Exclusive A security flaw accessible via Google’s UK motor insurance aggregator Google Compare has potentially exposed vast numbers of drivers to identity theft.
The vulnerability, the existence of which has been verified by The Register, made it possible for comprehensive personal details – including names, addresses, phone numbers and job – to be harvested at will.
Information about the flaw was passed to The Register last week by a source who wishes to remain anonymous, but who is familiar with motor insurance aggregation systems. The data could be accessed via a simple edit of a motor insurance proposal form. The Register created a fictitious motorist for this purpose, and completed an online proposal form using Google Compare.
Google Compare sends this form to numerous underwriters – there can be at least 100 of these – and then Google offers you details of the companies that wish to offer a quote, together with their prices.
Some of these companies’ quotes, however, can be illicitly accessed. After we had made a simple edit to a vulnerable document, we were no longer viewing our own proposal form, but those of unrelated individuals.
When the edited document was passed to the vulnerable system, an entirely different proposal – often from an entirely unrelated underwriter – was displayed. Essentially, once a criminal has a form fielded by the vulnerable system, he could repeatedly edit the form in order to obtain complete details of a new person every time. The process would not be difficult to automate.
Nor does it appear that all of these people applied for insurance via Google Compare, because some of the forms we viewed were apparently quotes from other insurance comparison sites.
The problem was potentially vast. The Register understands that the flaw lies in third-party software external to Google Compare, operated by insurance and financial specialist SSP. But although Google’s own in-house systems were not directly compromised, the SSP system effectively allows criminals to operate Google Compare as a massive identity theft portal.
Our source claimed the SSP system is used by about 20 per cent of motor insurance brokers working with Google Compare, but that “quotes from near enough all car insurance comparison sites in the UK go through this system, so you will find all Google Compare’s customers in there, and other comparison sites’ customers also”.

“Your quote from Go Compare…” You were sitting down, weren’t you?
The quote above, accessed using the Google Compare flaw, appears to have been offered via Go Compare, not the spookily similarly named Google Compare.
The SSP system appears to act as a host for quote forms from a range of brokers and aggregators. Aside from this system’s ability to leak unrelated forms, Google’s own security could be viewed as overly lax.
“Some other aggregators do a server-side redirect,” says our source. “Other aggregators do not send the real contact details. It’s Google that chooses to send to this system.”
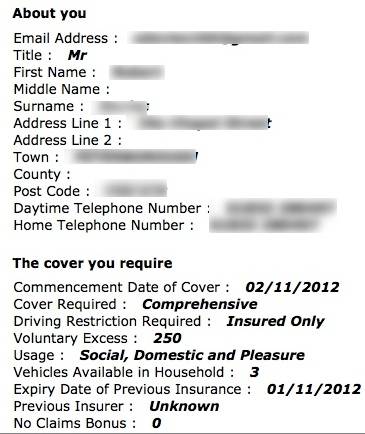
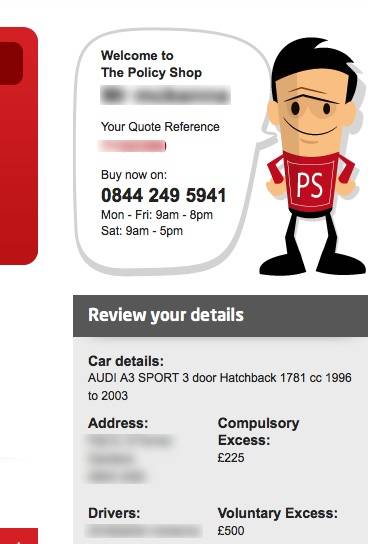
Your personal details, leaked by the vulnerable web system, and another quote inappropriately accessed
After verifying the existence of the flaw, The Register notified the Information Commissioner’s Office (ICO) and Google, informing the latter of our intention to publish this story.
Within hours of being notified, a Google spokesman told us it had suspended insurers using SSP software from its comparison site – meaning the flaw can no longer be exploited via Google Compare.
Google also sent us a statement:
As soon as we became aware of this problem, which occurs on certain broker websites that use SSP software, we suspended those brokers. We have raised this issue with SSP and have asked them to address it immediately.
The ICO responded that it will begin enquiries before deciding what action, if any, was required.
We asked Google if it will report itself to the ICO. The company responded that it was SSP and the insurance brokers who had suffered a data breach, not Google. The search giant argued that the same problem exists with all aggregator sites, and said “we didn’t hold contracts with SSP – SSP holds contracts with those brokers” and “we’re not responsible for content”.
Which is a similar argument to the one Google uses regarding other media it links to. Essentially, the company believes it has no legal responsibility for what happens to the user after they’ve clicked on a link. And yet Google Compare undoubtedly collected personal data at the form-filling stage and passed it on to a third party whose software appears to be insecure. According to Google, that’s not its fault.
The Register contacted SSP, and will update our readers when we have received a response.
Although Google insists this isn’t its problem, and the same bug exists in other motor insurance aggregators, The Register has been unable to verify this. A check of Go Compare, for example, confirmed that the site does link to brokers using SSP software, but it does not seem to be possible to manipulate the quote proposal document in the same way that was, until yesterday, possible with Google Compare.
The Register’s source said it is likely some aggregators are indeed vulnerable to the flaw, but that others were already aware of it and had taken steps to stop it being exploited via their websites.
It seems there are two important aspects to the security bug: First, the way SSP’s software handles document storage and retrieval, and second, the security of the identification process. The flaw in the latter lay somewhere on the road from Google to SSP to broker – but that’s one for the ICO to figure out. ®
Bootnote
Many years ago, your writer worked for Insurance Age, The Review, Worldwide Reinsurance and Marine Insurance Bulletin. In those days they didn’t have computers … as such. El Reg has intentionally withheld precise details of the flaw at this stage in the interests of responsible disclosure.
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2012/11/08/google_compare_identity_theft/


