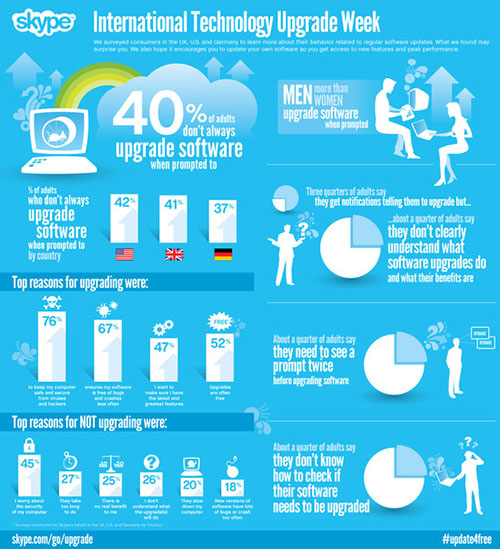
A new survey commissioned by Skype reveals that 40 per cent of adults do not always update their software when prompted to do so, and that 25 per cent skip software updates because they think they offer no real benefit.
The survey was offered on Skype’s behalf to some 350,000 individuals in the US, UK, and Germany by internet pollster YouGov.
A quarter of the adults surveyed said they did not understand the benefits of software updates or what they were supposed to do.
About the same number said they didn’t know how to check for updates, and another quarter said they’d need to be prompted to upgrade their software at least twice before they would do it.
The respondents gave various reasons for shying away from updates. Some said they expected new versions of software would have “lots of bugs” or would crash too often, while others said they thought the updates would slow down their computers.
More than a quarter of respondents said the process of updating their software just takes too long.
Software updates: Don’t get ’em, don’t want ’em, can’t be bothered. (Source: Skype)
The most jaw-dropping result, however, was that 45 per cent of survey participants said they did not upgrade their software – paradoxically – because they worry about the security of their computers.
The survey results highlight the often-contentious issue of security updates for consumer software. Former Mozilla staffer Jonathan DiCarlo ignited a minor internet firestorm in early July when he spelled out the issue in a blog post:
Only after I heard from dozens of different users that the rapid release process had ruined Firefox did I finally get it through my thick skull: releasing an update is practically an act of aggression against your users. The developer perspective is “You guys are going to love this new update we’ve been working on!” The user perspective is “Oh god here comes another update, is there any way I can postpone the agony for a few more days?”
Thankfully, the Skype survey participants who replied that they did regularly update their software said they did so for sensible reasons. Of them, 76 per cent responded that they updated their software “to keep my computer safe and secure from viruses and hackers.”
Other popular reasons for upgrading were to keeping computers free of bugs so that they crash less often, and gaining the latest features.
About half of the respondents said they installed the updates because, hey, they don’t cost anything.
Skype commissioned its survey in preparation for a weeklong event it’s calling International Technology Upgrade Week (ITUW), a global effort to raise consumer awareness about the importance of software updates, which kicks off on Monday.
Joining Skype in promoting the ITUW effort are Adobe, Norton, and TomTom.
“We hear you – loud and clear,” writes Adobe’s Wiebke Lips in a statement. “The good news is that times have changed. Especially for consumers, software updates have become much easier and much more reliable than they once were. Software vendors continuously look for ways to make the update process less cumbersome.”
The companies may have a hard time convincing some customers, however. Consider the recent Symantec security update that triggered widespread reports of crashing PCs in July. (Symantec is the parent company of Norton, one of the sponsors of ITUW.) And then there was the Windows update earlier that same month that silently installed Skype onto business PCs without asking.
It appears that for all the good that the sponsors of IUTW hope to do with their campaign, a little “physician, heal thyself” may yet be in order. ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2012/07/23/skype_software_update_survey/