Western world.
Hackers realize this, of course, and Adobe’s products have been a primary attack vector for years now. And it’s not just Adobe having problems – the popular Foxit PDF reader plugin for web browsers got a zero-day exploit of its own in January that took nearly two weeks to fix. ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/02/14/adobe_reader_flaw_fireeye/