Apple, Google tumble off top 20 trusted companies list
Once ranked as high as number eight among companies most trusted for protecting their customers’ privacy and personal information, Apple has fallen out of the top 20 entirely. Google didn’t make this year’s list, either, but it fell only from its pervious high of 13th place.
The list in question was compiled by the Ponemon Institute, an independent research group focused on privacy, data protection, and information security policy, and published in a new report entitled, logically enough, “2012 Most Trusted Companies for Privacy”.
As they have for the past seven years, the Ponemon researchers contacted over 100,000 adults and asked them – among other things – to name the companies they most trusted to protect the privacy of their personal information. Out of that large sample, the researchers derived 6,704 usable responses that provided a total of 39,890 positive and negative company ratings.
Survey responders named American Express as the company most trusted to protect their personal information, an honor the company has received each year since 2007, when eBay lost the top spot. HP came in second, with Amazon, IBM, and the US Postal Service rounding out the top five; eBay has slipped down to number nine.
Apple and Google didn’t fare as well this year as they have in the past. Neither made it into the top 20, although Google had been so honored in four of the past seven years, and Apple had been named among the 20 most-trusted in 2009, 2010, and 2011.
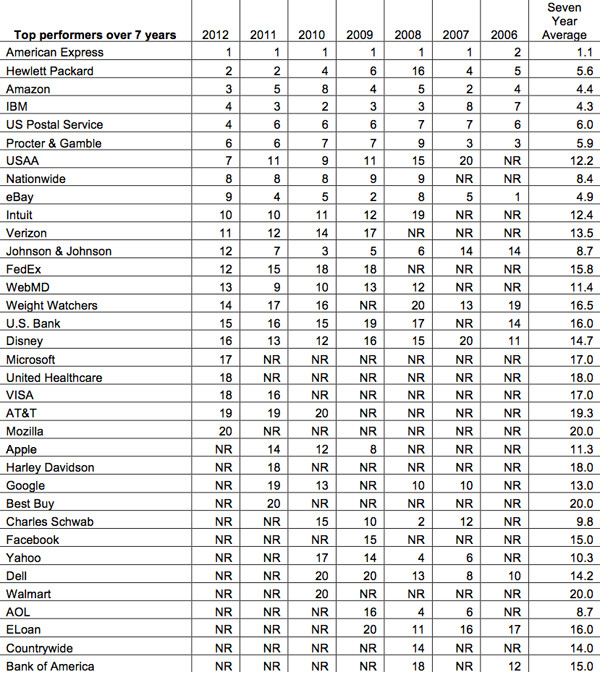
Apple, Google, Facebook, and other tech companies are less trusted than even ATT (source: the Ponemon Institute)
Facebook missed the cut as well – the social-media juggernaut has only made the annual Ponemon Institute list once, at number 15 in 2009. Other tech companies that were once in the top 20 but are now on the outs include Yahoo!, Dell, and AOL.
The report contains quite a bit more information, as well, and is worth a quick read if you care about such things. One particular bit of data caught our eye: respondents are increasingly pessimistic about the control they feel they have over their personal information, and at the same time they report a greater sense of the importance of that information.
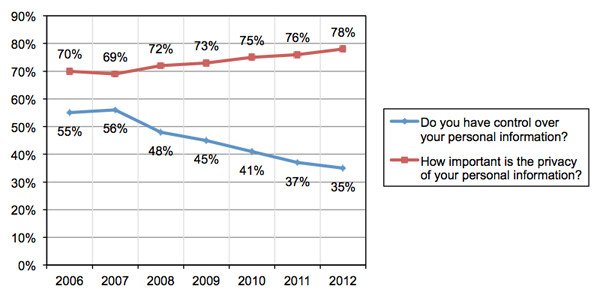
These trends would seem to indicate that a comprehensive privacy solution might be in order (source: the Ponemon Institute)
One final nugget: of the 25 industries that the Ponemon Institute tracks, the one least trusted to protect the privacy of your personal information is Internet and Social Media (excluding eCommerce), with Mozilla being the most trusted company in that mistrusted sector.
Right above the much-maligned internet, slotting in at 24th place among industry groups in trustability, is the non-profit sector. The most trusted non-profit organization? The National Rifle Association (NRA). ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/01/30/top_20_companies_trusted_to_protect_personal_information/