Middle Eastern Gauss malware could be state sponsored
Security firms are investigating what looks to be another piece of state-sponsored malware, which has been targeting banks in the Middle East and distributing an unknown payload.
Dubbed Gauss by Kaspersky Labs, the malware first seemed to be a module of the highly sophisticated Flame virus but has now been recognized as a separate entity. It was first detected in September 2011 and over 2,500 infections have been found on Kaspersky’s cloud network.
“Gauss was created by the same ‘factory’ which produced Flame. This indicates it is most likely a nation-state sponsored operation,” Kaspersky’s report on the malware states.
Gauss is designed to infect Windows systems and harvests browsing information and payment logins via PayPal, Citibank and a number of Lebanese operations such as the Bank of Beirut and Fransabank.
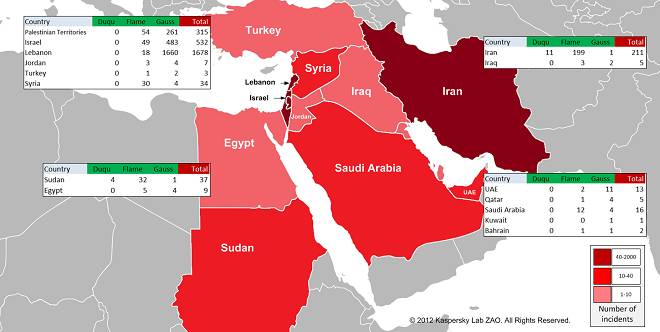
The infection pattern is curiously localized. The vast majority of infections are in Lebanon, with Israeli and Palestinian computers making up the bulk of other victims, plus a smattering of appearances in other Middle Eastern countries.
Gauss infections are curiously localized (click to enlarge)
It also has a separate encrypted payload in the malware which is installed on any USB drives put in a Gauss-infected machine. When the drive is used in an uninfected PC, the malware scans the new system’s configuration for data such as its OS, network shares, proxy data, and URL history, and then matches that against a known configuration stored in the malware code. If there is no match then the malware deletes itself to avoid detection.
“The payload is run by infected USB sticks and is designed to surgically target a certain system (or systems) which have a specific program installed. One can only speculate on the purpose of this mysterious payload,” said Kaspersky, after its experts were unable to break the encryption.
In all, the malware installs up to eight separate modules, depending on the machine it infects. These harvest CMOS and BIOS data, network interfaces, domains, and drives, in addition to installing plugins that monitor browser history and collect passwords. Other modules cover malware transmission and control, as well as installing other software whose purpose is, at present, unknown.
Kaspersky don’t think that the purpose of Gauss is to steal cash, but rather to record and track individual computers and bank accounts. The theft angle would be incompatible with a nation-state attack, the company suggests, and it looks as though data collection was the motivation of its authors.
The Russian firm identified five command and control servers for Gauss, all running Debian Linux and listening on ports 22, 80, and 443 (as with Flame) but on July 13 they were taken offline. Purloined data was sent to seven domains and the load balancing systems used indicate high levels of traffic.
Kaspersky has now put out a signature file for Gauss and the boffins at Hungarian research lab CrySyS have come up with an online detection tool to find new infections. As part of its payload, Gauss installs a new font, Palida Narrow, and the tool checks to see if this is installed as an indicator of infection.
The nature of the malware, and its choice of targets, will stoke fears that Gauss is another manifestation of Project Olympic Games, the claimed US/Israeli project to militarize code. The use of such software was dubbed a “moral crime” at last month’s Black Hat conference and has many in the industry worried about the security ramifications for businesses caught in the crossfire. ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2012/08/10/gauss_middle_east_malware/